This guide applies to Mac computers
Configure EAP-TLS
EAP-TLS uses Transport Layer Security and an identity certificate to authenticate devices to the network.Configure TLS Version Settings
To prevent using older and weaker TLS versions, select the TLS minimum version you would like to allow. If your infrastructure does not support the latest versions of TLS, select the TLS maximum version you want to use.
Configure Identity Certificate
Select a method to provide an identity certificate and configure applicable settings. See Configure the Wi-Fi Library Item to learn more.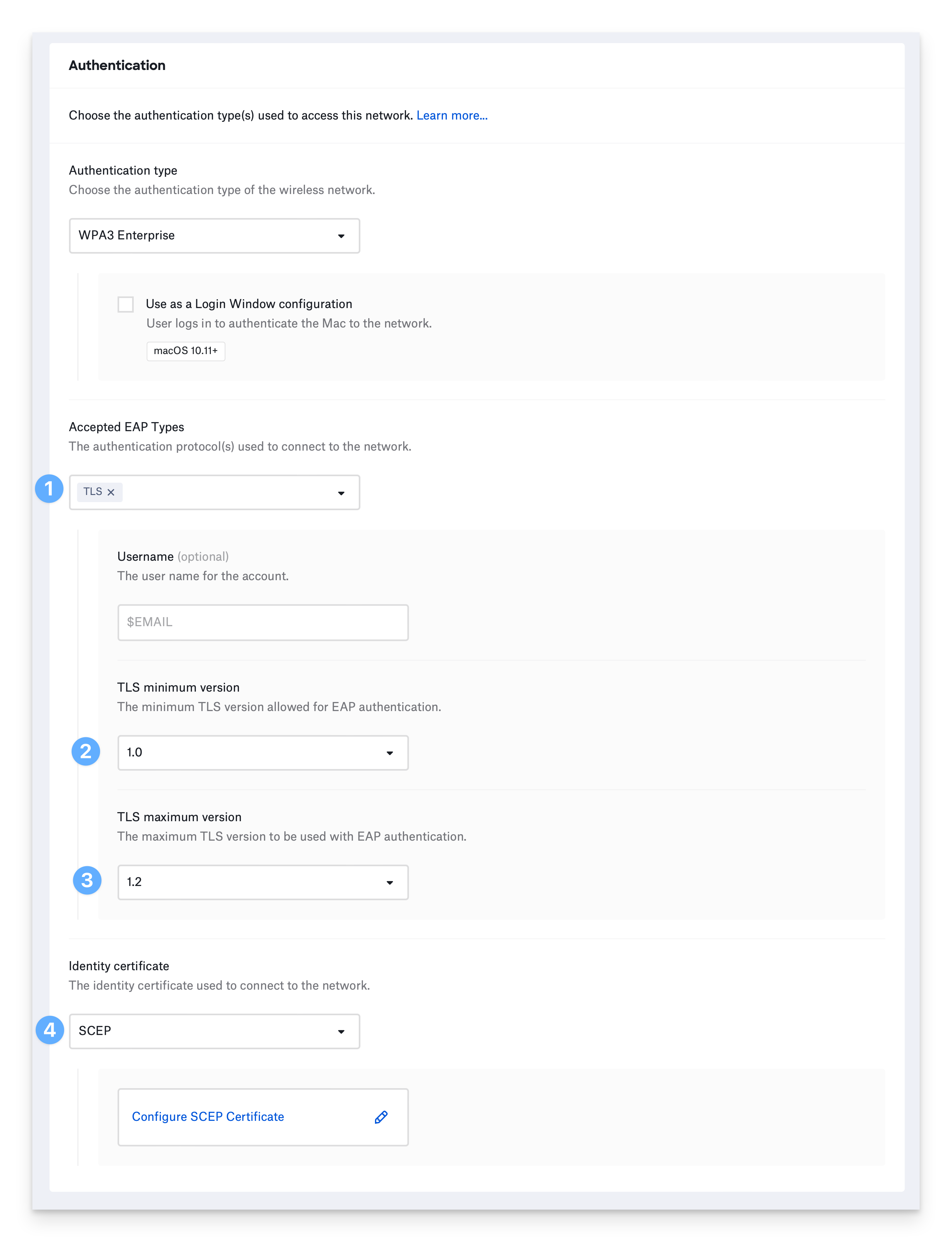

Configure EAP-TTLS
Tunneled Transport Layer Security uses a TLS tunnel to encrypt another authentication protocol. It does not require an identity certificate. Devices can use a username and password or device-based directory credentials to authenticate. Username and password authentication:Configure Username
Optionally, provide the Username. You can use a static value or one of Iru Endpoint’s global variables, such as $EMAIL. If you do not enter a username, the device prompts the user to enter one when connecting to the network.
