This Library Item is available for Apple devices
What is 802.1X Authentication?
802.1X is a standard for controlling access to a network. It ensures that only authorized devices can connect, making your network more secure. This protocol is used in both wired (ethernet) and wireless networks.How 802.1X Authentication Works
There are three main parts involved in 802.1X authentication:- Supplicant -This is the device (like your user’s Mac) that wants to join the network. It provides credentials to the authenticator.
- Authenticator - This is a network device, such as a switch or access point, that controls access to the network. It checks the credentials and decides whether to allow the device to connect.
- Authentication Server -Usually a RADIUS server, it verifies the credentials provided by the supplicant and tells the authenticator whether to grant access.
Add an Ethernet Library Item
To add this Library Item to your Iru Endpoint Library, follow the steps outlined in the Library Overview article.Assign to Blueprints
Assign to your desired Blueprints.
Configure Authentication Settings
Use as Login Window Configuration
Using this configuration requires integration with a directory service. See this Apple support article for more information.
Accepted EAP Types
Select the Accepted EAP Types your network supports. You may select more than one and must set all the settings necessary for the selected EAP types. For more information on configuring specific EAP types, refer to our Configuring EAP (Extensible Authentication Protocol) Types support article.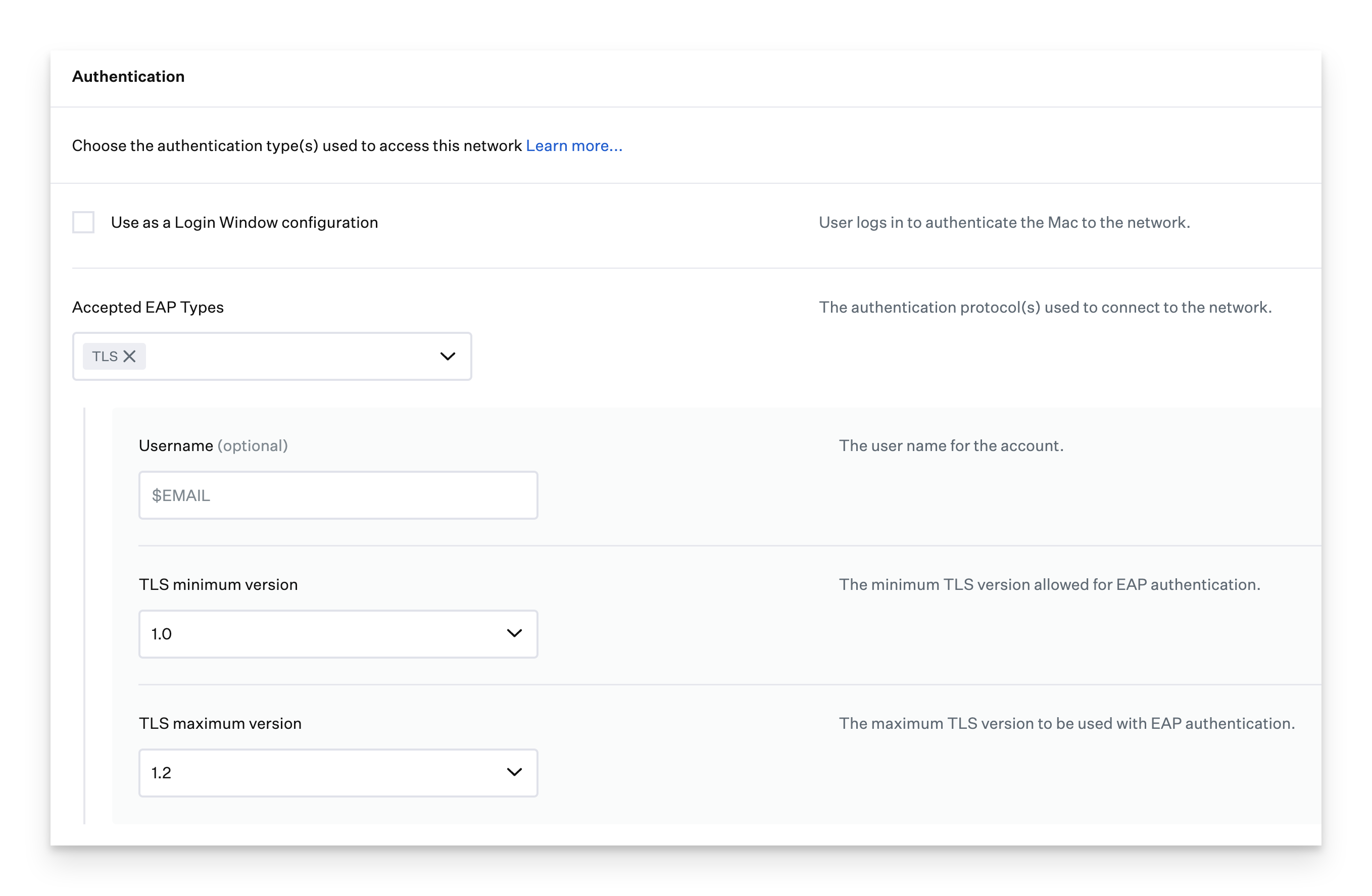
Configure an Identity Certificate
You can configure an identity certificate using SCEP or by uploading a PKCS #12 file. For instructions on configuring identity certificates, see our Using Identity Certificates for 802.1X Authentication support article.Configure SCEP
