About Accessory & Storage Access Library Item
Iru Endpoint’s Accessory & Storage Access Library Item allows you, as the device or security administrator, to define access privileges and controls for external storage volumes, server volumes, and DMG file types on Mac computers.How It Works
The Accessory & Storage Access Library Item provides granular control over storage device access on managed Mac computers. It allows administrators to configure access privileges for external storage devices, disk images, and server volumes, with options for encryption requirements, password protection, and user-specific access controls.Adding an Accessory & Storage Access Library Item
To add this Library Item to your Iru Endpoint Library, follow the steps outlined in the Library Overview article.Assign to Blueprints
Assign to your desired Blueprints.
Configuring External Volumes
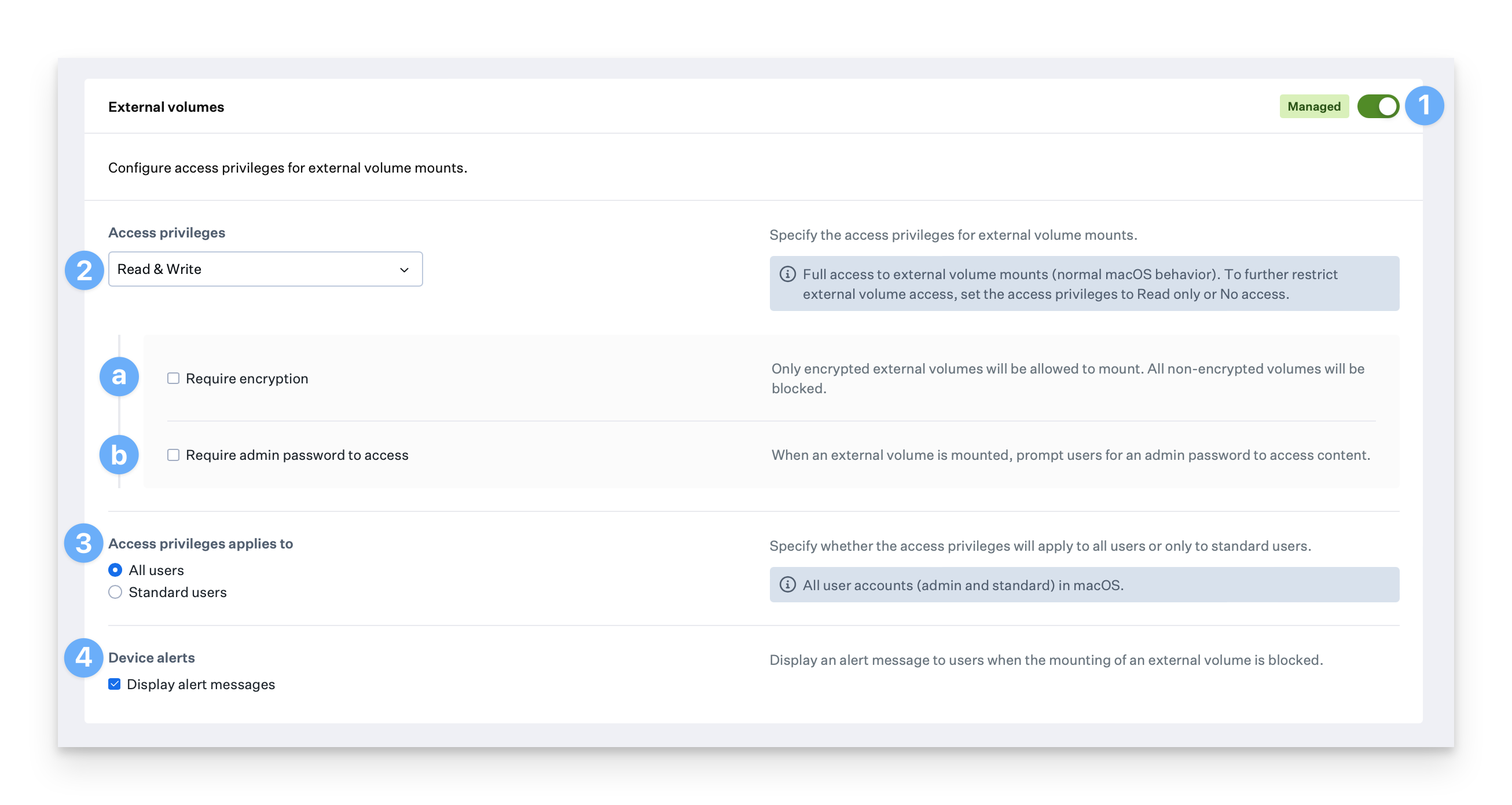
The External volumes section allows you to manage access privileges for external storage devices such as USB, CD, and DVD drives connected to the accessory port and memory cards (SD, SDXC) inserted in the SD card slot. To manage access for external volumes, follow the steps below.Configure Access Privileges
From the Access privileges menu, select the desired access privileges for external volumes. The available options are: Read & Write, Read only, or No access.
