This guide applies to Mac computers
About Passport with Google Workspace
Passport with Google Workspace enables users to log into Mac computers using their Google Workspace credentials. This integration provides seamless authentication using your organization’s Google identity system.How It Works
Passport integrates with your Google Workspace instance using Secure LDAP to authenticate users at the macOS login screen. When users enter their Google Workspace credentials, Passport verifies them against your Google directory and creates or updates the local Mac user account.Prerequisites
- Your organization’s Google Workspace instance needs to support Secure Lightweight Directory Access Protocol (LDAP). Google has a list of supported licenses for the LDAP service here.
- You need access to your organization’s super administrator account.
- If your web browser automatically uncompresses .zip files, temporarily change that setting and download the file again, or compress the uncompressed folder before you upload it to your Passport library item.
Create a Secure LDAP Client and Download the Certificate
Passport uses Secure LDAP to communicate with Google to confirm login credentials and gather basic user and group information. When you create a new Secure LDAP client in Google Workspace, you’ll download a certificate to secure communications and turn the service on.Sign in to Google Admin console
In a web browser, use your organization’s super administrator account to sign in to your organization’s Google Admin console at admin.google.com.
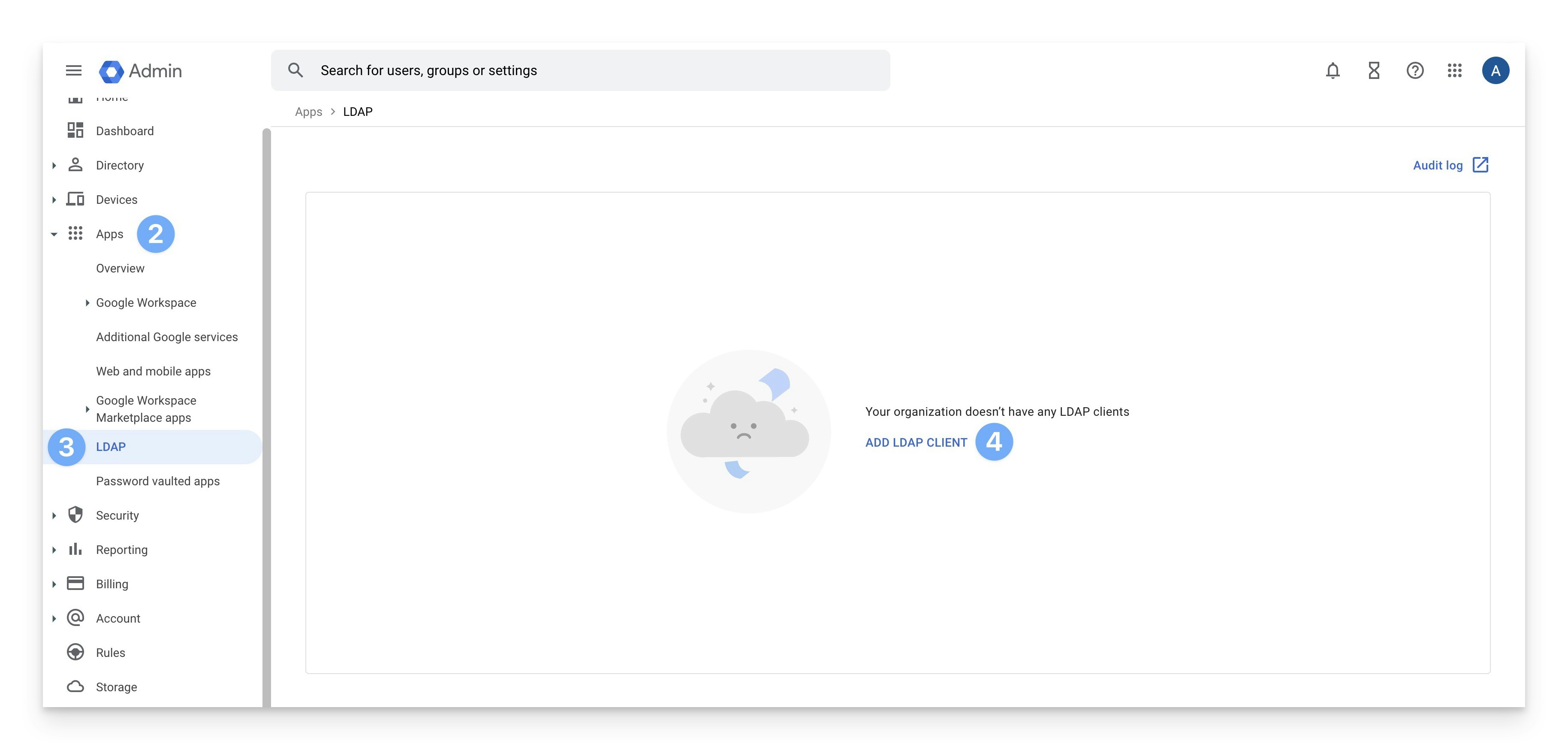
Access LDAP
In the Apps section, click LDAP (if LDAP does not appear, it’s possible that your organization has the Business Starter or Business Standard editions of Google Workspace, which does not offer Secure LDAP service).