When utilizing SCEP for identity certificates, ensure that SCEP is deployed inside the Ethernet Library Item, not as a separate SCEP Library Item.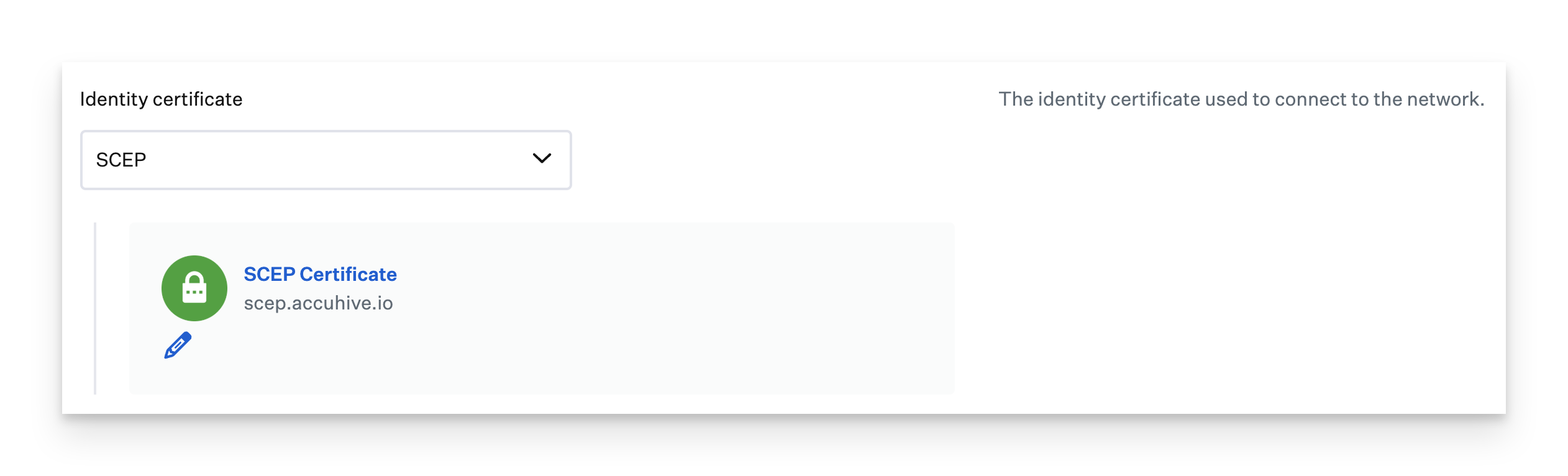
Configure Certificate Trust Settings
Install the trusted certificate chain for your RADIUS server(s) using a separate Certificates Library item. Then, specify the names of those certificates in the Ethernet Library item under Specify server certificate names. For more information, see Apple’s guide, Connect Apple devices to 802.1X networks. Most enterprise environments require that devices trust the 802.1X authentication server(s), typically a Remote Access Dial-In User Server (RADIUS). The Certificate trust settings allow you to configure which certificates presented by the server devices will trust. If a device does not trust the authentication server(s), the user will be prompted to trust it.Specify trusted certificates (optional)
Select Specify trusted certificates if you want to provide certificates for the configured devices to trust. Then upload the certificates in .cer or .crt format.
Specify server certificate names (optional)
Select Specify server certificate names if you want to provide DNS names of certificates devices should trust. Then enter their DNS names — wildcards are accepted.
Configure Proxy Settings
Configure devices to use a network proxy by configuring the settings in the Proxy section.Configure Automatic proxy
To configure devices to use a Proxy Auto-Configuration (PAC) file, select Automatic for Proxy type.
- Specify the Proxy PAC URL where devices can find the PAC file.
- If you want devices to attempt to connect directly to destinations when the PAC file is not available, select Proxy PAC fallback allowed.





