About Microsoft Entra ID Native Integration
Microsoft Entra ID Native integration in Iru Endpoint lets you set up native Microsoft Entra ID integration for SSO. Users authenticate using their Microsoft Entra ID credentials through OAuth2/OpenID Connect.How It Works
When users attempt to access Iru Endpoint, they’re redirected to Microsoft Entra ID for authentication using OAuth2/OpenID Connect protocols. After successful authentication, Microsoft Entra ID sends an access token back to Iru Endpoint, which validates the user’s identity and grants access. SSO can be used for Iru Endpoint Web App sign-in and for Require Authentication with Automated Device Enrollment.Microsoft Entra ID is the new name for Azure AD (Azure Active Directory)
Because client secrets have a maximum life of 24 months, we recommend that you configure SAML based Single Sign-On instead of using the method described in this document.
Prerequisites
Before you begin, ensure you have:- Access to the Iru Endpoint Web App as an Admin or Account Owner
- An administrator account in Microsoft Entra ID with permissions to create app registrations (such as Global Administrator, Application Administrator, or Cloud Application Administrator)
- Iru Web App Configuration
- Microsoft Entra ID Configuration
Configuring Iru Endpoint Connection
Follow these steps to configure the connection in Iru:Select Admin and Authentication
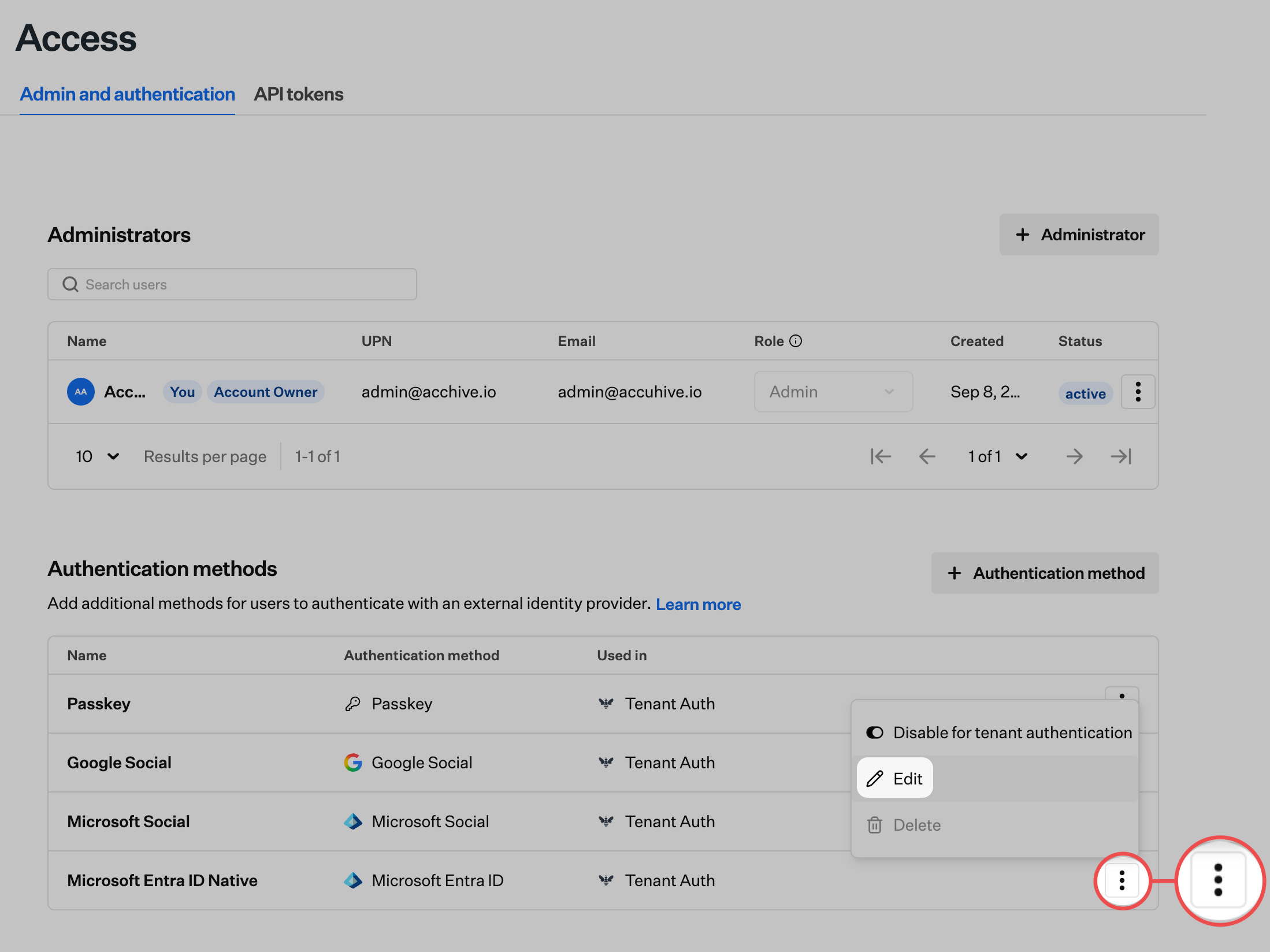
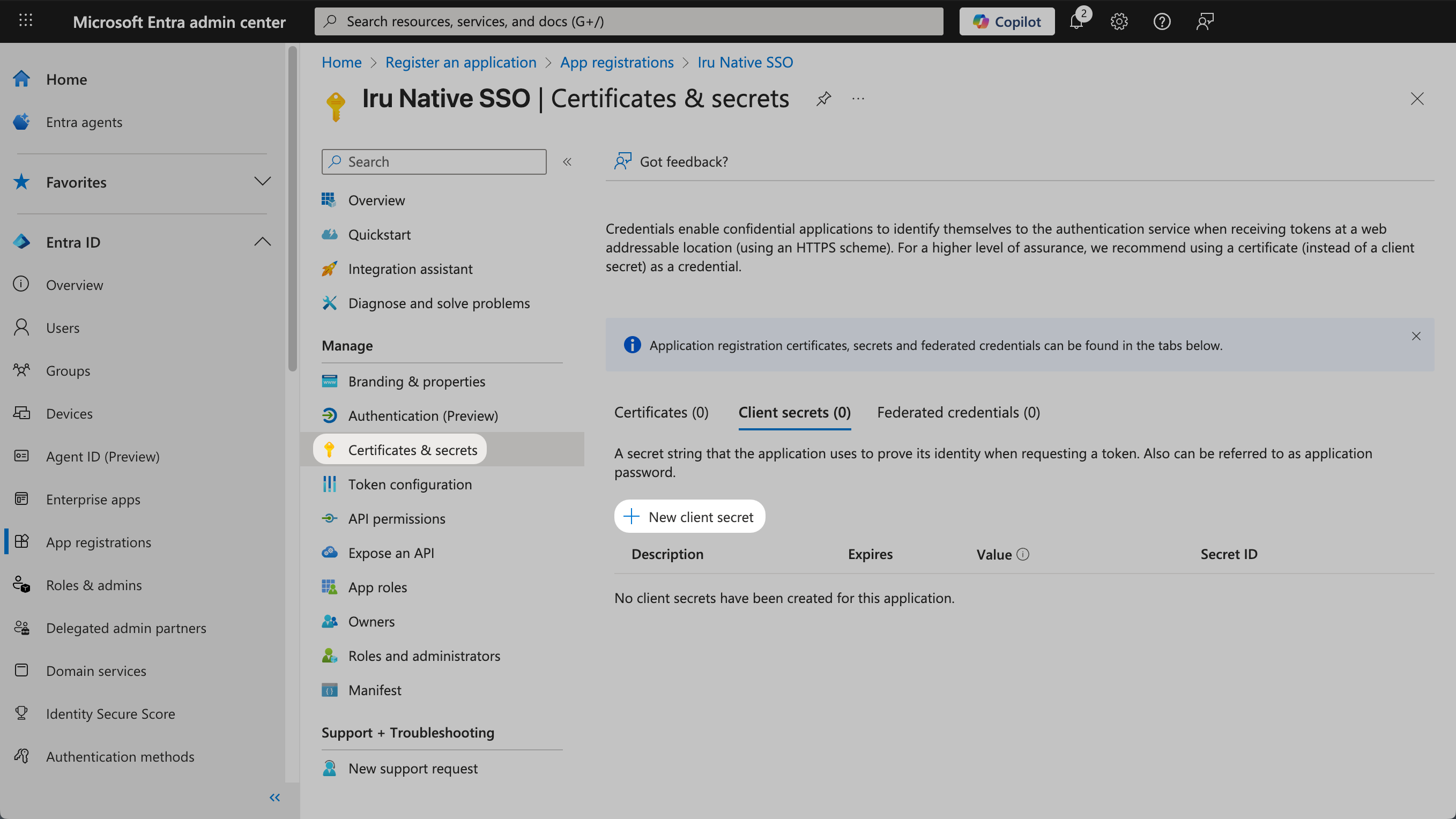
Select the Admin and authentication tab (selected by default) and scroll down to Authentication methods.