Enter description
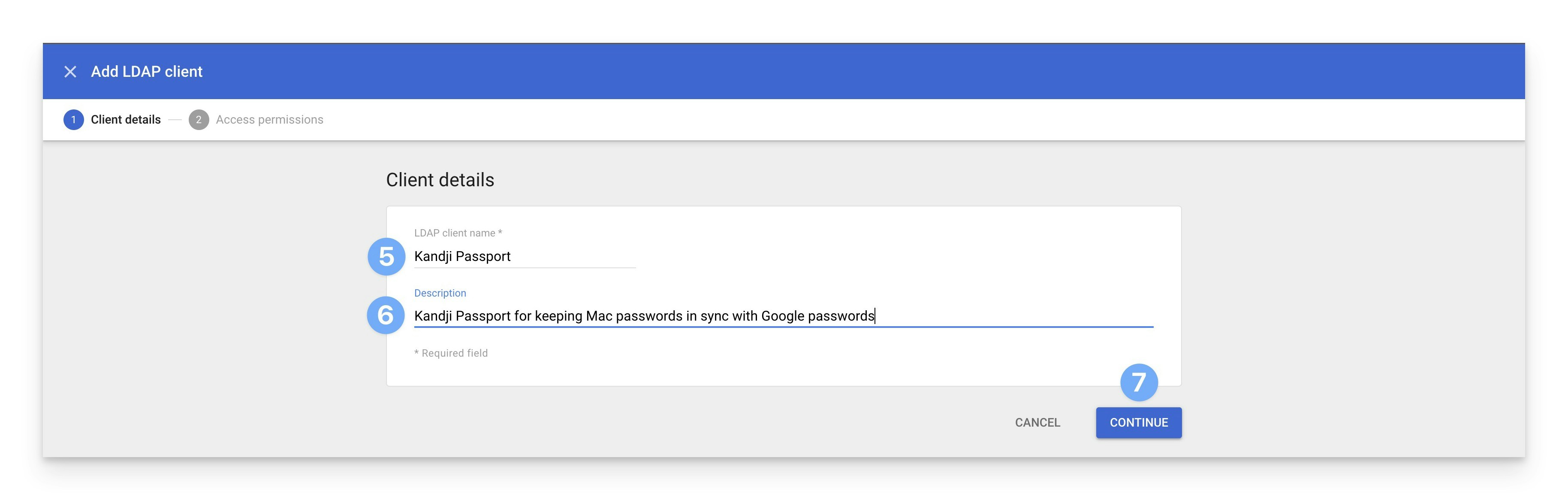
In the Description field, enter a description like Iru Passport for keeping Mac passwords in sync with Google passwords.
