This guide applies to Mac computers
This article goes over configuring Passport to use Web login. If you want to configure Mac Login, please see Configure Passport with Microsoft Entra ID - Mac Login.
About Passport with Microsoft Entra ID Web Login
Passport with Microsoft Entra ID Web Login enables users to log into Mac computers using their Microsoft Entra ID credentials through a web-based authentication interface. This method supports multi-factor authentication and provides a more secure login experience.How It Works
Passport integrates with your Microsoft Entra ID tenant to authenticate users at the macOS login screen using a web view that displays your organization’s Entra ID login page. This allows for full MFA support and provides a familiar authentication experience for users.Prerequisites
You will need access to a Microsoft Entra ID admin user account to grant the Passport app the correct permissions. For instructions on configuring multifactor authentication (MFA) within Microsoft Entra ID, please see this Microsoft guide.Create the App Registration
Sign in to Microsoft Entra admin center
Sign in to the Microsoft Entra admin center using a Global Administrator account.
Configure application details
On the Register an application dialog, enter a name for the new application (such as Iru Passport Web Login).
Select platform
In the Redirect URI section, in the Select a platform drop-down, choose Public client/native (mobile & desktop).
Enter redirect URI
In the URI field, enter the following, https://localhost
For more information about redirect URI restrictions, platform types, and best practices, see Microsoft’s redirect URI documentation.
Collecting Configuration Details
Prepare secure document
Open a secure text document where the values for this OIDC app can be temporarily stored. You will need these details when you configure the Passport Library Item.
Copy Application ID
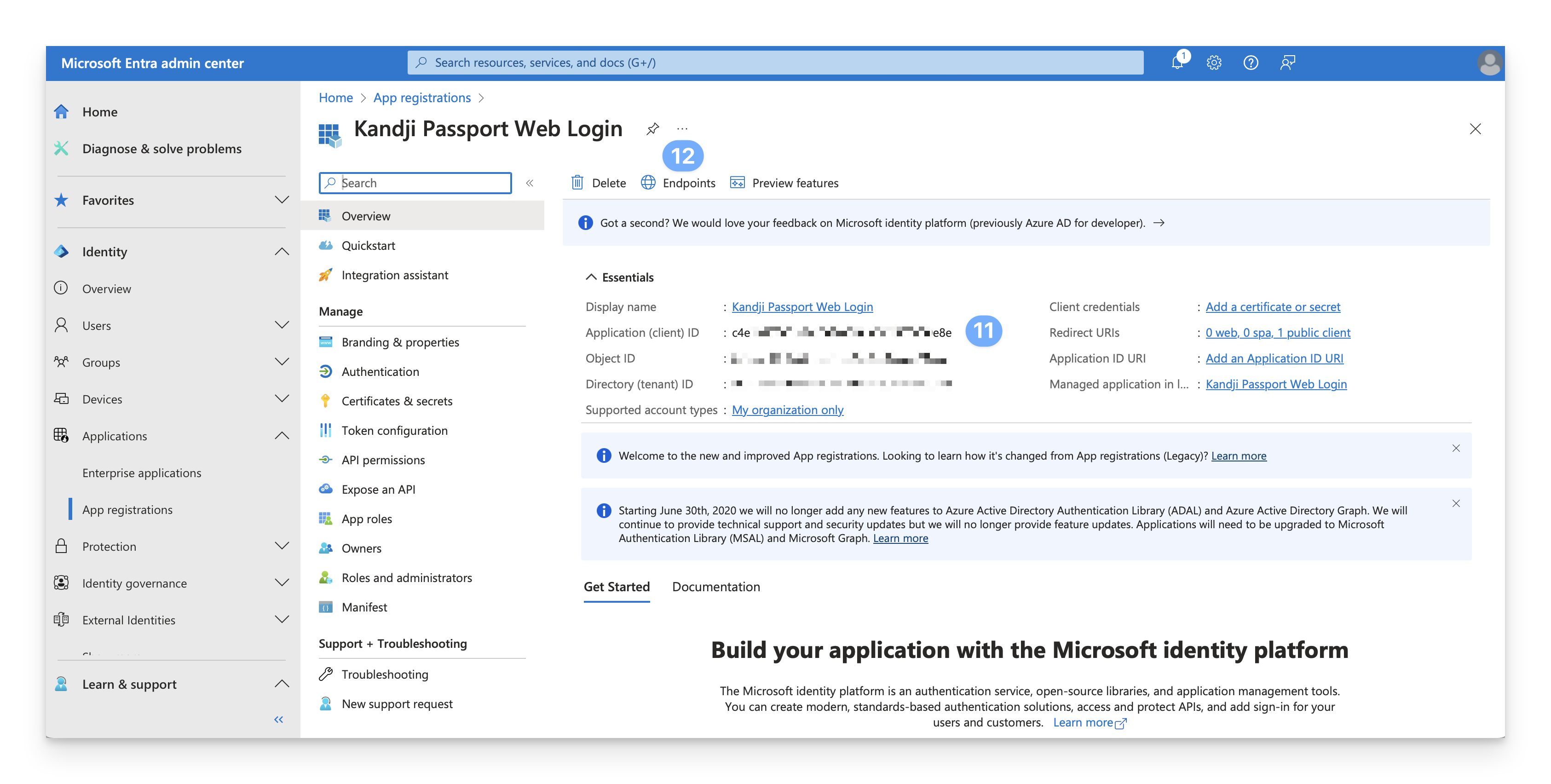
Copy the Application (client) ID on the Overview page to a temporary secure text document.
Copy Identity provider URL
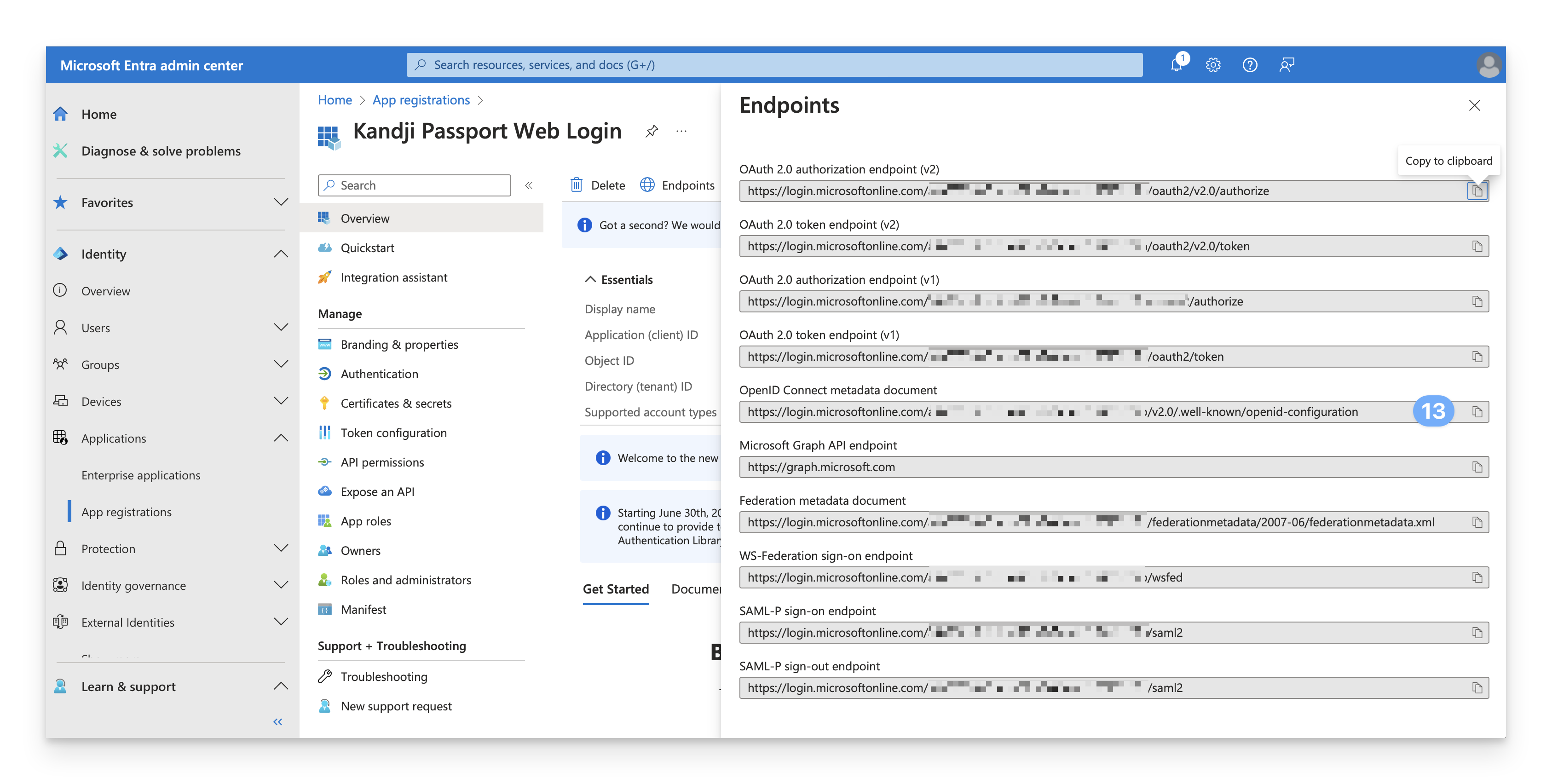
Copy OpenID Connect metadata document (identity provider URL) to a temporary secure text document.
