About OneLogin SAML Integration
Single Sign-On with OneLogin (SAML) in Iru Endpoint lets you set up SAML-based SSO integration with OneLogin for users accessing Iru Endpoint through their OneLogin credentials.How It Works
OneLogin SAML integration lets users authenticate to Iru Endpoint using their existing OneLogin credentials. Once configured, users can access Iru Endpoint through a single sign-on experience. The integration works by establishing a trusted relationship between Iru Endpoint and OneLogin, where OneLogin acts as the identity provider (IdP) and Iru Endpoint acts as the service provider (SP). When users attempt to access Iru Endpoint, they’re redirected to OneLogin for authentication, and upon successful login, OneLogin sends a SAML assertion back to Iru Endpoint confirming the user’s identity. SSO can be used for Iru Endpoint Web App sign-in and for Require Authentication with Automated Device Enrollment.- Iru Web App Configuration
- OneLogin Configuration
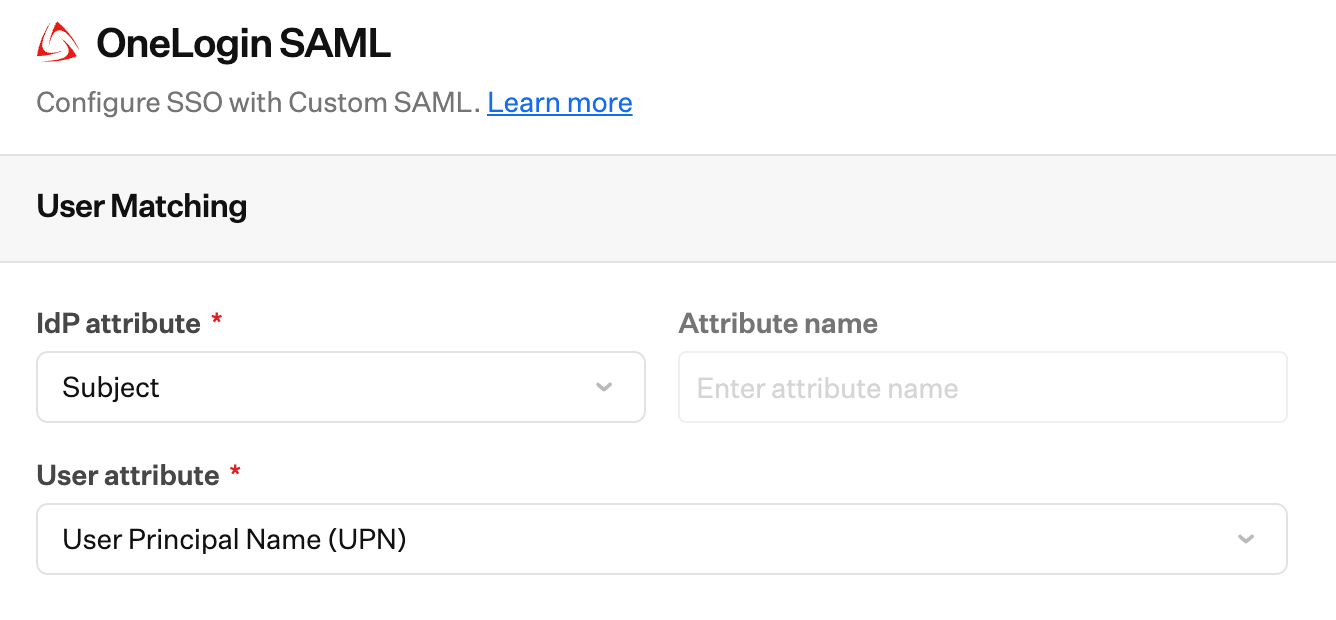
Setting Up the SAML Connection
You’ll need to complete the initial setup in Iru Endpoint first to get the configuration information required for OneLogin. After copying the Entity ID and ACS URL, switch to the OneLogin Configuration tab to continue.
Select Admin and Authentication
Select the Admin and authentication tab (selected by default) and scroll down to Authentication methods.