Set Password Prompt Frequency
Select how often to prompt the user for their password. If you choose Once and don’t provide a password, the device will prompt the user once for their password and remember it. If you select, Every time the user connects to the network, the device will not remember the password.
Configure the remaining TTLS settings:
Configure TTLS authentication
When you select TTLS, your device will use a username and password or device directory credentials for authentication. If your network requires an identity certificate as a second authentication factor, select Require Two-Factor Authentication.
Set inner authentication
For Inner authentication, choose the authentication protocol to use inside the TLS tunnel.
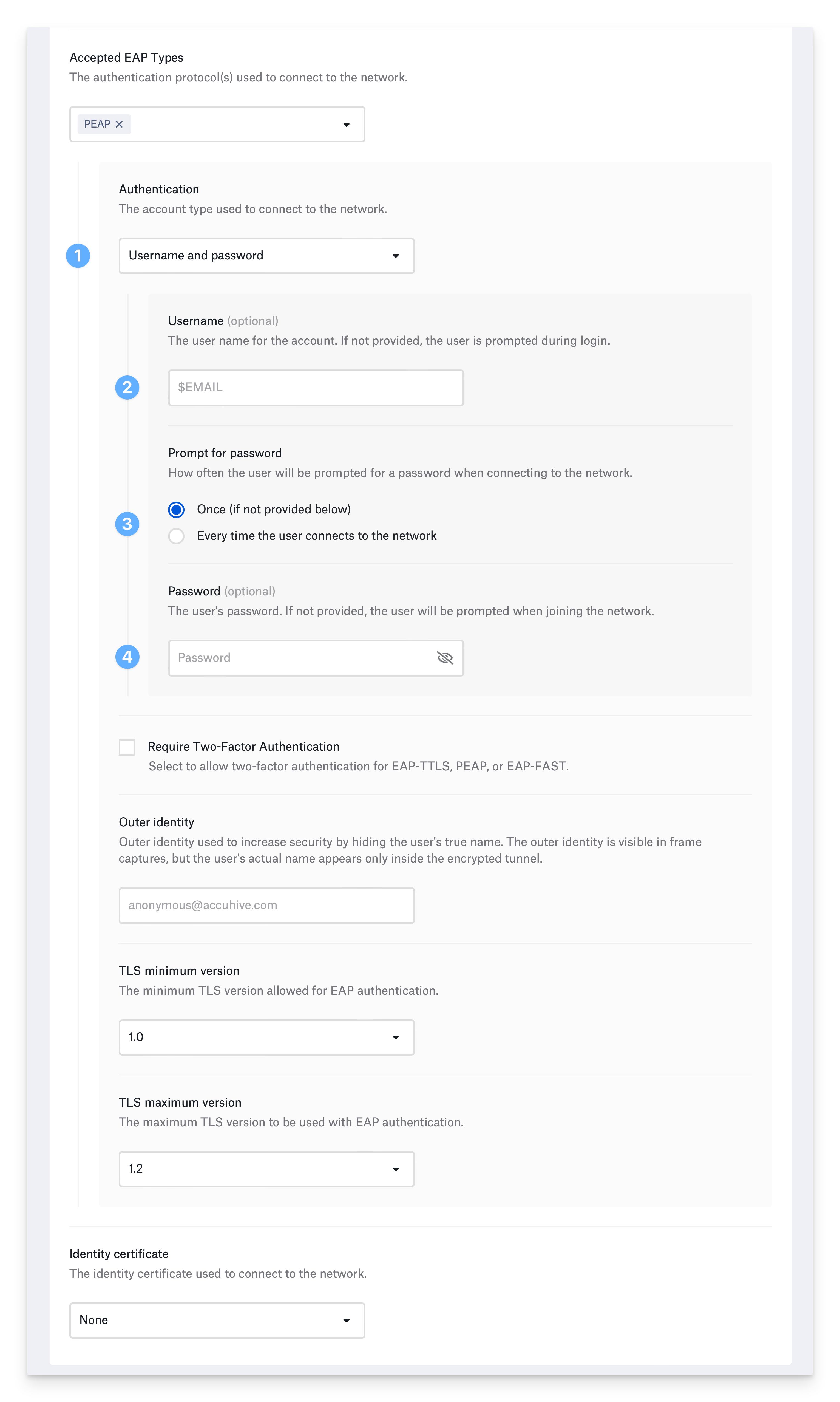
Specify outer identity (optional)
Optionally specify Outer identity. It is different from the identity used inside the tunnel and is specified to prevent exposing the inner identity.