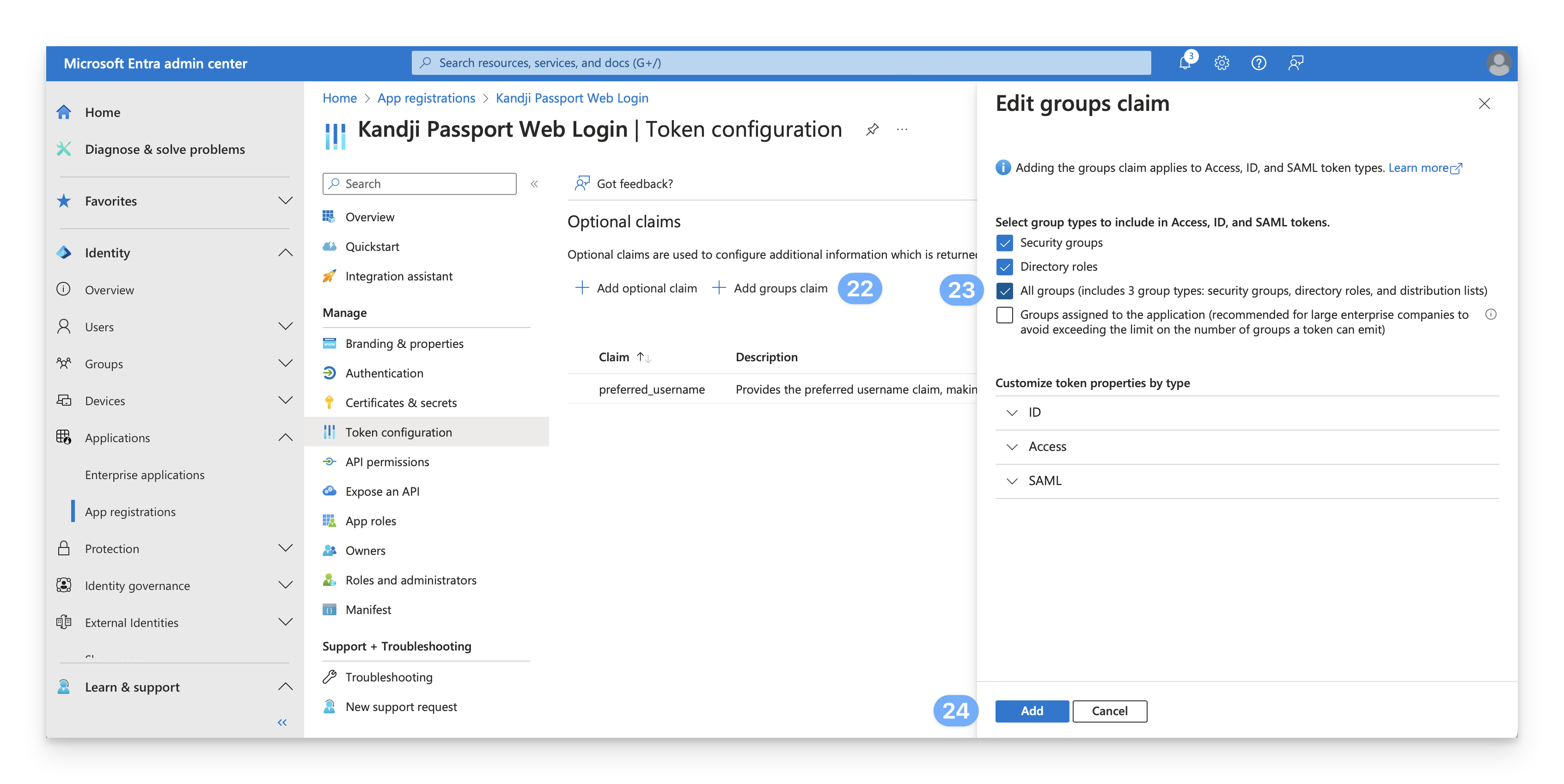
Select groups
Select All groups.
Entra ID SAML only supports up to 150 security groups. If you have more than 150 security groups, you should not use All groups, but rather select specific groups. You can read more in Microsoft’s Configure group claims for applications by using Microsoft Entra ID article.