Set Encryption Requirements
Optionally, select Require encryption to ensure only encrypted volumes are mounted. For information about using Disk Utility to encrypt storage devices, see this Apple support article.
Configure Password Protection
Optionally, select Require admin password to access to prompt users for an admin password to access content.
Set User Scope
Select All users to apply the access privileges to all users, including admin, or select Standard users to apply the access privileges only to standard users.
Configuring Disk Images
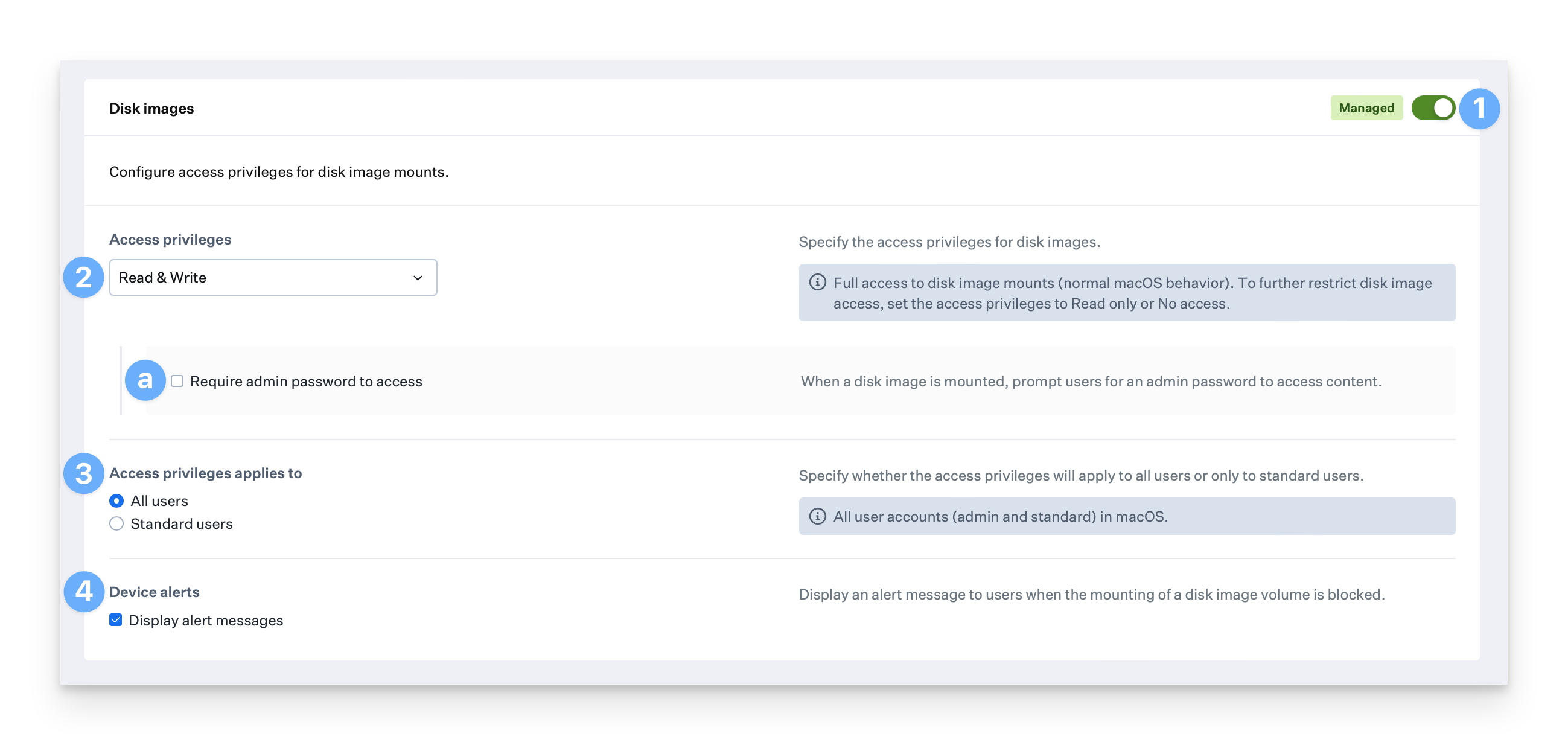
The Disk images section allows you to manage access privileges for DMG file types. To manage access for disk images, follow the steps below. Disk image settings specified here will apply to all DMG mounts on the device, including those in scripted automated workflows and in-app DMG mounts such as Google Chrome’s Auto Update Agent.Configure Access Privileges
The Access privileges menu allows you to select the desired access privileges for disk images. The available options are: Read & Write, Read only, or No access.
Set Password Protection
Optionally, select Require admin password to access to prompt users for an admin password to access content.
Set User Scope
Select All users to apply the access privileges to all users, including admin, or select Standard users to apply the access privileges only to standard users.
Configuring Server Volumes
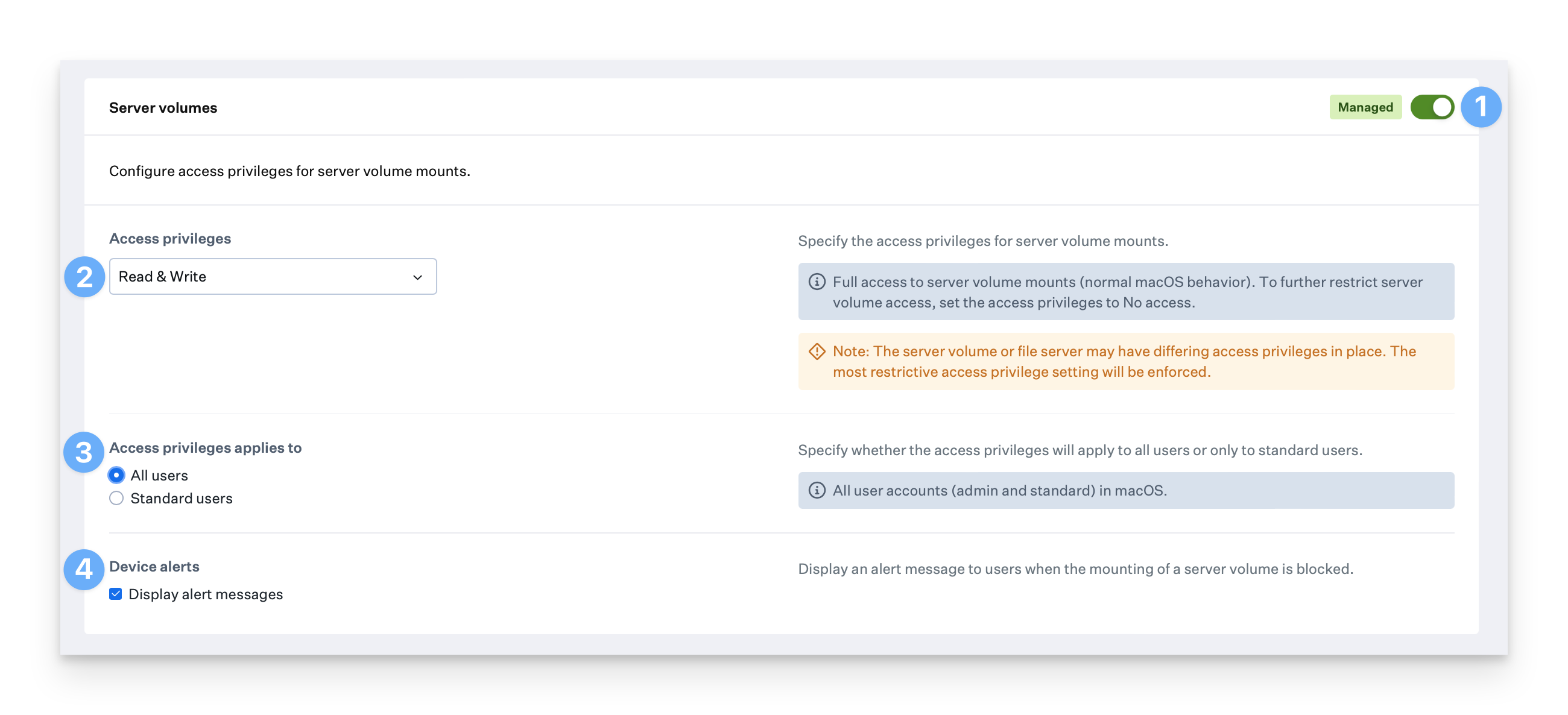