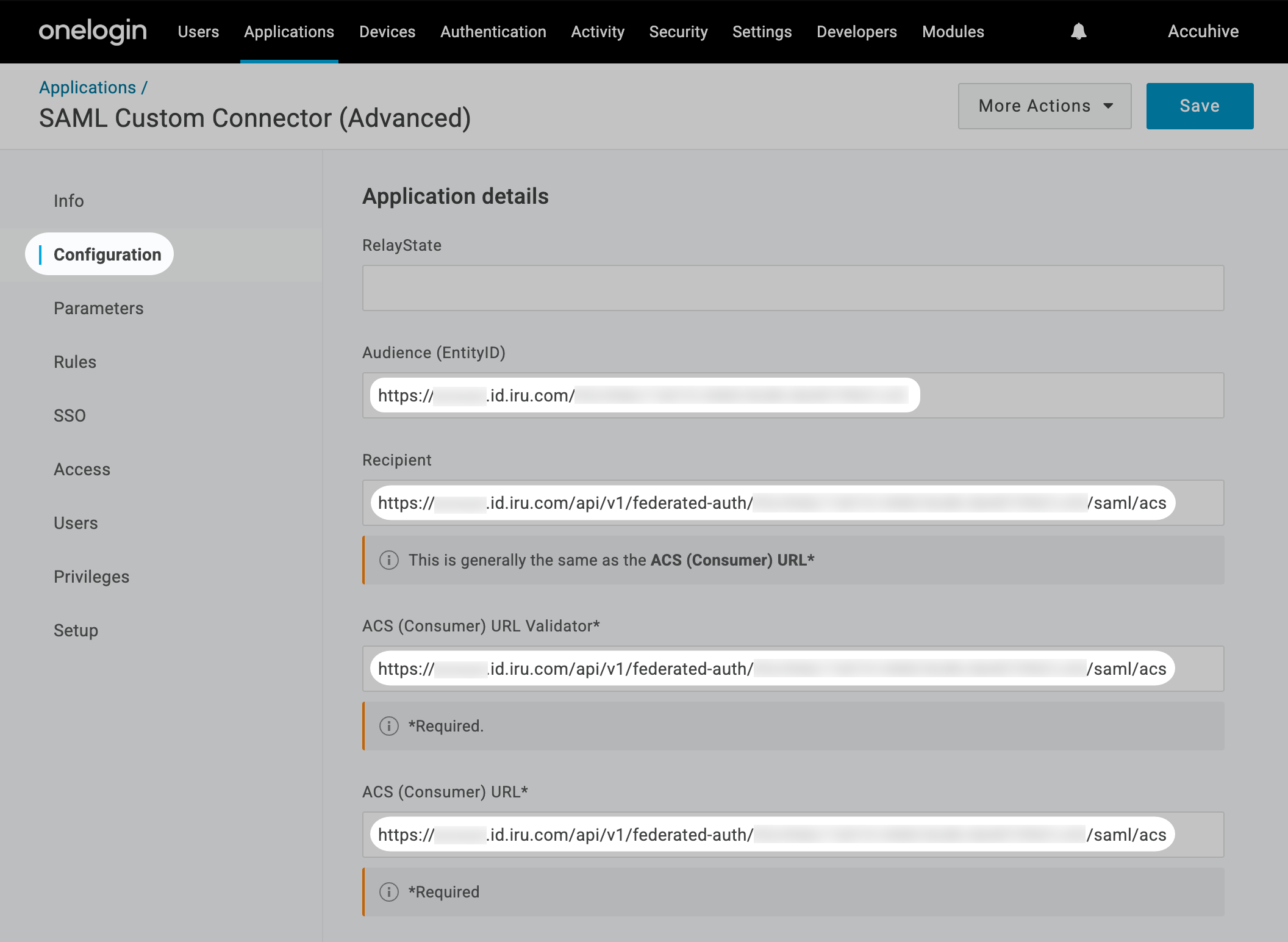
Copy Service Provider Entity ID
Copy the Service provider entity ID into a text document for later use. You’ll need this for the OneLogin configuration.