API Permissions
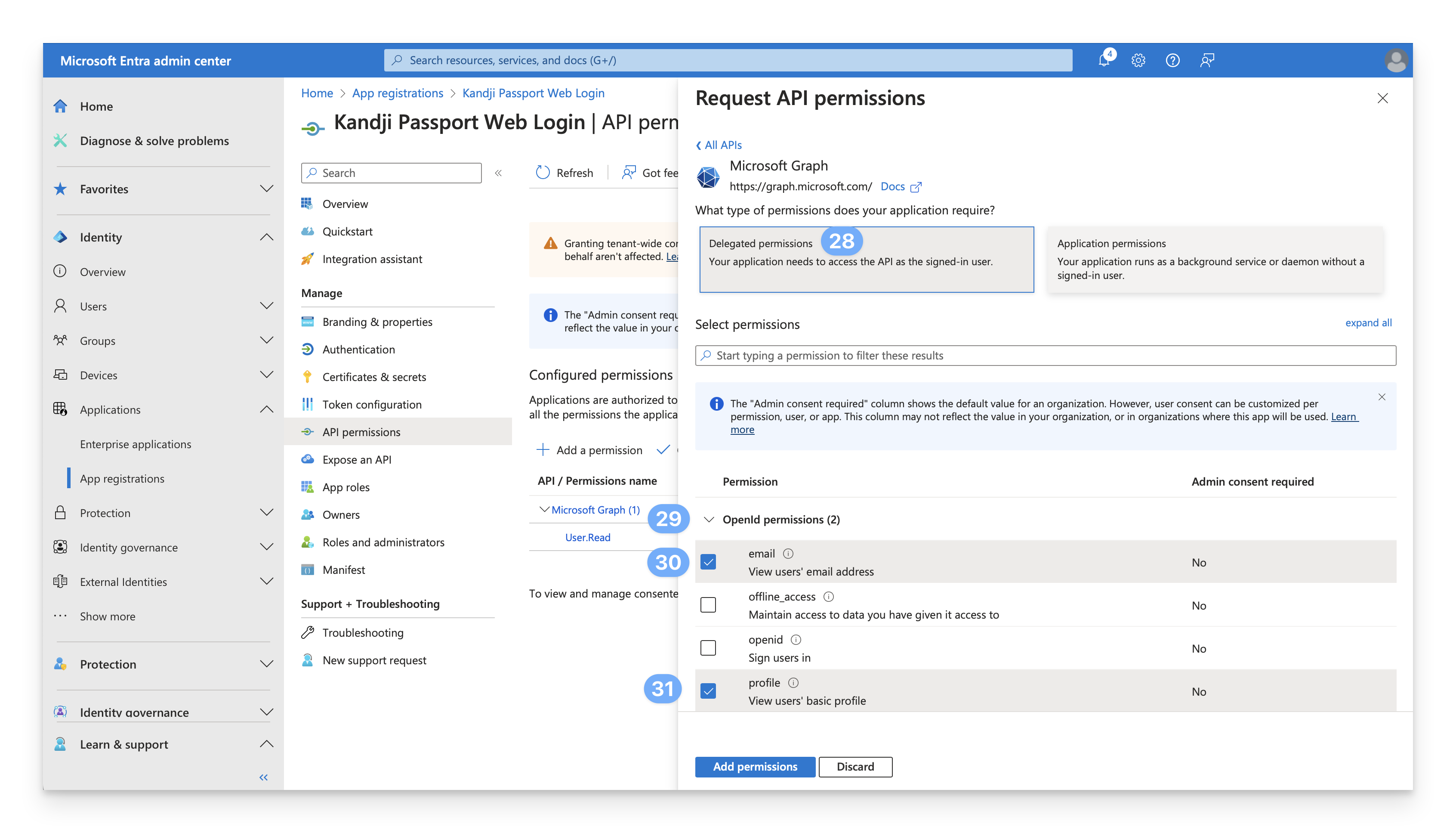
Expand OpenID permissions
Confirm that the OpenID permissions section is expanded. If it isn’t, click the icon next to it to expand it.
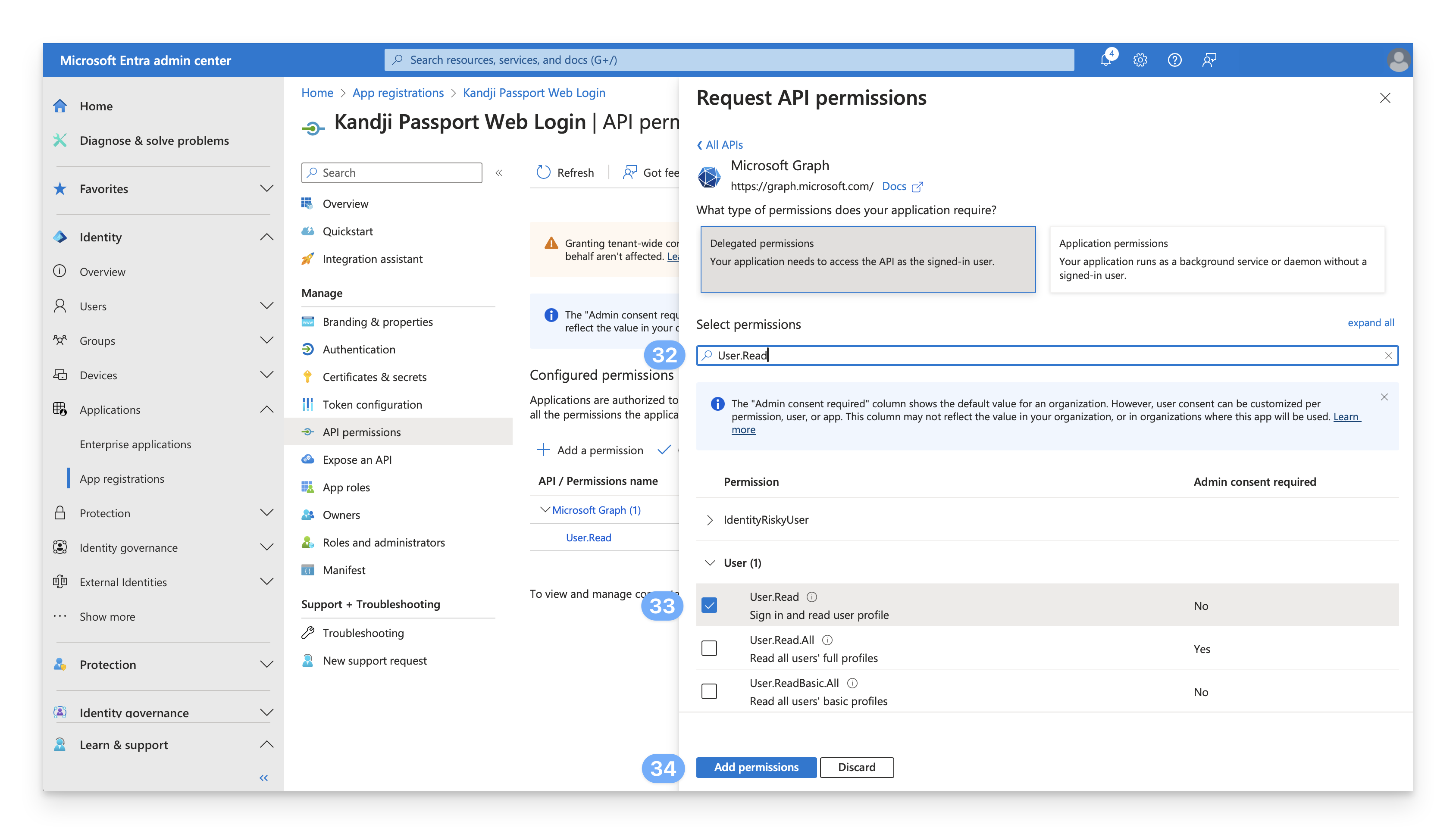
Confirm User.Read selection
In the User section, confirm that User.Read is already selected. If it isn’t, select it.