Set TLS minimum version
To prevent using older and weaker TLS versions, select the TLS minimum version you would like to allow
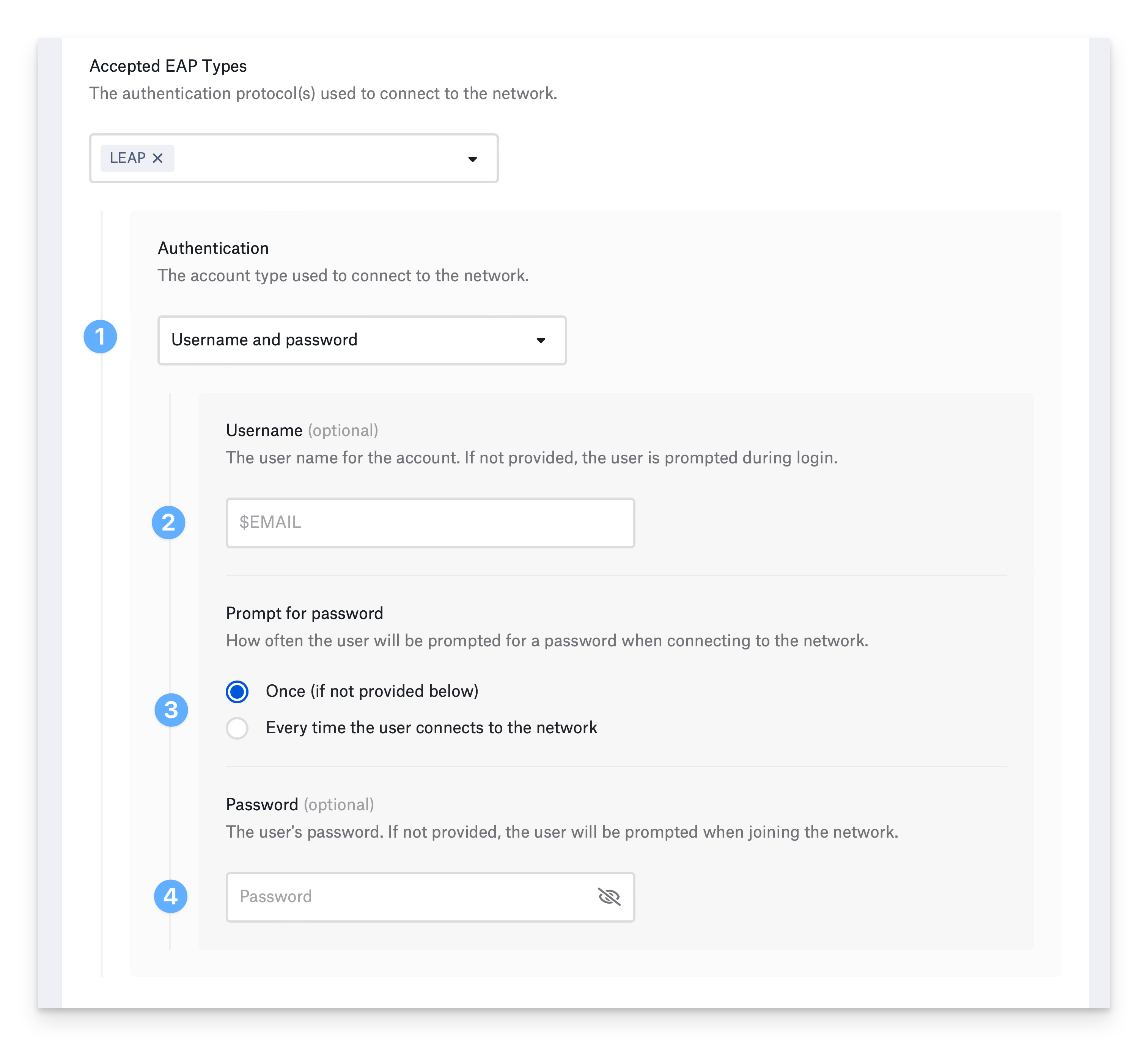
Configure EAP-LEAP
Lightweight Extensible Authentication Protocol is an older authentication method based onMS-CHAP and Dynamic WEP. It does not use an identity certificate. Devices can use a username and password or device-based directory credentials to authenticate. Username and password authentication:Configure username (optional)
Optionally, provide the Username. You can use a static value or one of Kandji’s global variables, such as $EMAIL. If you do not enter a username, the device prompts the user to enter one when connecting to the network.