Configure user credentials verification
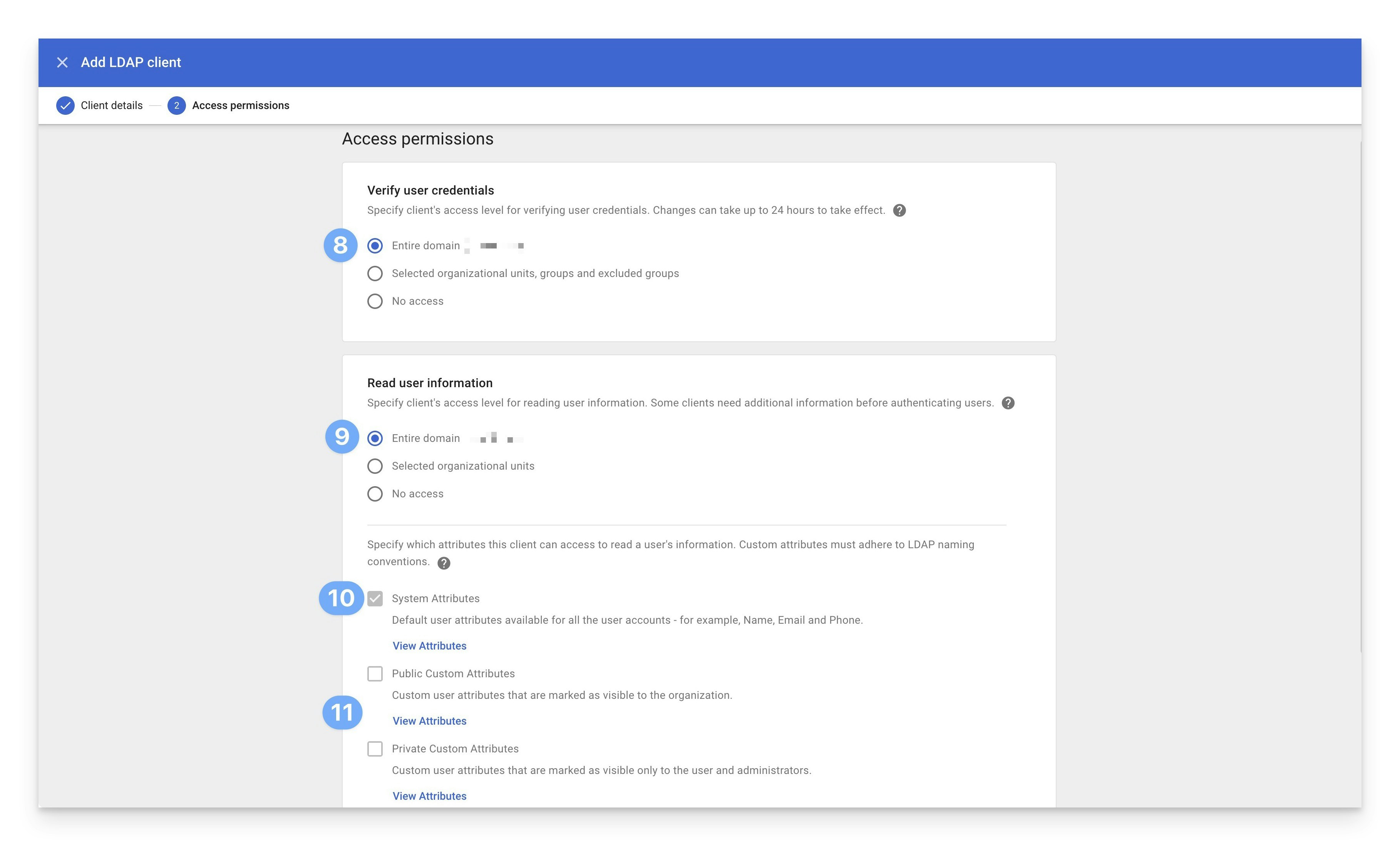
In the Verify user credentials section, select either Entire domain, or if you want to limit Passport to certain accounts, select Selected organization units, groups, and excluded groups.
Configure user information reading
In the Read user information section, configure the same settings as you did in the previous step.
Enable System Attributes
Confirm that the checkbox for System Attributes is selected so that Passport can read the default user attributes.