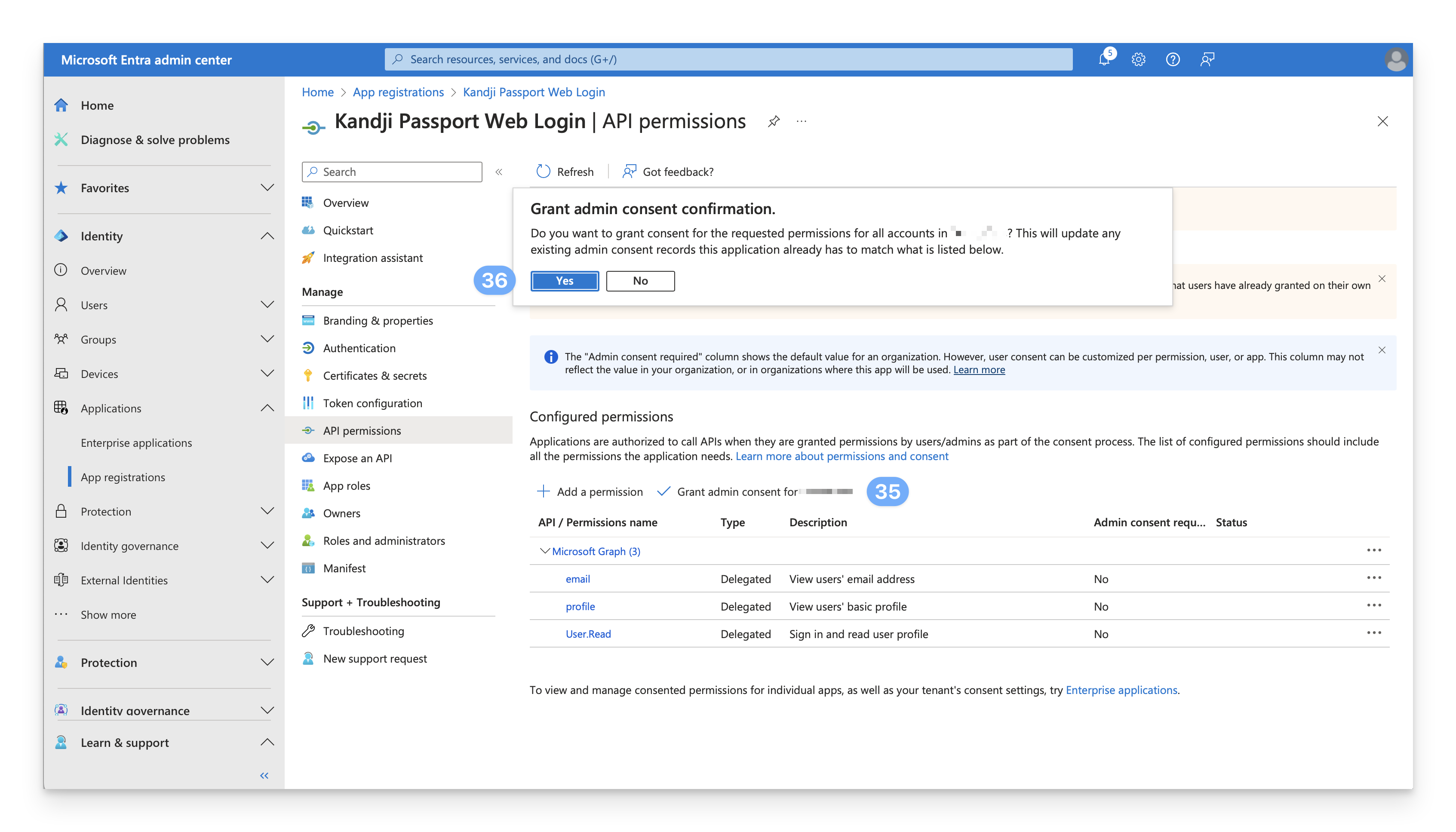
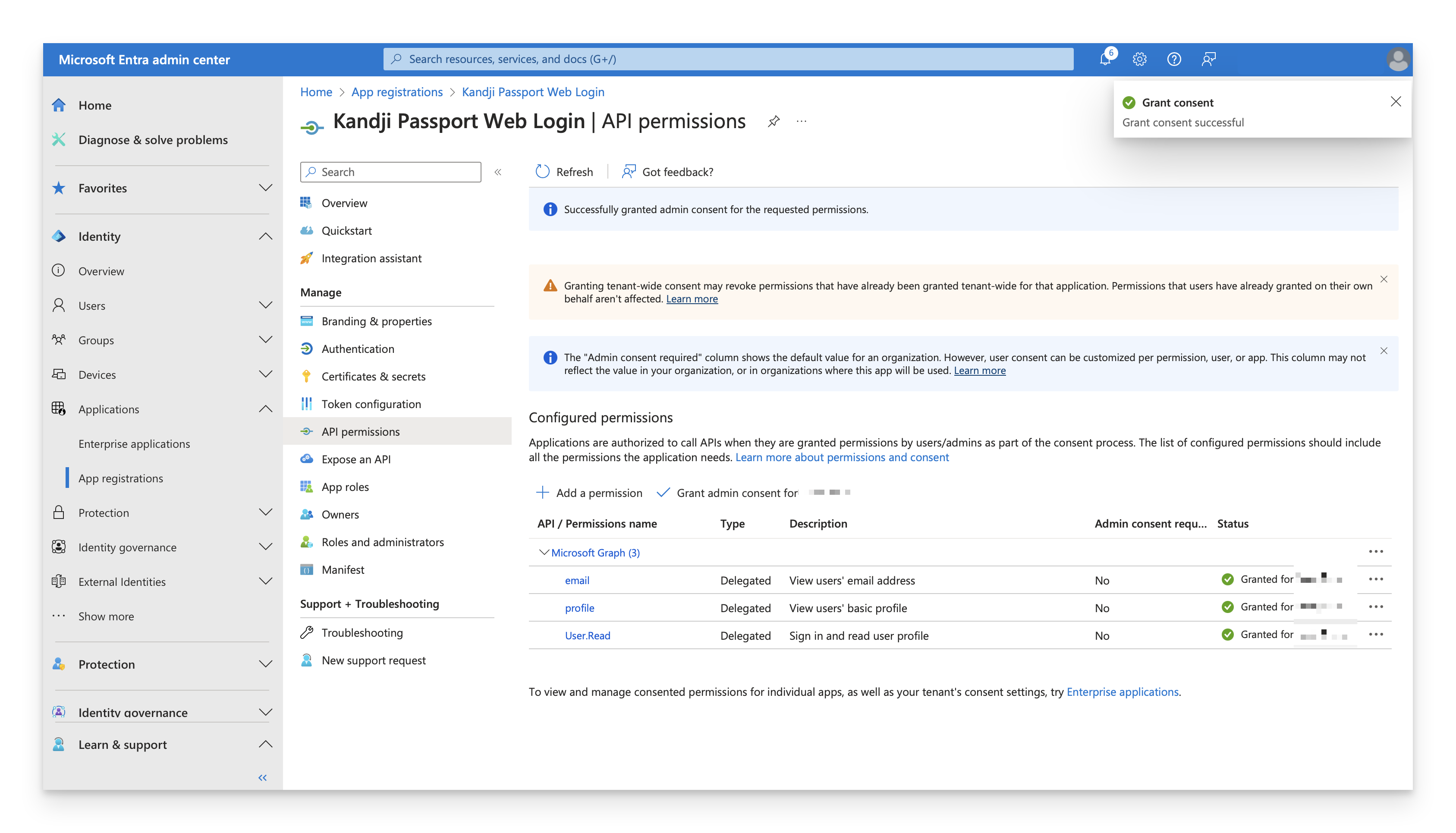
Grant admin consent
While still on the API permissions page, select Grant admin consent for <your_tenant_name>.