Copy Redirect URL
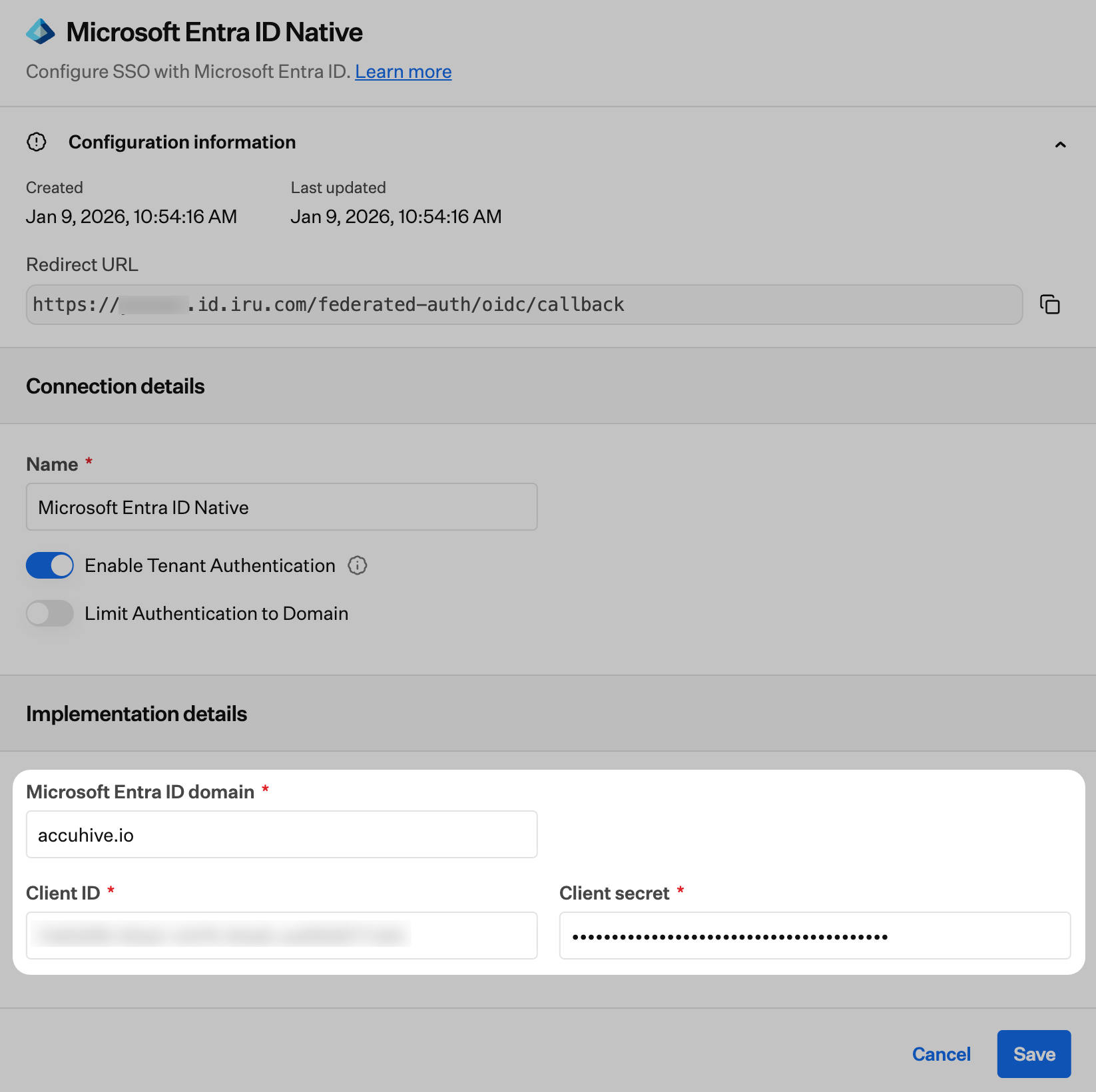
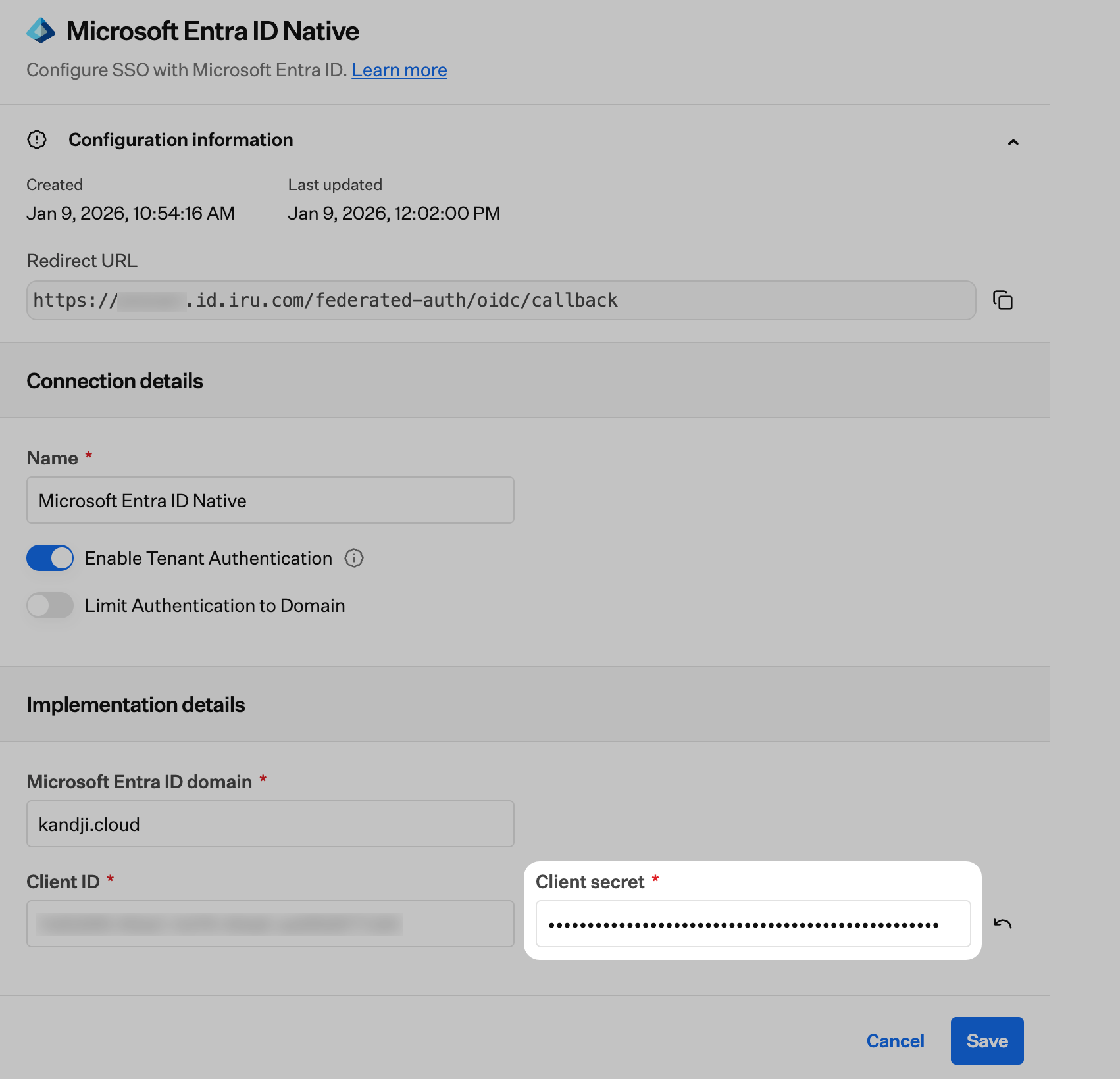
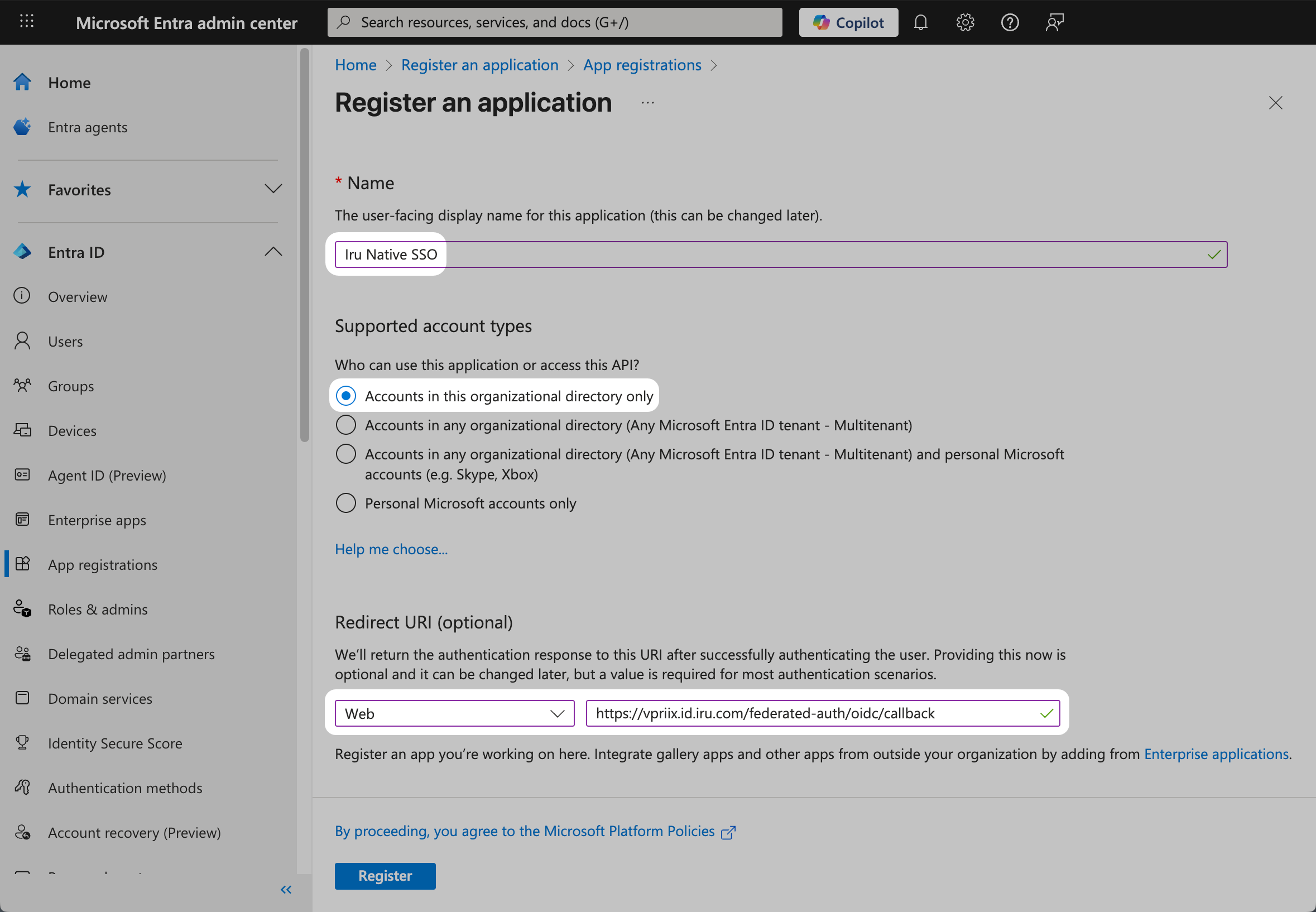
Copy the Redirect URL into a text document for later use. You’ll need this for the Microsoft Entra ID configuration.