Configure group information reading
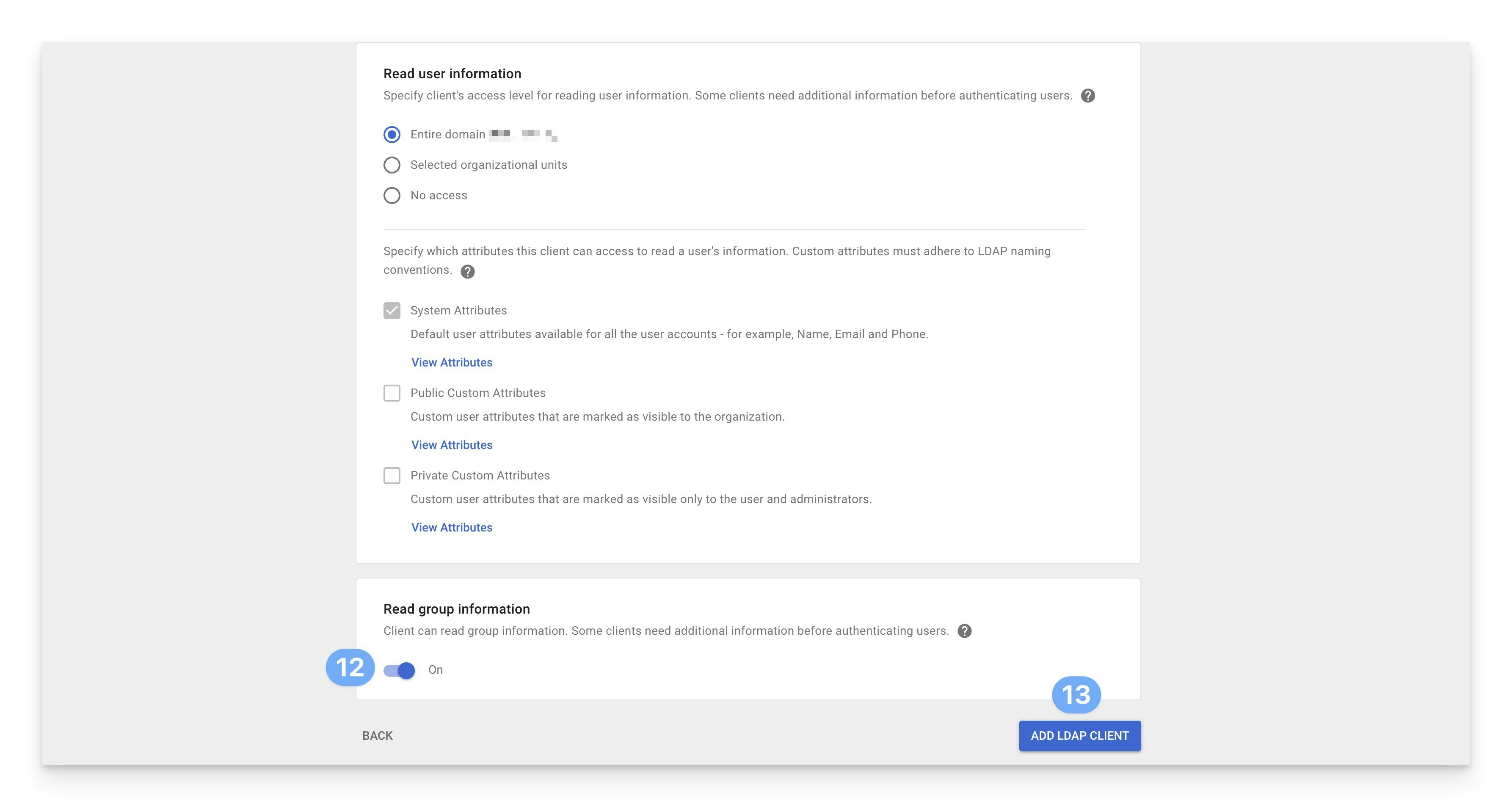
In the Read group information section, turn the slider to On so you can configure Passport to use a user’s Google Workspace group information to dynamically convert their local Mac account between standard and administrator privileges when they log in. You can turn this option on later if you don’t turn it on now.