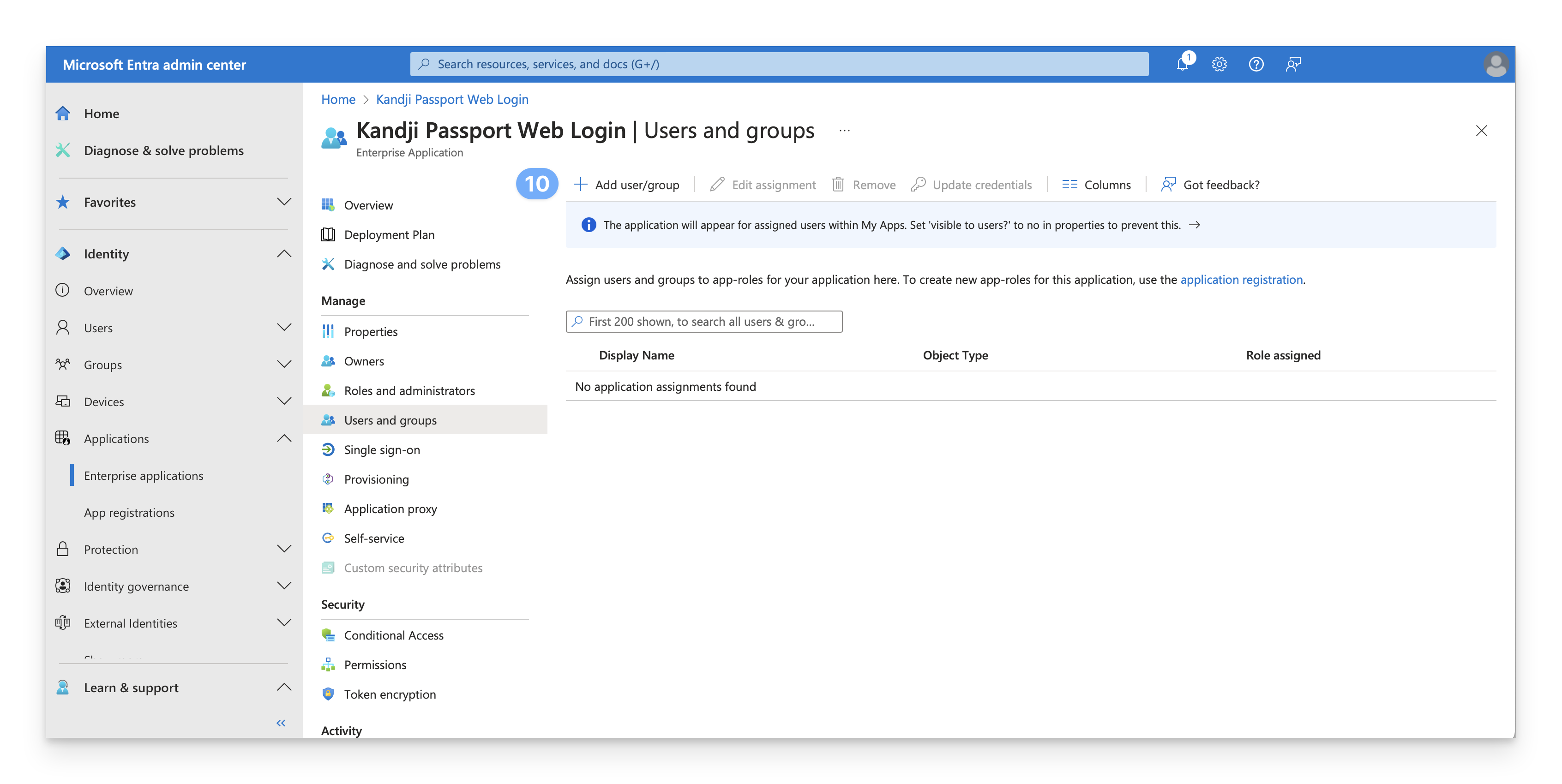
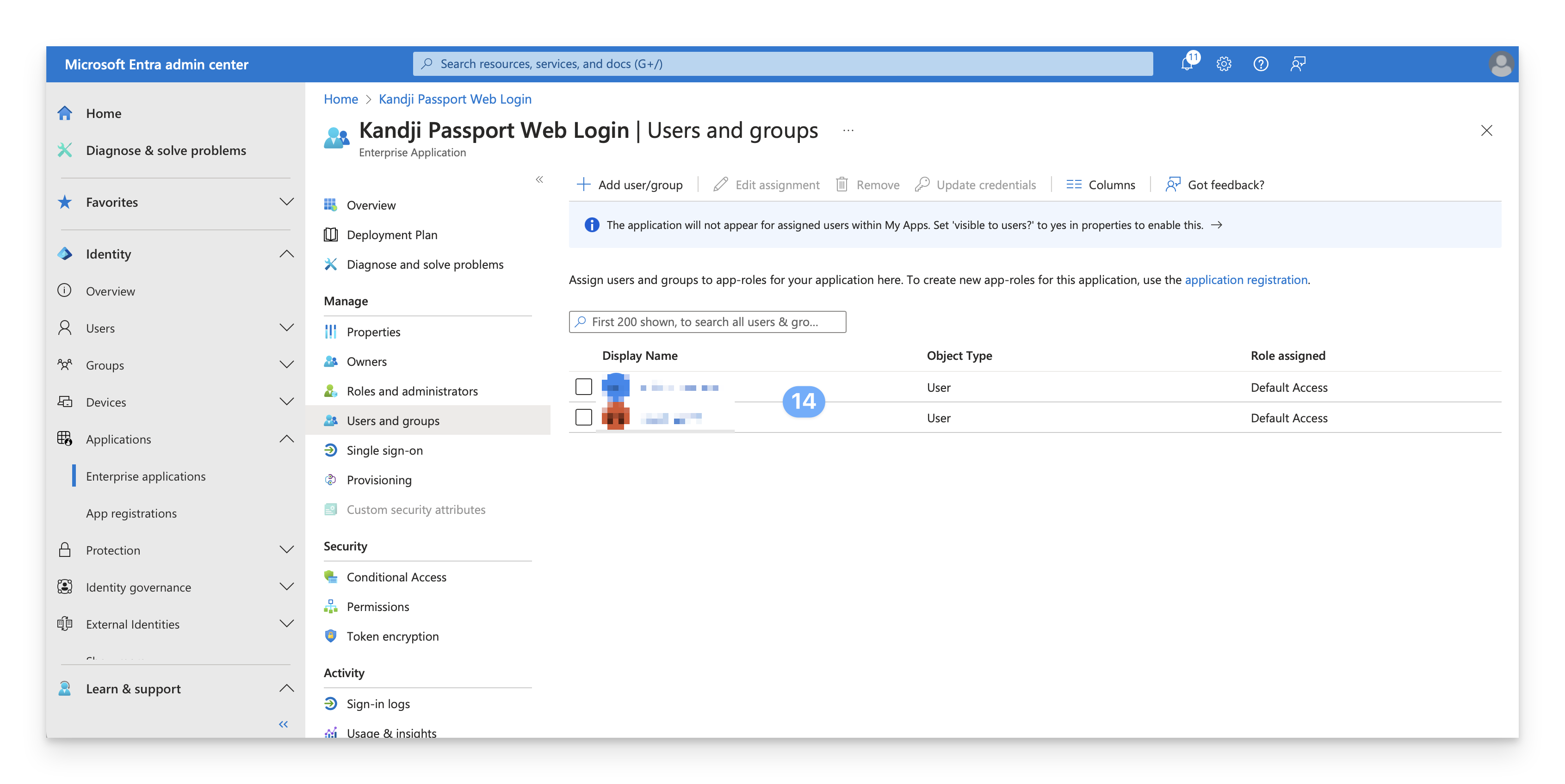
Assign Users and Groups
By default, when you create a new App registration, the “Assignment required?” attribute is set to “No”. However, if your Passport Enterprise app is set to require assignment, you will need to follow these steps to assign users in order to be able to use your Passport app.