Set password prompt frequency
Select how often to prompt the user for their password. If you choose Once and don’t provide a password, the device will prompt the user once for their password and remember it. If you select Every time the user connects to the network, the device will not remember the password.
Configure EAP-PEAP
Protected Extensible Authentication Protocol addresses shortcomings of previous Extensible Authentication Protocols such as LEAP. Like EAP-TTLS, PEAP uses a TLS tunnel to encrypt another authentication protocol. It does not require an identity certificate. Devices can use a username and password or device-based directory credentials to authenticate. Username and password authentication:Configure username (optional)
Optionally, provide the Username. You can use a static value or one of Kandji’s global variables. For example, $EMAIL. If you do not enter a username, the device prompts the user to enter one when connecting to the network.
Set password prompt frequency
Select how often to prompt the user for their password. If you choose Once and don’t provide a password, the device will prompt the user once for their password and remember it. If you select, Every time the user connects to the network, the device will not remember the password.
Configure the remaining PEAP settings:
Configure PEAP authentication
When you select PEAP, your device will use a username and password or device directory credentials for authentication. If your network requires an identity certificate as a second authentication factor, select Require Two-Factor Authentication.
Set TLS minimum version
To prevent using older and weaker TLS versions, select the TLS minimum version you would like to allow.
Set TLS maximum version
If your infrastructure does not support the latest versions of TLS, select the TLS maximum version you want to use.
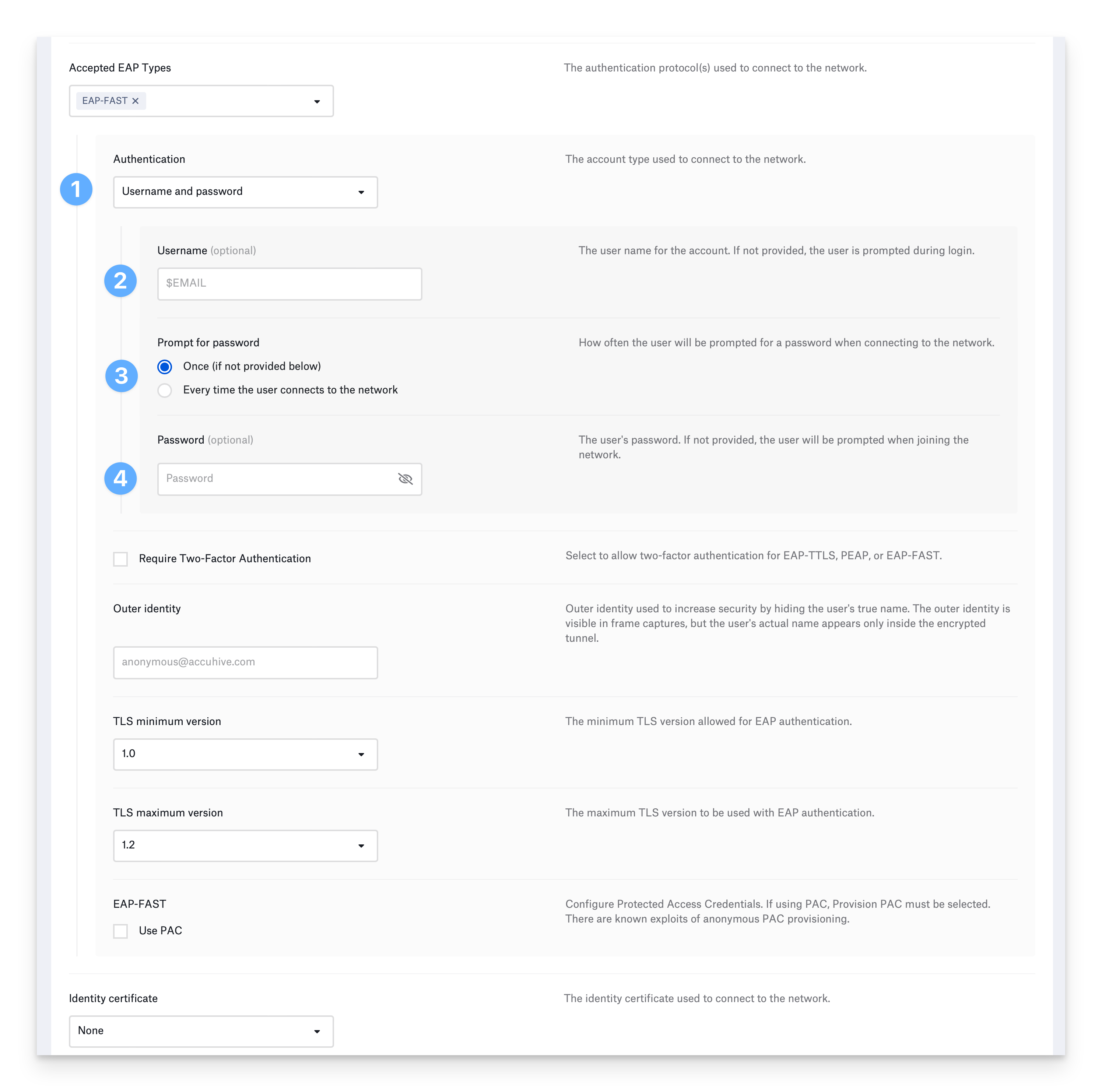
Configure EAP-FAST
Flexible Authentication via Secure Tunneling (FAST) uses a TLS tunnel to encrypt additional authentication information. FAST also supports fast re-establishment of the tunnel through Protected Access Credentials (PAC). It does not require an identity certificate. A username and password or device-based directory credentials can provide authentication. Username and password authentication:Configure username (optional)
Optionally, provide the Username. You can use a static value or one of Kandji’s global variables. For example, $EMAIL. If you do not enter a username, the device prompts the user to enter one when connecting to the network.