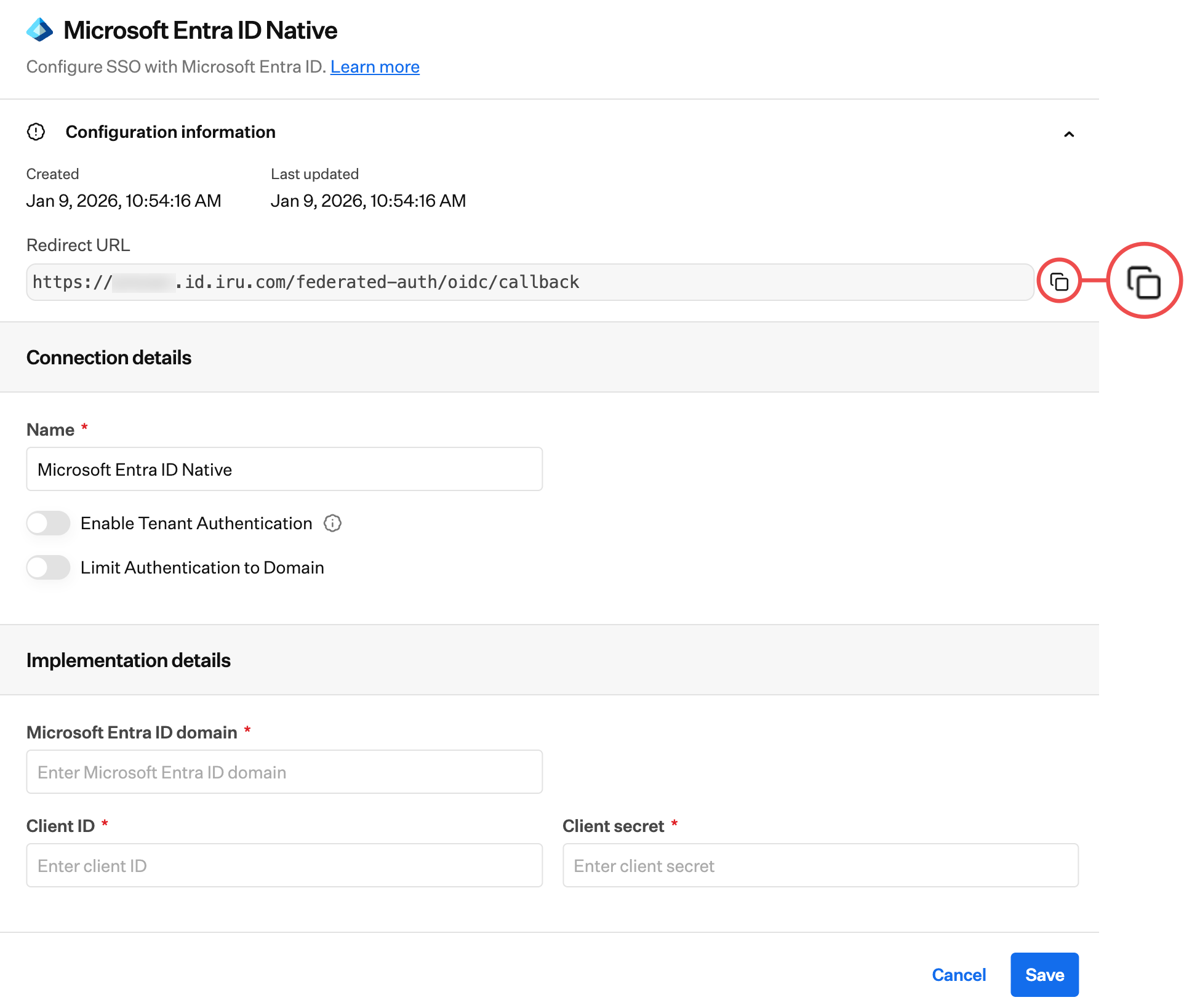

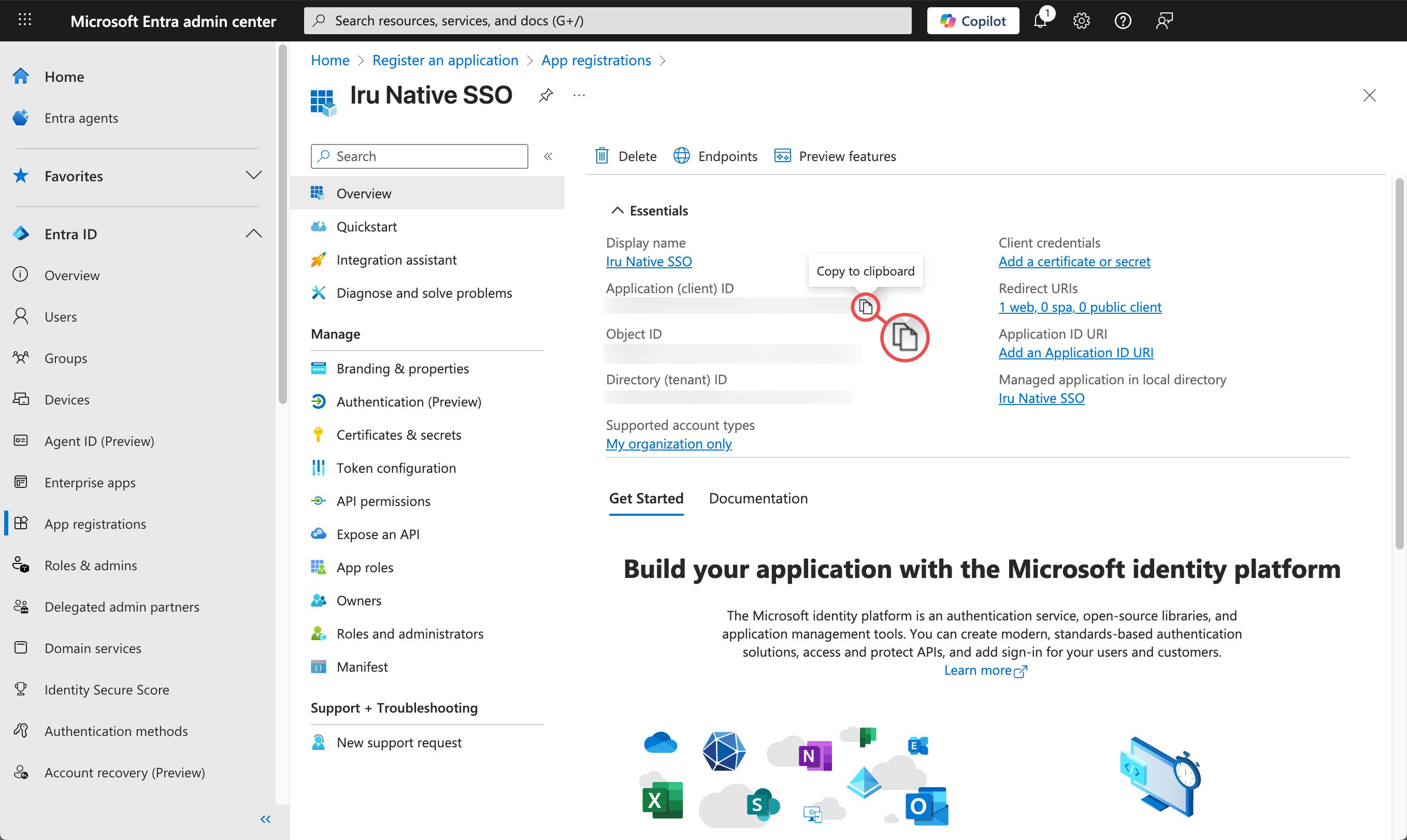
After completing the Microsoft Entra ID configuration, return here to finish setting up the SSO connection in Iru Endpoint. You’ll need the Client ID and Client secret you copied from Microsoft Entra ID.
Enter Directory Domain
Enter the Tenant ID that the application was registered within into the Microsoft Entra ID Domain field. Please refer to Microsoft’s documentation to locate your Tenant ID.
Authorize Connection
After saving, a new dialogue box will appear with a link to authorize your connection. A Microsoft Entra ID administrator for your domain must click the link and complete this process to authorize the application. This box will not go away after authorization is completed.