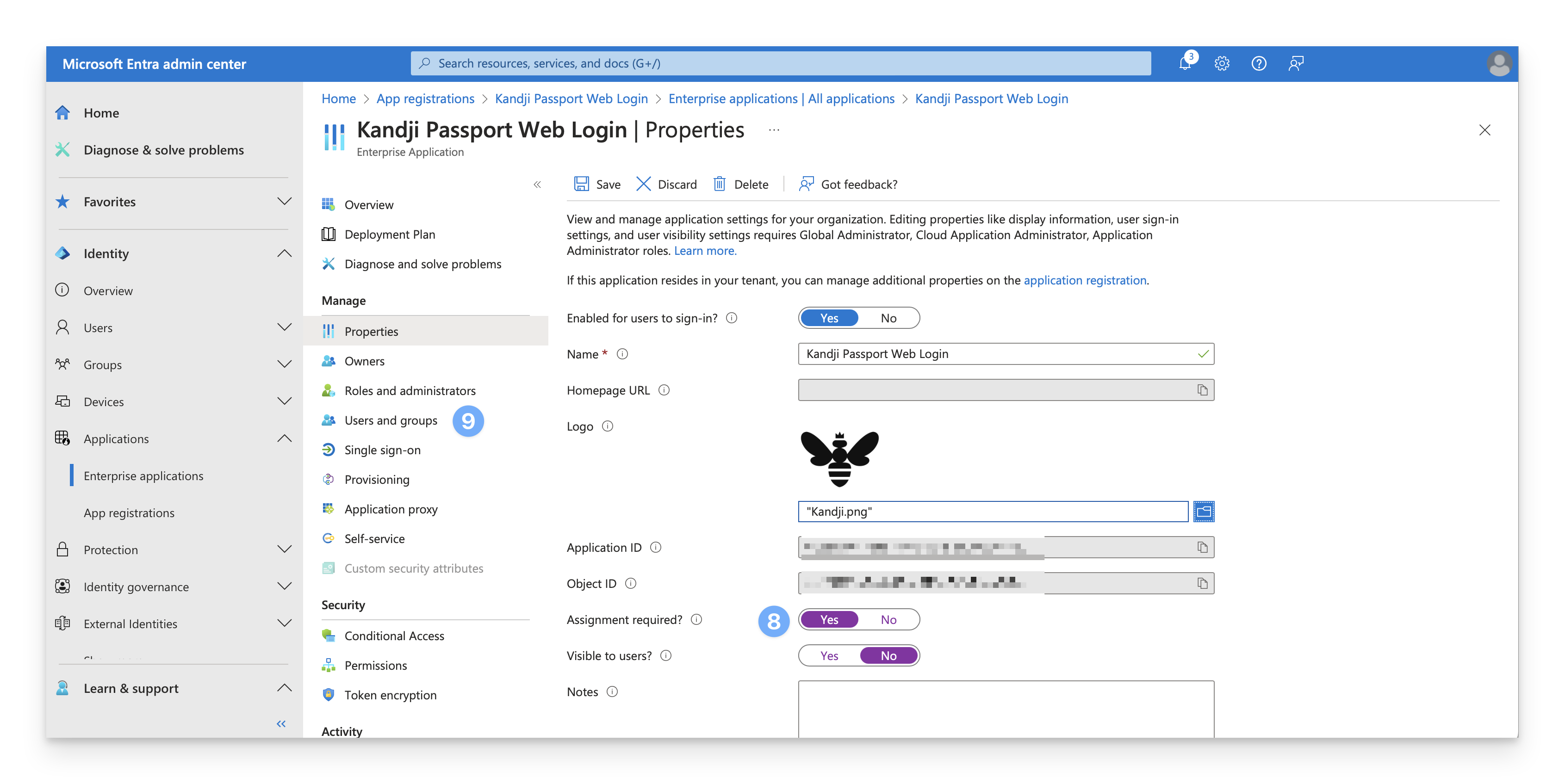
Access Enterprise Applications
In the Identity navigation menu on the left, open Applications and select Enterprise Applications.
Select Passport application
In the All applications list, select Iru Passport Web Login or whatever name you named the App registration in the previous section.
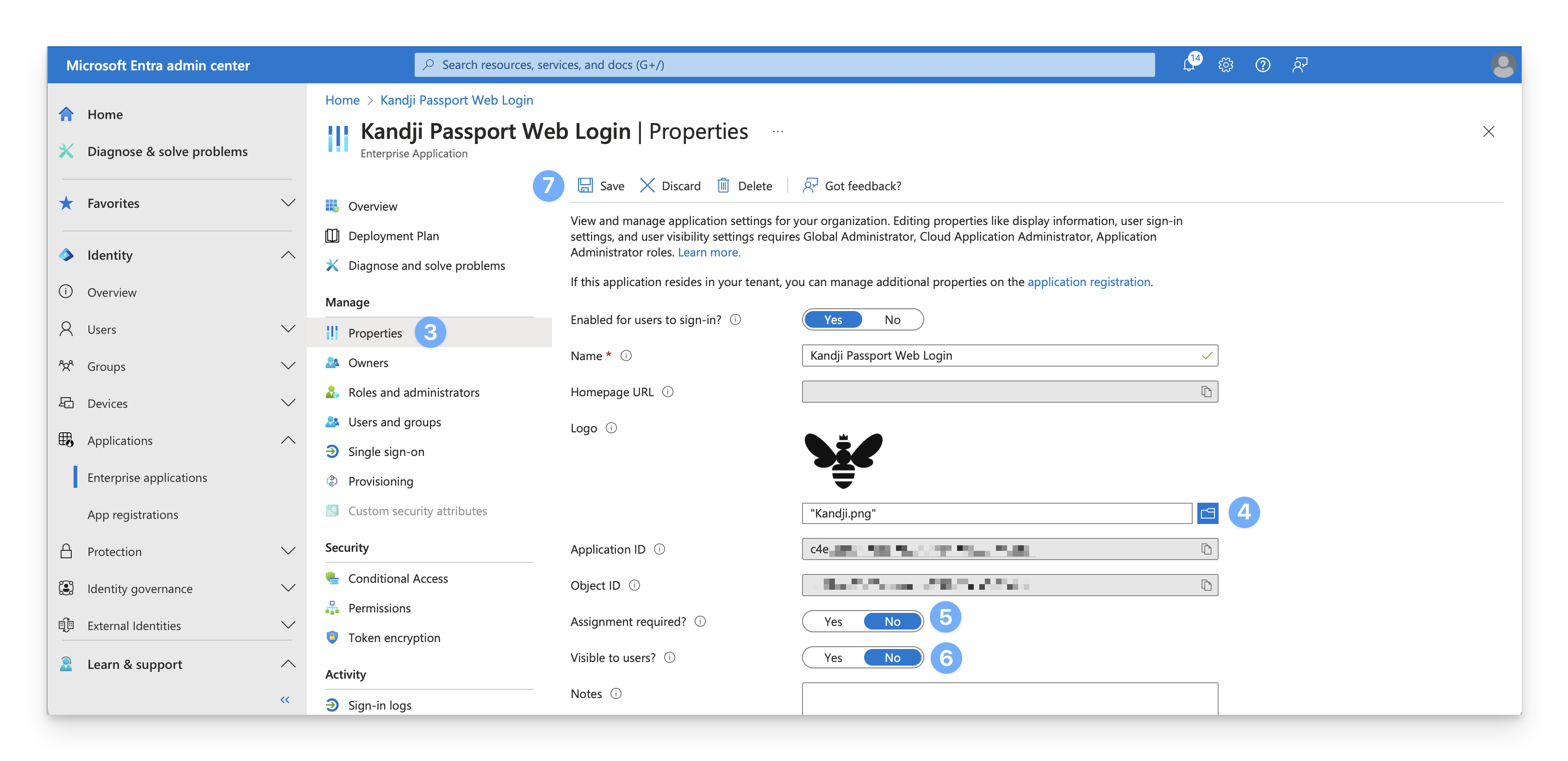
Check assignment requirement
Inspect the Assignment required? setting. If it is set to “No,” then you can skip the rest of this section. All users in Entra ID will be able to use the Passport app.