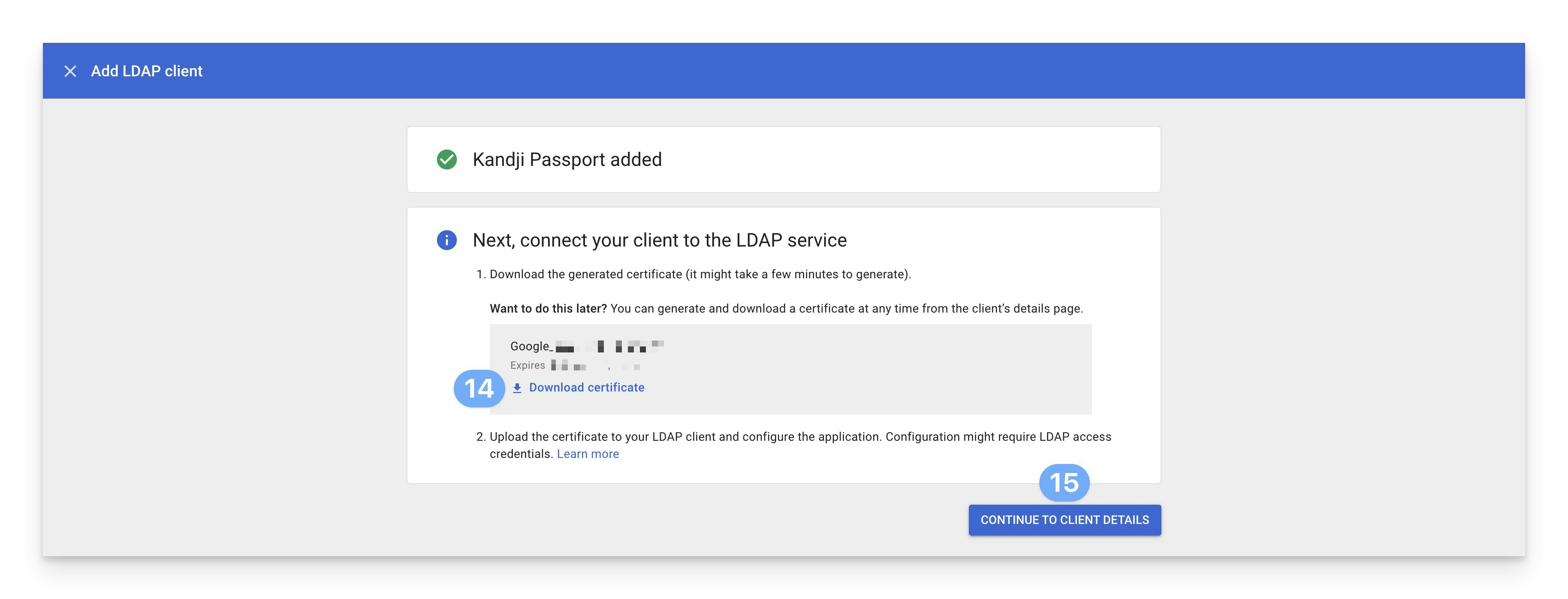
Access service settings
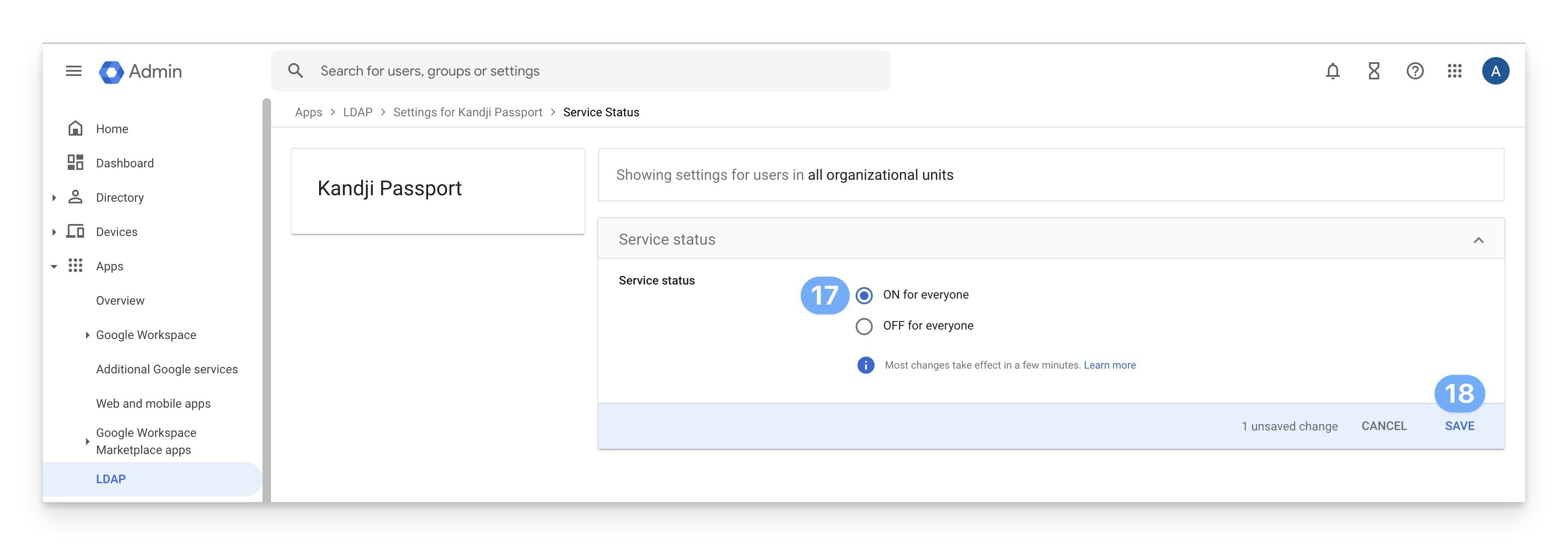
In the upper-right corner, click Off or the disclosure triangle to get to the screen where you can turn on the service.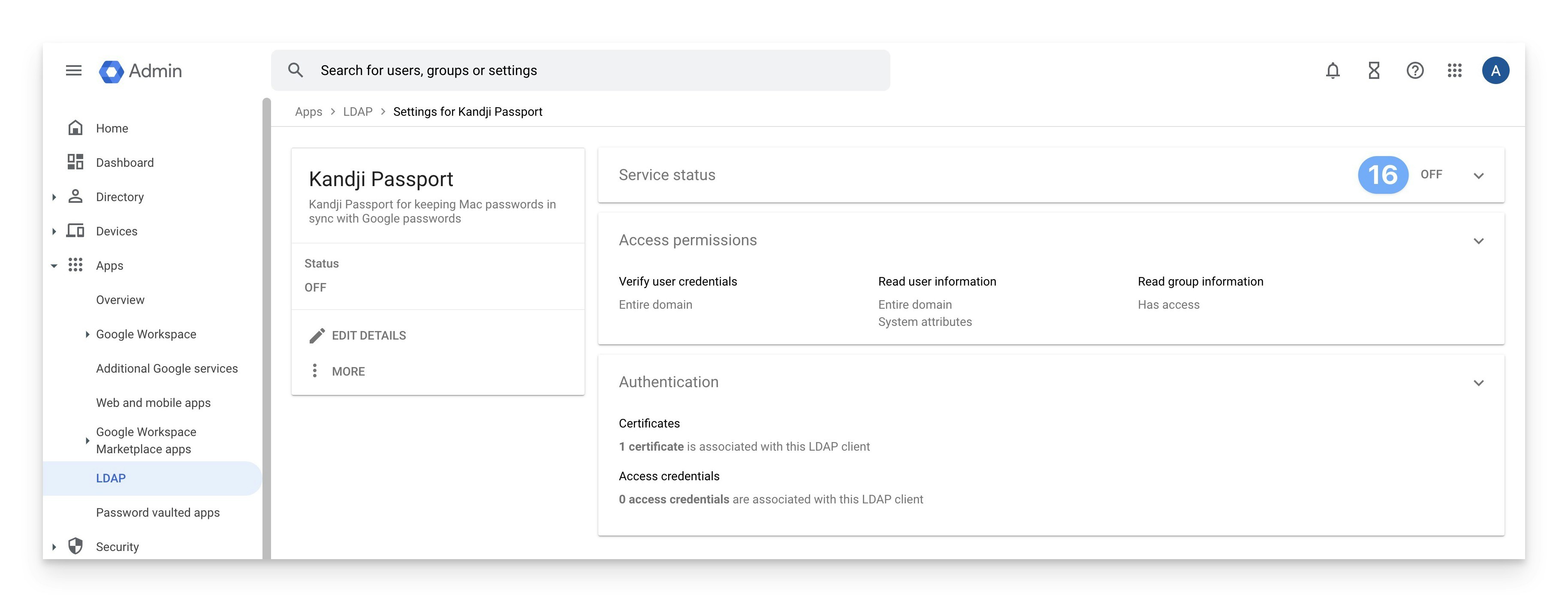

Re-download Your Secure LDAP Certificate (optional)
After you configure the LDAP client in the previous section, you can always download the certificate that’s used to secure the LDAP communication between Passport and Google. There are many other options, including renaming a certificate, generating additional certificates, and deleting a certificate.Sign in to Google Admin console
In a web browser, use your organization’s super administrator account to sign in to your organization’s Google Admin console at admin.google.com.