Set password prompt frequency
Select how often to prompt the user for their password. If you choose Once and don’t provide a password, the device will prompt the user once for their password and remember it. If you select, Every time the user connects to the network, the device will not remember the password.
Configure the remaining EAP-FAST settings:
Configure EAP-FAST authentication
When you select EAP-FAST, your device will use a username and password or device directory credentials for authentication. If your network requires an identity certificate as a second authentication factor, select Require Two-Factor Authentication.
Specify outer identity (optional)
Optionally specify Outer identity. It is different from the identity used inside the tunnel and is specified to prevent exposing the inner identity.
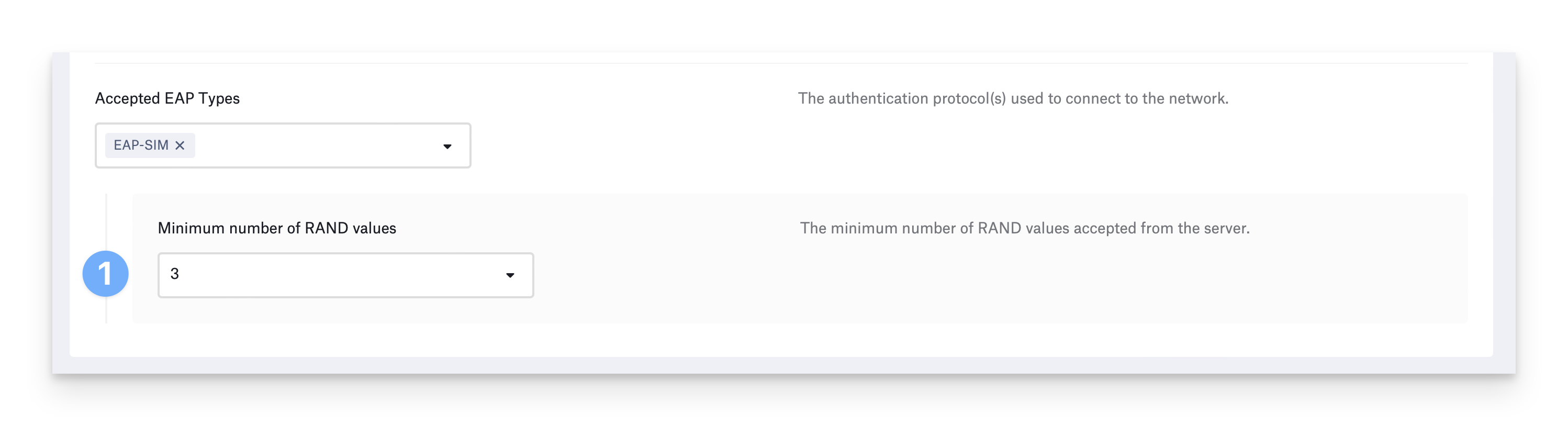
Configure EAP-SIM
This authentication method is compatible with the Wi-Fi Library Item only.
Configure EAP-AKA
This authentication method is compatible with the Wi-Fi Library Item only.







.png?fit=max&auto=format&n=TTV4GXkIHgRpdDZ5&q=85&s=67480d44c947ee458a01e5d3926ca780)