Configure visibility
Confirm that the Visible to users? setting is set toggled to “No”; otherwise, users will see it in their portal. The Passport app is only useful as a replacement for the macOS login window.
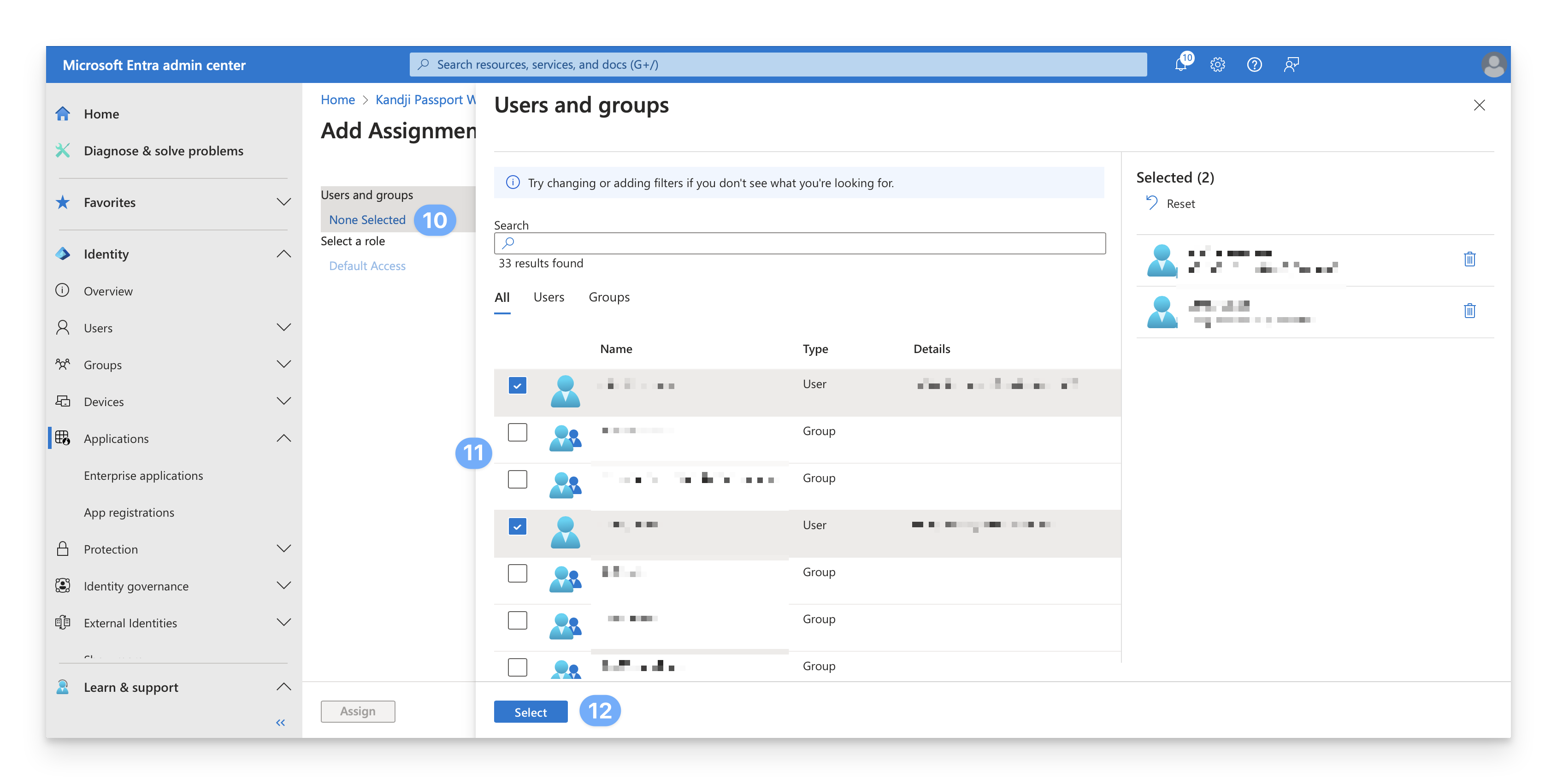
Check if assignment is required
If the Assignment required? setting is set to “Yes,” continue with the following steps.
Choose users and groups
A list of users and security groups is displayed. You can search for a specific user or group or select multiple users and groups that appear in the list.
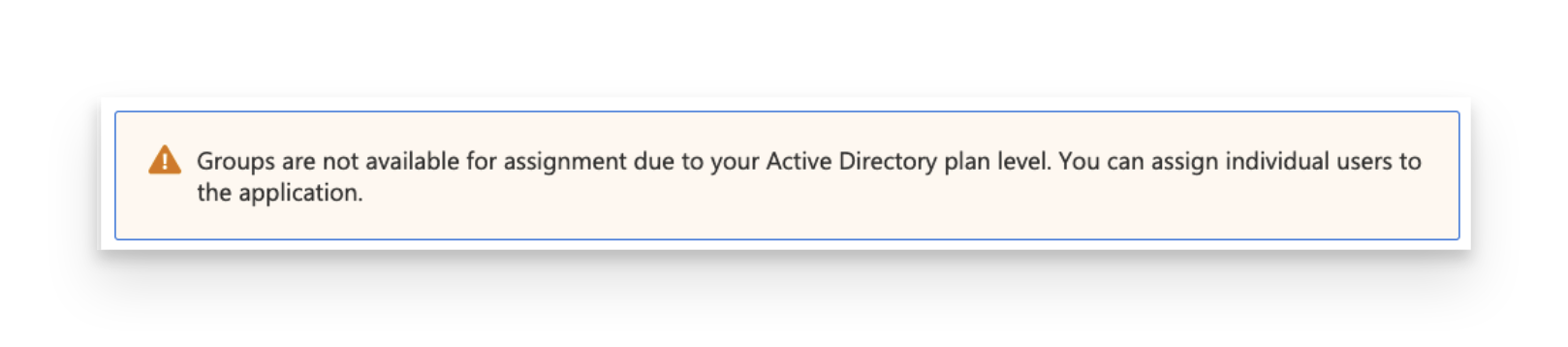
If you see the message below, it means that a free tier is being used. You can only add users (not groups) to the Passport Enterprise App.