The Server volumes section allows you to manage access privileges for server volume mounts such as SMB shares. To manage access for server volumes, follow the steps below.Configure Access Privileges
Choose the desired access privileges for disk images from the Access privileges menu. The available options are: Read & Write or No access.
Set User Scope
Select All users to apply the access privileges to all users, including admin, or select Standard users to apply the access privileges only to standard users.
Configure Alert Messages
Optionally, select Display alert messages to display alert messages to users when the mounting of external volumes is blocked.
Understanding Restricted Mode on Apple Silicon
On a Mac with Apple silicon running macOS 13+ and depending on the device’s Privacy & Security settings, when new or unknown USB accessories are used, the user may get an alert asking whether or not the USB accessory should be allowed to connect. This is known as Restricted Mode on macOS and is independent of Device alert settings in this Library Item. Restricted Mode can be managed with the Allow USB accessories while device is locked setting in the Restrictions Library item. See this Apple support article for more details.Considerations
- EDR Requirement: The Endpoint Detection & Response add-on is required to use this Library Item, but the EDR Library Item doesn’t need to be assigned to device Blueprints
- Access Privilege Configuration: Configure appropriate access levels (Read & Write, Read only, No access) based on your security requirements and user needs
- Encryption Requirements: Use encryption requirements for external volumes to ensure data protection, especially for sensitive information
- Password Protection: Implement admin password requirements for additional security when accessing external storage devices
- User Scope Management: Choose between All users and Standard users based on your organization’s access control policies
- Alert Configuration: Configure alert messages to inform users when access is blocked, improving user experience and security awareness
- Existing Volume Management: Previously mounted volumes won’t be managed until they are unmounted and re-mounted after Library Item deployment
- Apple Silicon Compatibility: Be aware of macOS Restricted Mode on Apple Silicon devices, which operates independently of this Library Item’s settings
- Disk Image Security: DMG file access controls apply to all disk image mounts, including automated workflows and application updates
- Server Volume Access: Configure server volume access carefully to balance security with legitimate business needs for network storage
- Testing and Validation: Test configuration changes in a controlled environment to ensure they meet security requirements without disrupting workflows
- Regular Review: Periodically review and update access privilege settings to align with changing security policies and business requirements