Select LDAP client
In the list of LDAP clients, select the LDAP client you created for use with Passport.
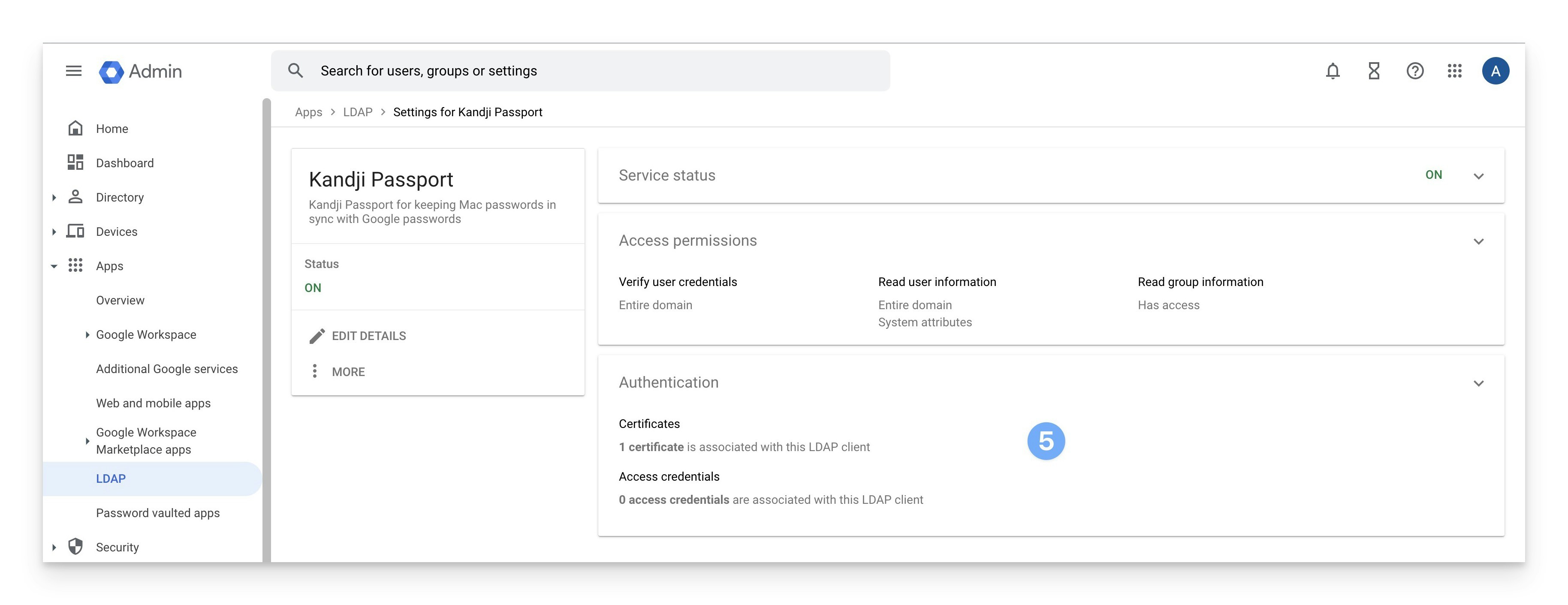
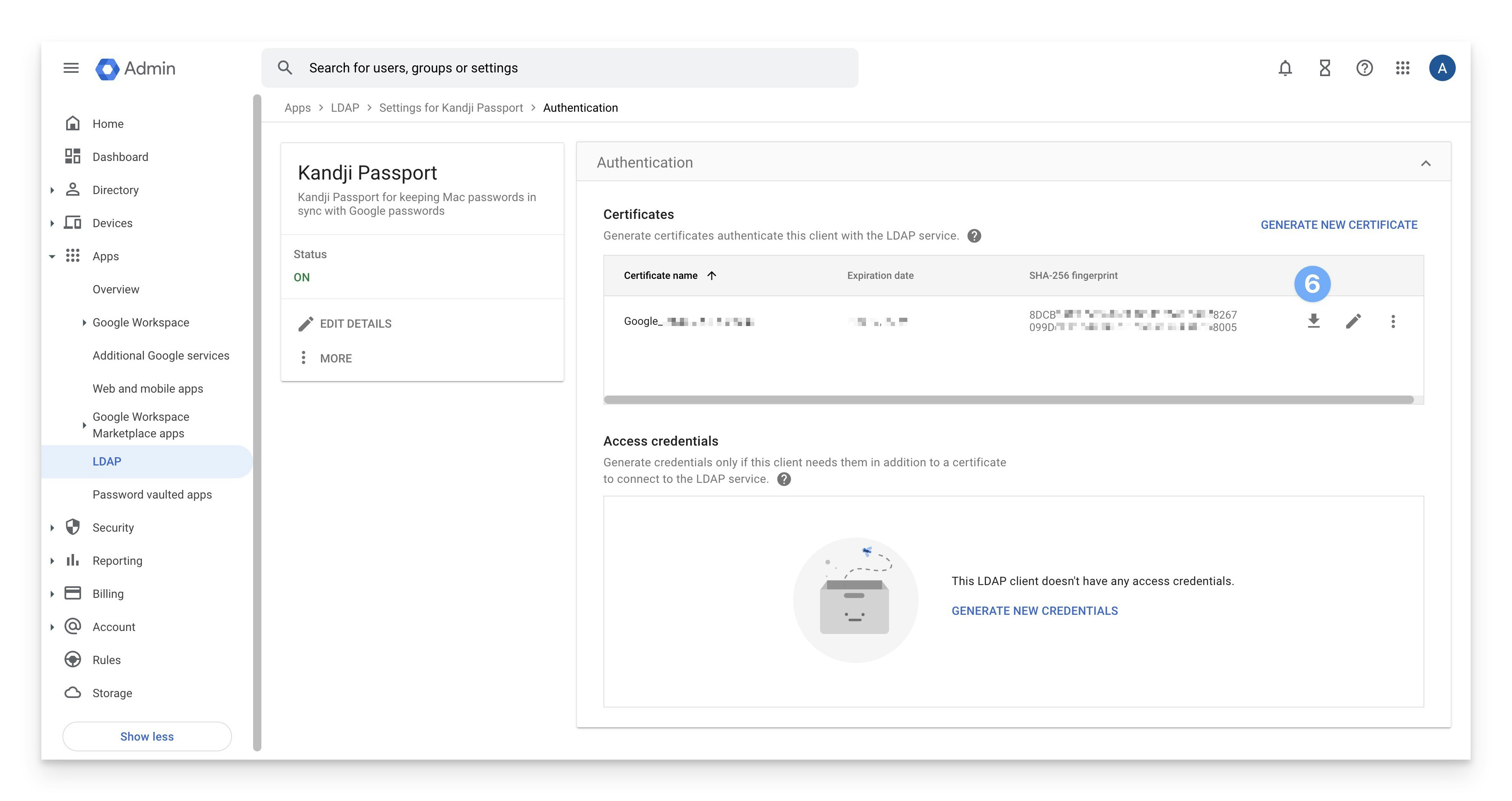
- You can leave the Access credentials section blank; Passport doesn’t use them in addition to the certificate.
User account provisioning via Passport
If you use Specify per identity provider group option in the Passport Library Item, use the Google group email in the Identity provider group field.
Paste email prefix in Passport
In the Iru Endpoint Passport Library Item, in the User provisioning section, paste the email prefix from the previous section into the Identity provider group field.
Repeat for additional groups
Repeat the previous steps for each additional Google group email you want to use.
Library Item Configuration
Provide the certificate that you downloaded from Google Workspace.Select Google Workspace identity provider
In the Settings section, in the Authentication configuration section, click Identity provider and select Google Workspace.
Upload certificate
In the Upload certificate from Google Workspace field, click the link to upload the certificate you downloaded from Google.
Select certificate file
In the Choose Files to Upload window, navigate to the folder that contains your compressed certificate file and select the compressed certificate file.
Wait for validation
If you see the Validating file message, wait a few moments for the validation to complete.





