Setting Up the SAML Connection
You’ll need to complete the initial setup in Iru Endpoint first to get the configuration information required for Okta. After copying the Entity ID and ACS URL, switch to the Okta Configuration tab to continue.
Navigate to the Account Menu Button
In Iru Endpoint, in the sidebar, click the Account Menu Button.
Access Authentication Settings
Click the Access option in the menu. Select Admin and Authentication
Select the Admin and authentication tab (selected by default) and scroll down to Authentication methods.
Add Authentication Method
Click + Authentication method.
Enter Display Name
Enter a display name for the SSO Connection.
Select Authentication Method
Select SAML for the Authentication method.
Create Connection
Click Create.
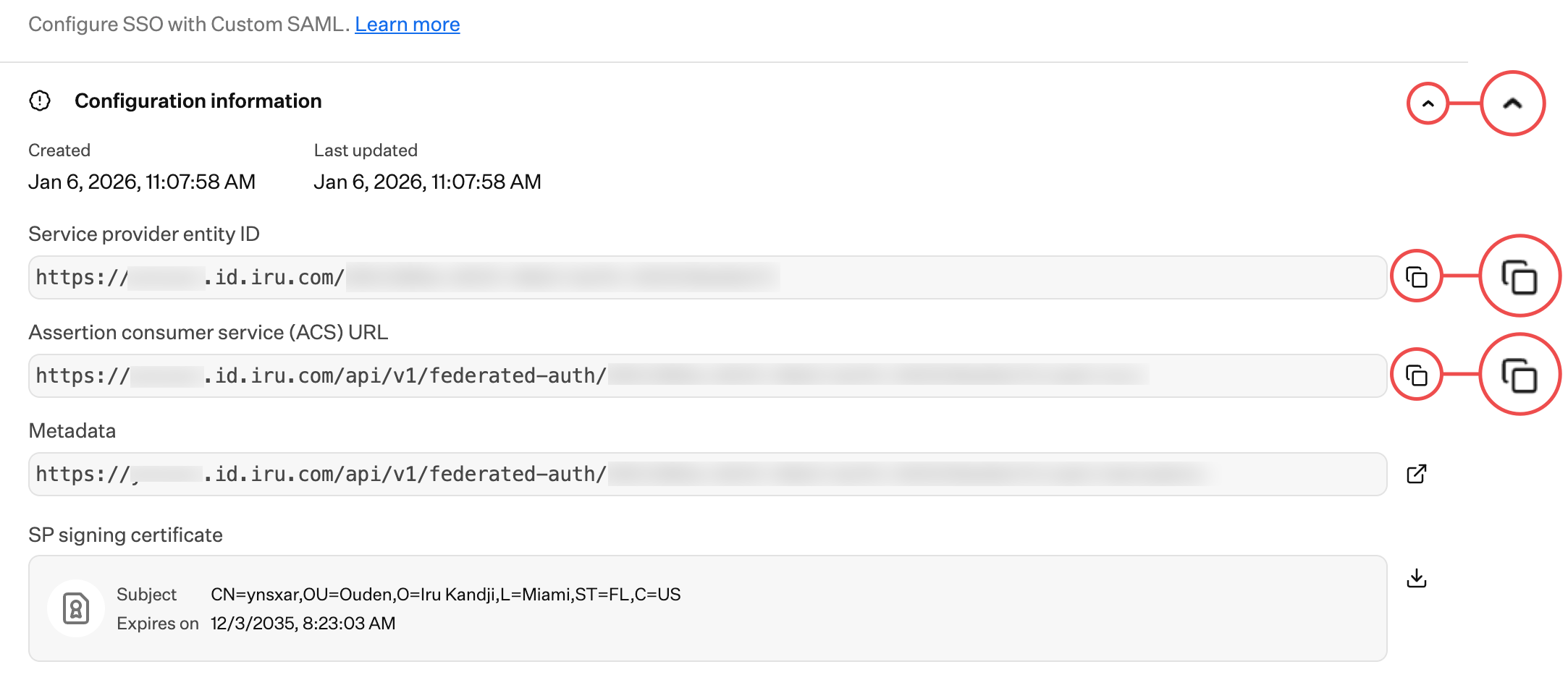
Configuration Information
Click Configuration information if that section is not already expanded.
Copy Service Provider Entity ID
Copy the Service provider entity ID into a text document for later use. You’ll need this for the Okta configuration.
Copy ACS URL
Copy the Assertion consumer service (ACS) URL into a text document for later use. You’ll need this for the Okta configuration. Keep Tab Open
Keep the Iru Endpoint configuration modal open, then switch to the Okta Configuration tab to continue.