Copy ACS URL
Copy the Assertion consumer service (ACS) URL into a text document for later use. You’ll need this for the OneLogin configuration.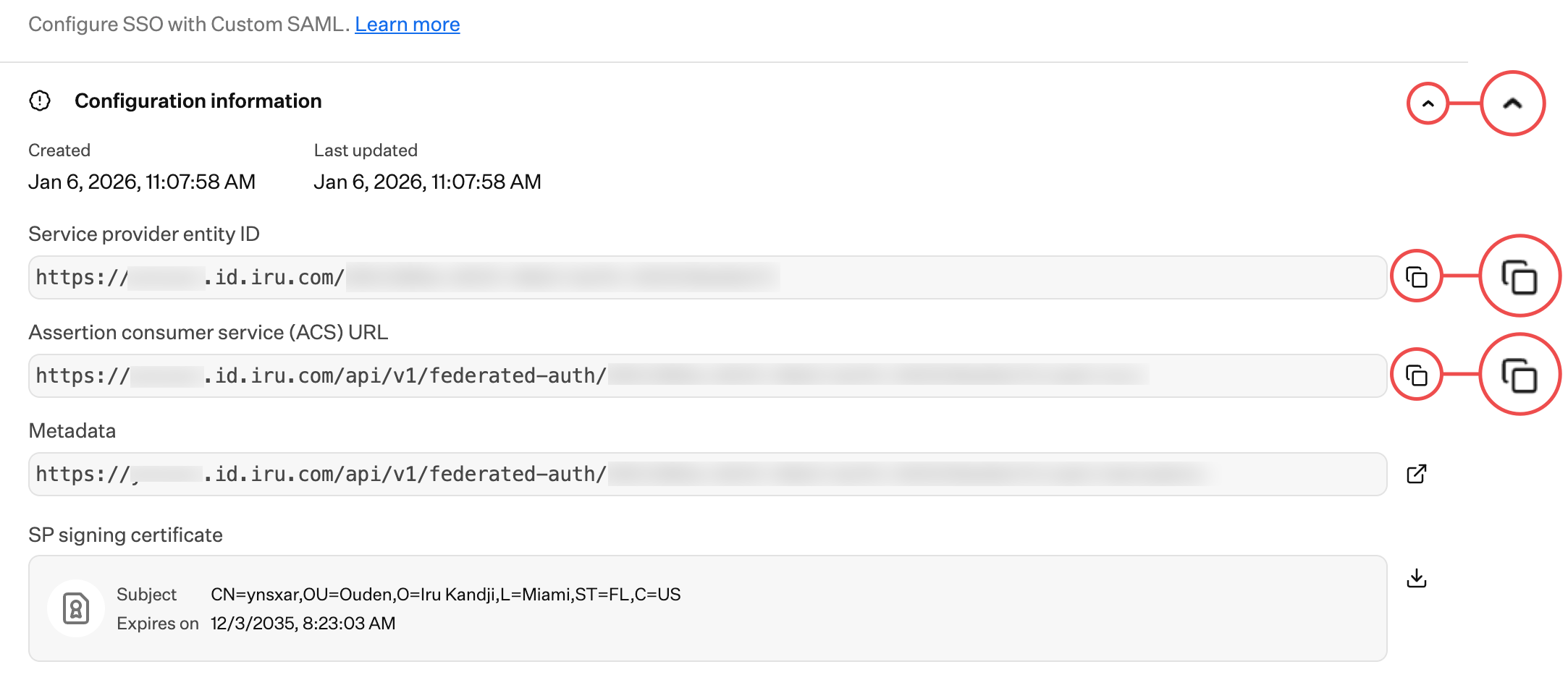

Configuring Iru Endpoint SAML Connection
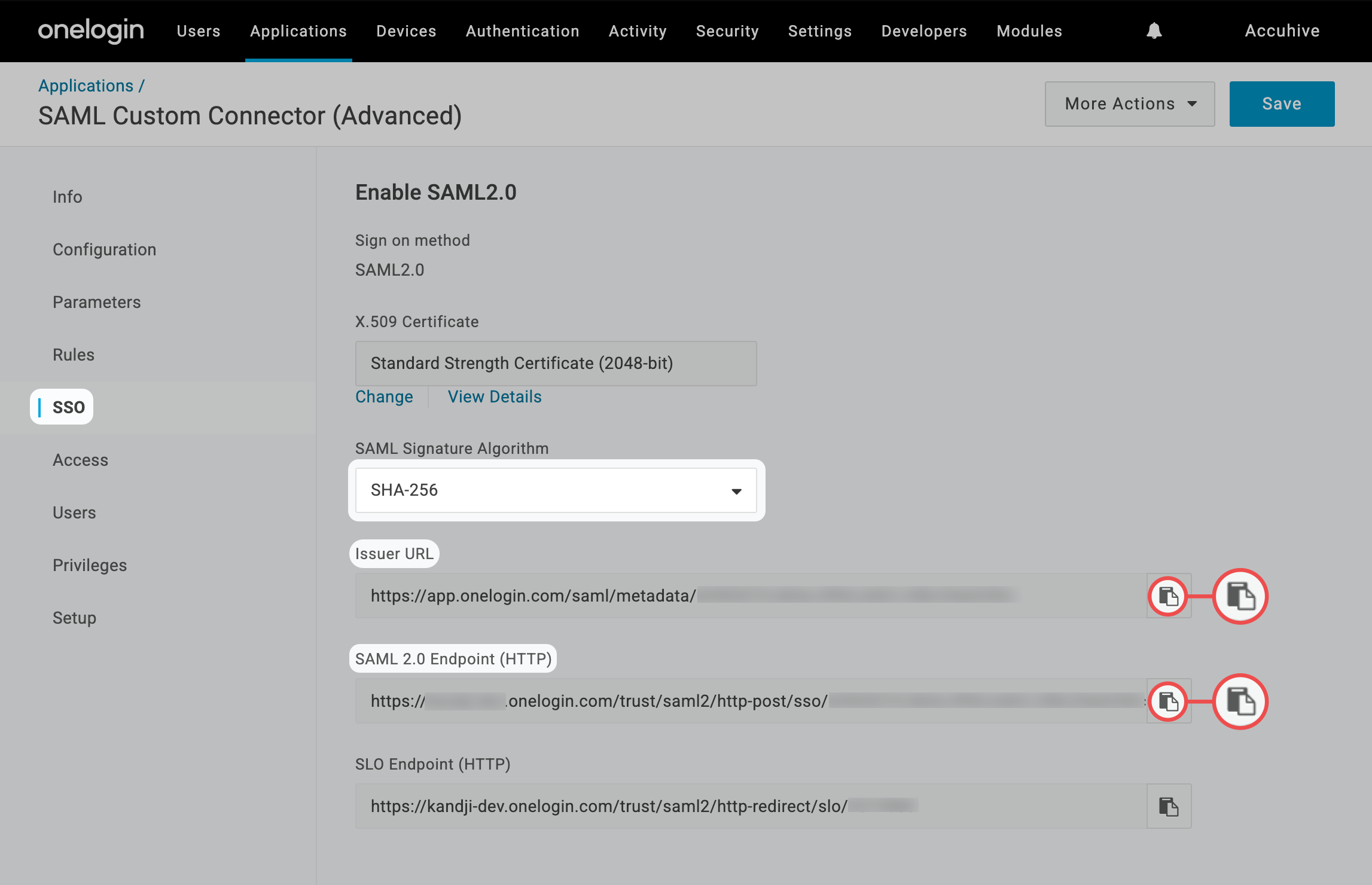
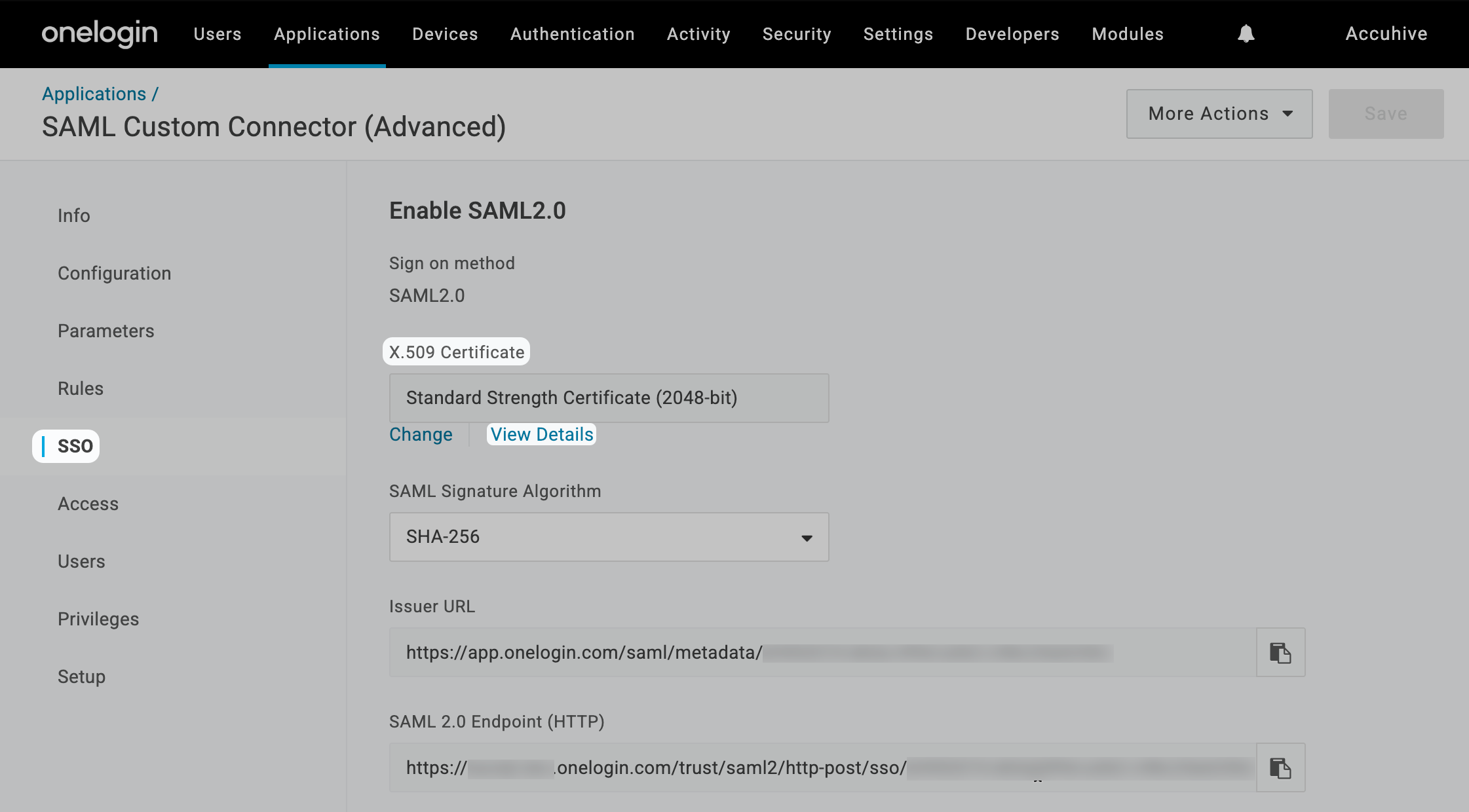
After completing the OneLogin configuration, return here to finish setting up the SAML connection in Iru Endpoint. You’ll need the Single Sign-on URL, IdP Entity ID, and certificate from OneLogin.
Configure Sign In URL
Paste the SAML 2.0 Endpoint (HTTP) URL you copied from OneLogin into the IdP Single Sign-on URL field.
Allow for Tenant Authentication
Once you have configured the SAML connection in Iru Endpoint and your identity provider, you can allow its use for tenant authentication. For step-by-step instructions, please refer to the Allowing Tenant Authentication and Managing Connections section in our Single Sign-on support article.Limit Authentication to Domain
When configuring the SAML connection, you can optionally limit authentication to one or more domains. This can be useful when the SSO connection could authenticate to multiple domains. You can limit the authentication to your Iru tenant to a subset of the available domains.Enforcing Single Sign-On
Once you have configured at least one Single Sign-on connection, you can disable Passkey, Google Social, and Microsoft Social connections. Disabling these connections will disable the ability for Iru Endpoint administrators in your tenant to authenticate via those methods. Please refer to our Single Sign-on support article for step-by-step instructions.Testing the Integration
Configure User Information
Fill in all of the corresponding user information. This user must exist in OneLogin and must be assigned to the Iru Endpoint SSO app in your OneLogin tenant.