User Account Provisioning via Passport
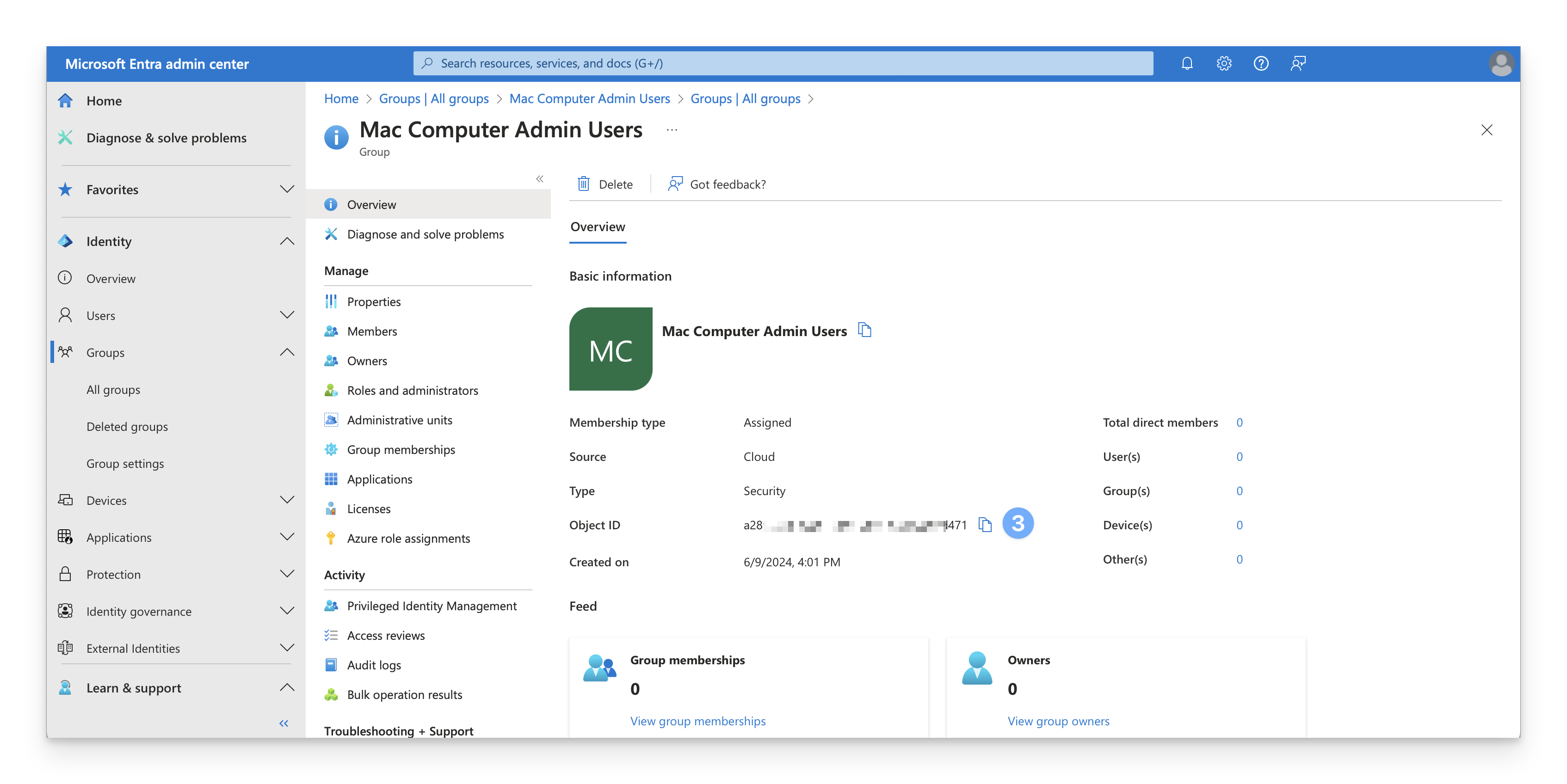
If you use Specify per identity provider group option in the Passport Library Item, use the Entra ID group ObjectID in the Identity provider group field.
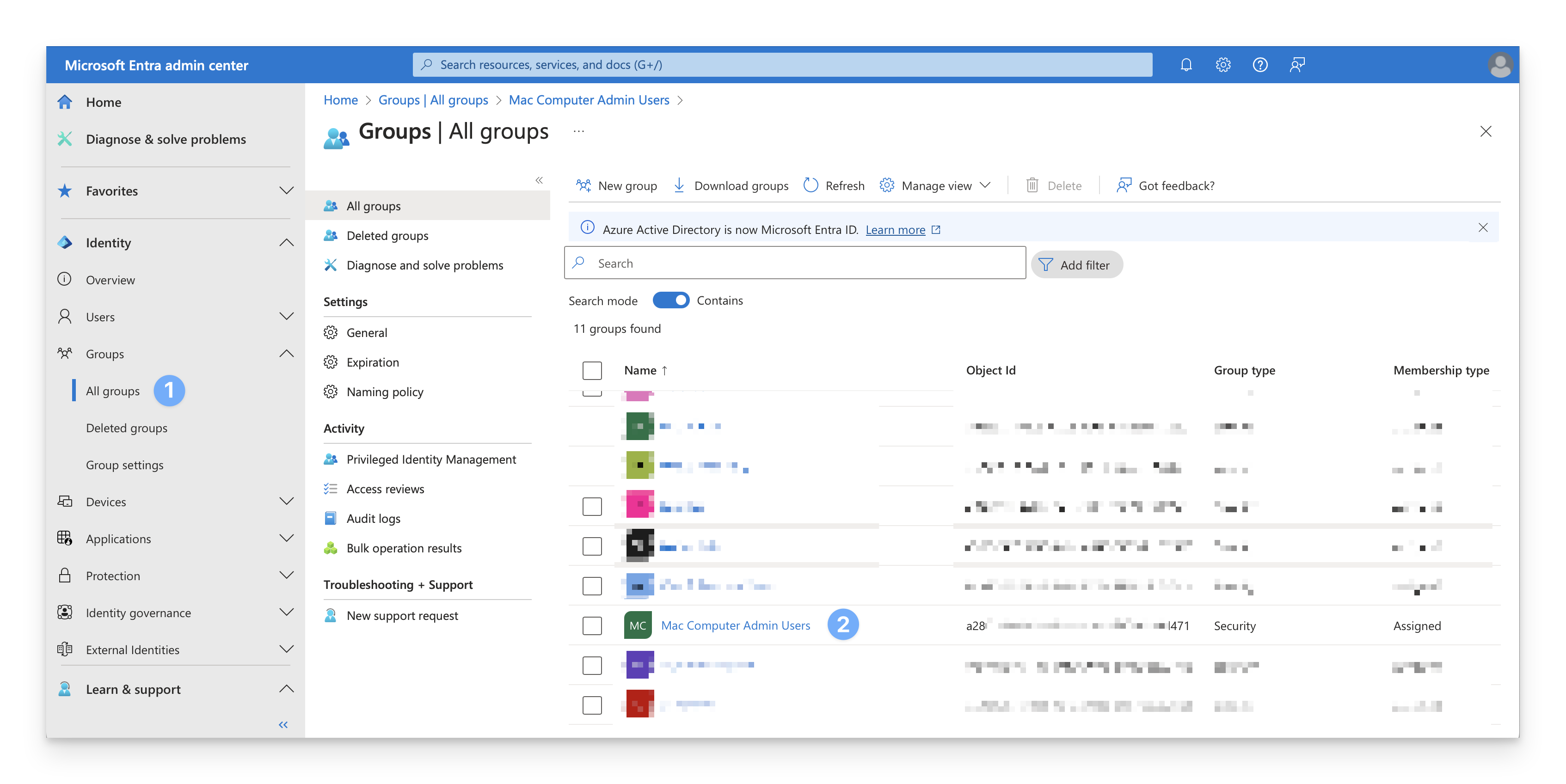
Access Groups
Sign in to the Microsoft Entra admin center. In the Identity navigation menu on the left, open Groups and select All groups.
Configure Passport Library Item
In the Iru Endpoint Passport Library Item, in the User Provisioning section, paste the value from the previous section into the Identity provider group field.
Repeat for additional groups
Repeat the previous steps for each additional Entra ID group you want to use.
Other Considerations
- If you are setting the default account type to standard user, only add administrator account types in the Identity provider groups. Unless otherwise specified as administrators in your Identity provider groups, all users will be created as standard users by default.
- If you are setting the default account type to administrators, only add standard account types in the Identity provider groups. All users will be created as administrators by default unless otherwise specified as standard users in your Identity provider groups.