Allow for Tenant Authentication
Once you have configured the SAML connection in Iru Endpoint and your identity provider, you can allow its use for tenant authentication. For step-by-step instructions, please refer to the Allowing Tenant Authentication and Managing Connections section in our Single Sign-on support article.Limit Authentication to Domain
When configuring the SAML connection, you can optionally limit authentication to one or more domains. This can be useful when the SSO connection could authenticate to multiple domains. You can limit the authentication to your Iru tenant to a subset of the available domains.Enforcing Single Sign-On
Once you have configured at least one Single Sign-on connection, you can disable Passkey, Google Social, and Microsoft Social connections. Disabling these connections will disable the ability for Iru Endpoint administrators in your tenant to authenticate via those methods. Please refer to our Single Sign-on support article for step-by-step instructions.Renewing the Client Secret
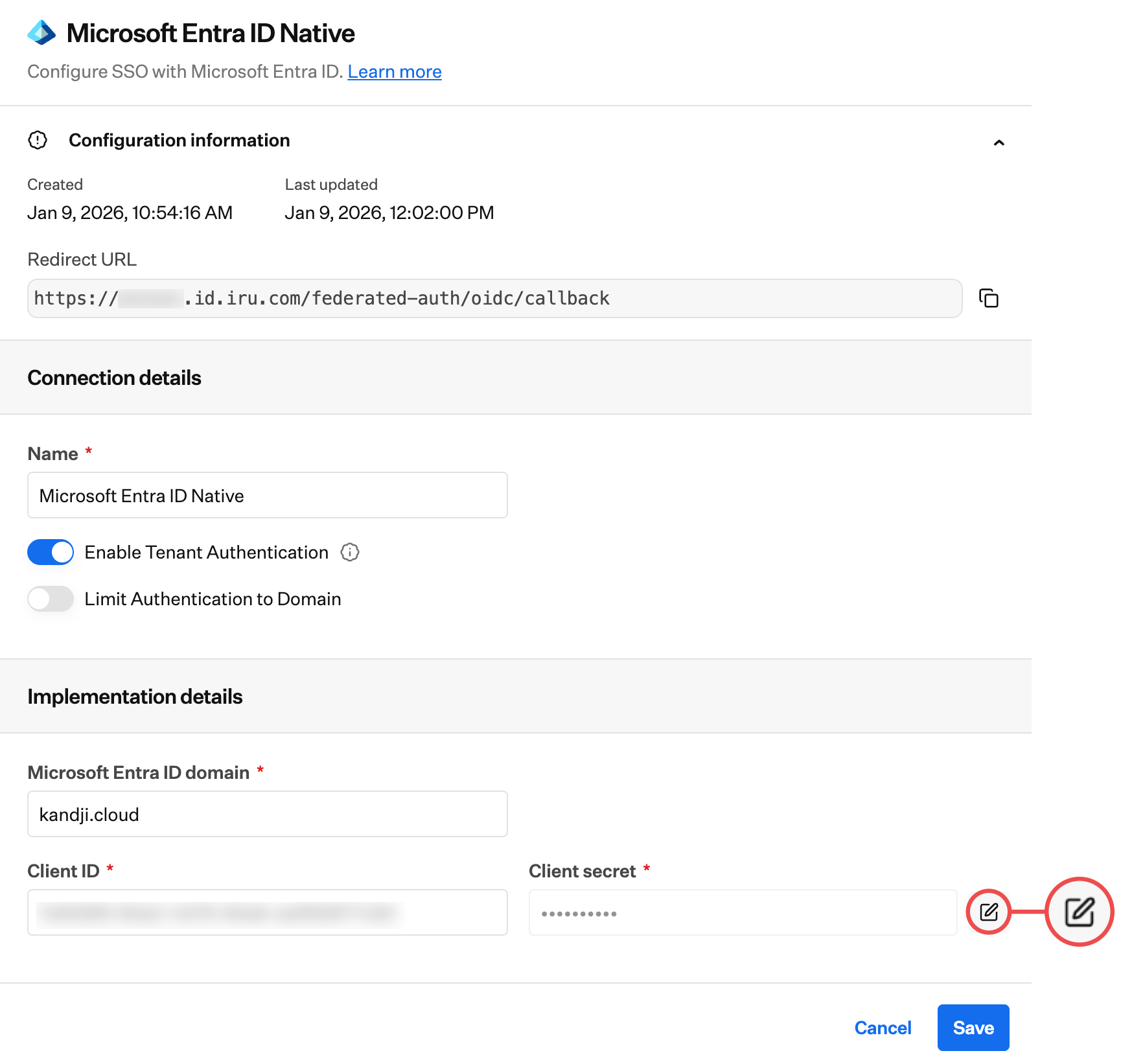
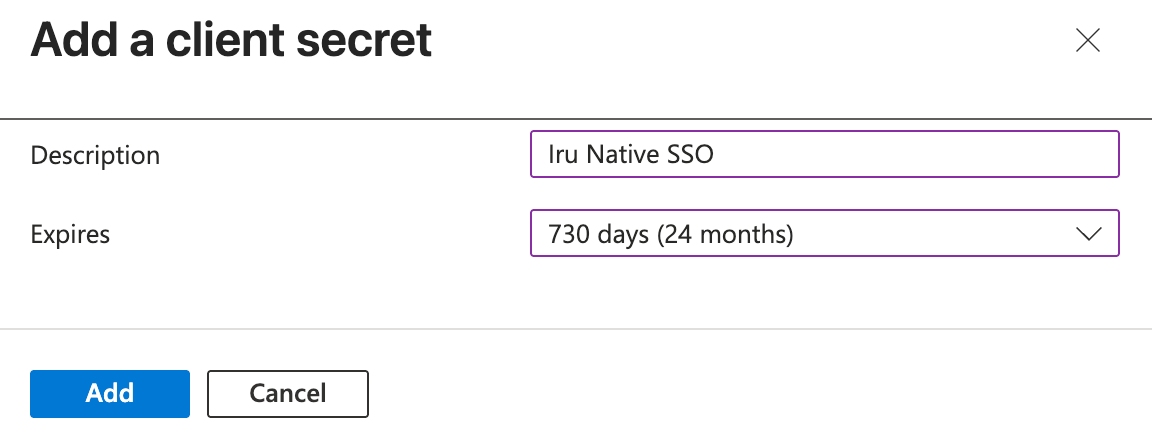
Create New Client Secret
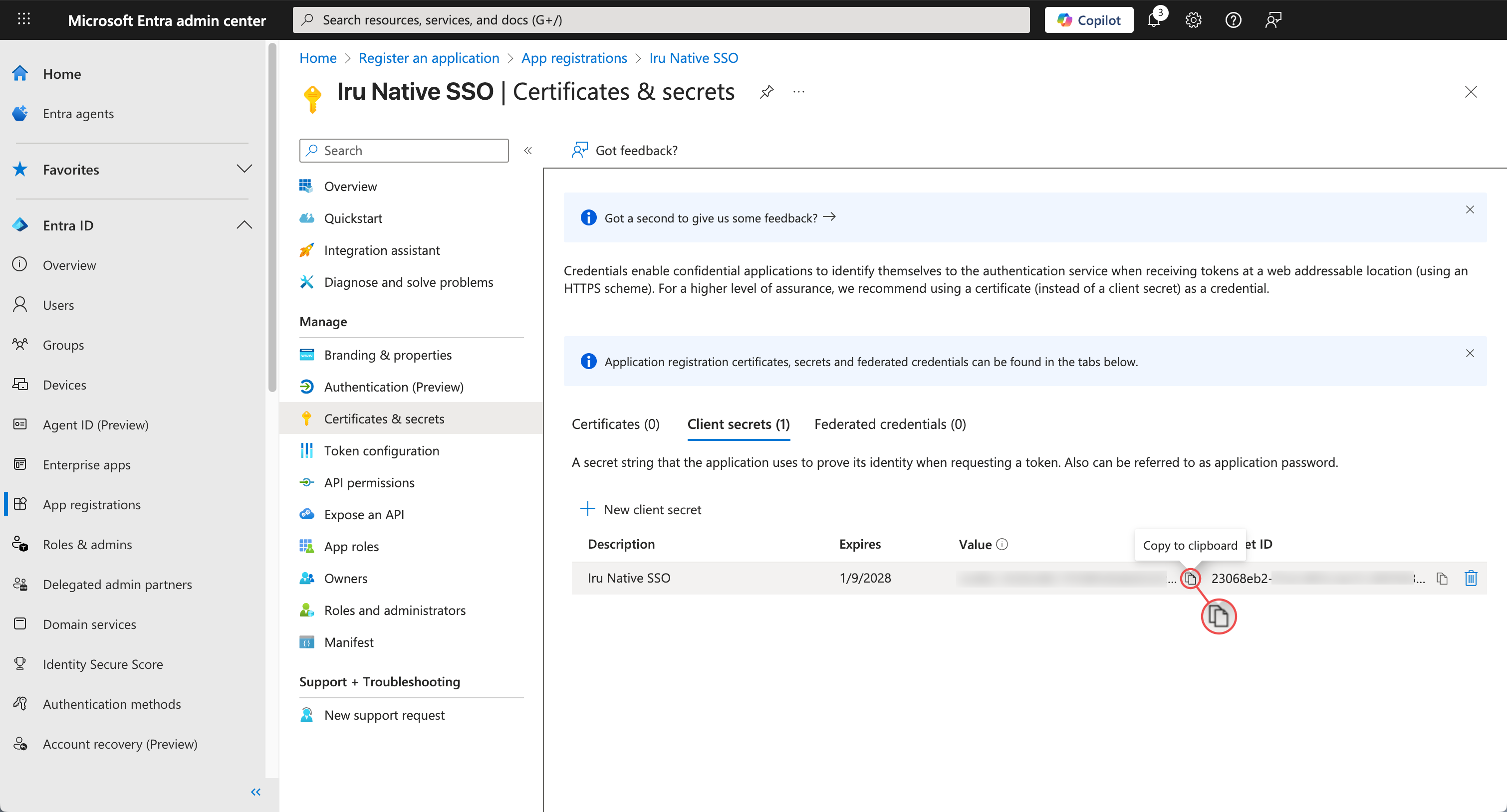
Follow the steps in the Microsoft Entra ID Configuration tab above to create a new client secret. Complete steps “Access Certificates and Secrets” through “Copy Secret Value” to create a new client secret and copy the value.
Navigate to Admin and authentication
After copying the value, return to the Iru Web App Configuration tab and follow steps 1-3 from the Configuring Iru Endpoint Connection section.
Select SSO Integration
Click on the ellipsis next to the SSO integration that was created earlier in this article.
Test Configuration
Be sure to test the configuration by signing into the Iru Endpoint web app and choosing the Native SSO login option that was created. You’ll want to test this with a private browser window/incognito window and verify that you are able to sign in to the Iru Endpoint web app.