Configuring Iru Endpoint SAML Connection
After completing the Okta configuration, return here to finish setting up the SAML connection in Iru Endpoint. You’ll need the Single Sign-on URL, IdP Entity ID, and certificate from Okta.
Return to Iru Endpoint
Go back to the Custom SAML modal in Iru Endpoint.
Set IdP Attribute
Set IdP attribute to Subject.
Set Attribute Name
Leave Attribute name blank.
Set User Attribute
Set User attribute to User Principal Name (UPN).
Configure Sign In URL
Paste the Single Sign-On URL you copied from Okta into the Sign In URL text field.
Add IdP Entity ID
Paste the Issuer information you copied from Okta into the IdP Entity ID field.
Upload Certificate
Upload the Okta certificate you downloaded earlier. Set Protocol Binding
Set the Protocol Binding to HTTP-POST.
Set Request Algorithm
Ensure that the Request Algorithm is set to RSA-SHA256.
Set Digest Algorithm
Ensure that Sign Request Algorithm Digest is set to SHA256.
Enable Sign Request
Ensure that Sign Request is enabled.
Set Response Signature Verification
Set the Response Signature Verification to Assertion.
Set Destination
Leave the Destination field blank.
Set Allowed Signature Algorithm
Set Allowed Signature Algorithm to RSA-SHA256.
Set Allowed Digest Algorithm
Set Allowed Digest Algorithm to SHA256.
Allow for Tenant Authentication
Once you have configured the SAML connection in Iru Endpoint and your identity provider, you can allow its use for tenant authentication. For step-by-step instructions, please refer to the Allowing Tenant Authentication and Managing Connections section in our Single Sign-on support article.Limit Authentication to Domain
When configuring the SAML connection, you can optionally limit authentication to one or more domains. This can be useful when the SSO connection could authenticate to multiple domains. You can limit the authentication to your Iru tenant to a subset of the available domains.Enforcing Single Sign-On
Once you have configured at least one Single Sign-on connection, you can disable Passkey, Google Social, and Microsoft Social connections. Disabling these connections will disable the ability for Iru Endpoint administrators in your tenant to authenticate via those methods. Please refer to our Single Sign-on support article for step-by-step instructions.Testing the Integration
Add Test User
Add a test user to the Admin Team in Iru Endpoint by clicking New User.
Configure User Information
Fill in all of the corresponding user information. This user must exist in Okta and must be assigned to the Okta SSO app in your Okta tenant.
Close Invite Window
Once the invite is submitted, close the Invite User window.
Refresh Access Page
Refresh the Access page in Iru Endpoint. You should see the user who was added.
Test SSO Login
Go to the user’s email to accept the invite and log in with the new SAML SSO connection.
Before starting the Okta configuration, complete the initial setup in the Iru Web App Configuration tab to get the Service Provider Entity ID and ACS URL. You’ll need these values to configure the Okta application.
Configuring Okta Application
Log in to Okta
In a new browser tab, log in to the Admin Console in your Okta tenant.
Navigate to Applications
On the left-hand side, click the reveal triangle next to Applications, then click Applications.
Create App Integration
Click Create App Integration. Select SAML 2.0
Select SAML 2.0 as the app integration type.
Configure App Name
Enter an App name.
Configure App Logo
Upload an optional App logo.
Configure SAML Settings
In the Single sign-on URL field, paste the Iru Endpoint Assertion Consumer Service URL that was copied earlier.
Set Entity ID
In the Audience URI (SP Entity ID) field, paste the Iru Endpoint Entity ID that was copied earlier.
Configure Name ID Format
Ensure that the Name ID format is set to Unspecified.
Configure Application Username Format
Ensure that the Application username format is set to Email.
Configure Update Username On
Ensure that Update application username on is set to Create and update.
Set App Type
Select This is an internal app that we have created.
View SAML Instructions
Back at the Sign On tab, find the link to View SAML setup instructions and open it in a new browser tab. Copy Sign-On URL
Copy the Identity Provider Single Sign-On URL and save it in a text document for later use in Iru Endpoint.
Copy Issuer Information
Copy the Identity Provider Issuer information and save it in a text document. You will paste this into the IdP Entity ID field in Iru Endpoint.
Download Certificate
Download the certificate file and save it for use in Iru Endpoint. Assigning Users to the Okta App
Navigate to Assignments
Go back to the Okta app and click the Assignments tab.
Assign to People or Groups
Click the Assign dropdown menu and click Assign to People or Assign to Groups. Search for User or Groups
Search for a users or groups to assign.
Click Assign
Click Assign next to the user or group. Complete Assignment
Once the user is assigned, click Done. Verify Assignment
You should see the users or groups that you have selected in the list. After completing the Okta Configuration, return to the Iru Web App Configuration tab to finish setting up the SAML connection using the SSO URL, Entity ID, and certificate you copied from Okta.