About EDR Library Item Configuration
The EDR Library Item is the core component of Iru Endpoint EDR, providing comprehensive threat detection and response capabilities. This library item can be configured with various posture modes, behavioral detection settings, user alerts, and custom allow/block lists to meet your organization’s security requirements.How It Works
EDR Library Item configuration allows you to customize EDR behavior through multiple settings. You can configure posture modes for malware and PUP detection, enable behavioral detection capabilities, set up user notifications, and create custom allow/block lists. These settings determine how EDR responds to threats and provides visibility into security events across your managed devices.Adding an EDR Library Item
To add this Library Item to your Iru Endpoint Library, follow the steps outlined in the Library Overview article.Assign to Blueprints
Assign to your desired Blueprints.
.png?fit=max&auto=format&n=-j5Xd3hg6nX9V7df&q=85&s=5c2589def8806ada9955855382eb76b1)
Configuring General Settings
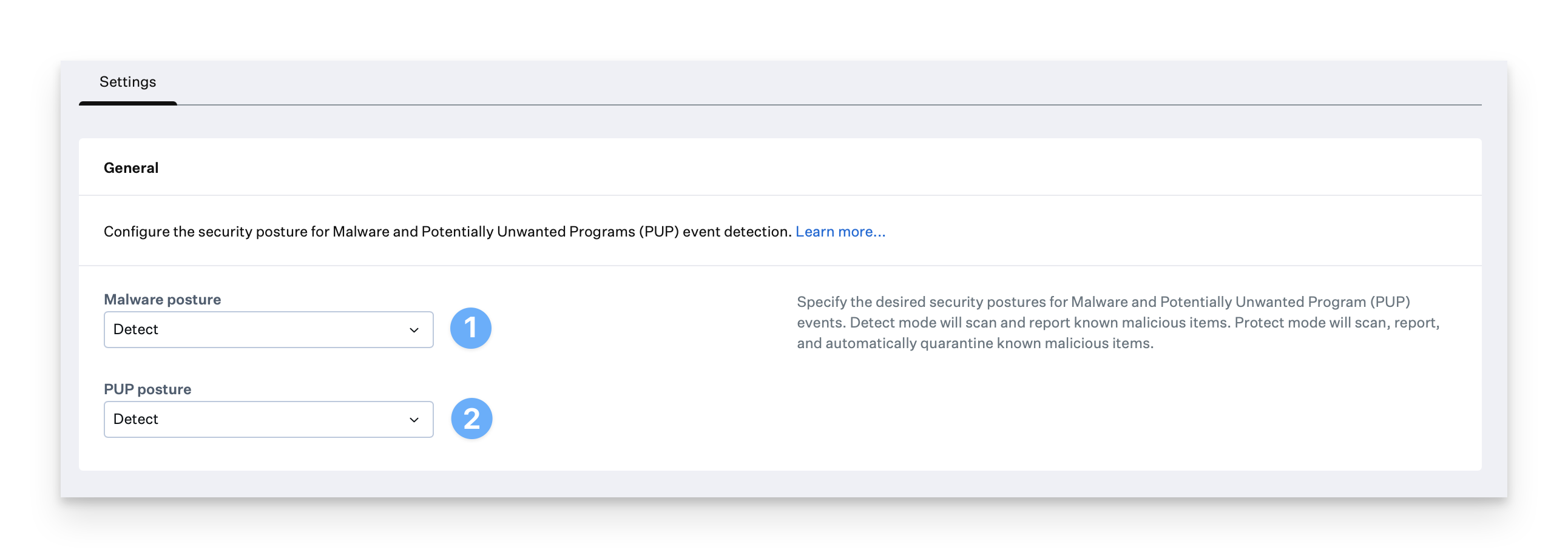
Configure the individual Malware and PUP posture mode preferences for your environment.Detect mode will scan and report known malicious items. Protect mode will scan, report and automatically quarantine known malicious items.
Configuring Behavioral Detections
Behavioral detections are turned on by default when creating and adding a new EDR Library Item to your Library, but can be turned off to suit certain workflows. For existing EDR Library Items, behavioral detections will manually need to be turned on to monitor behavioral activities.
Configuring User Alerts
When turned on, user alerts will notify end users when EDR has quarantined Malware or PUPs on their Mac computers. User alerts are turned on by default but can be turned off to suit certain workflows.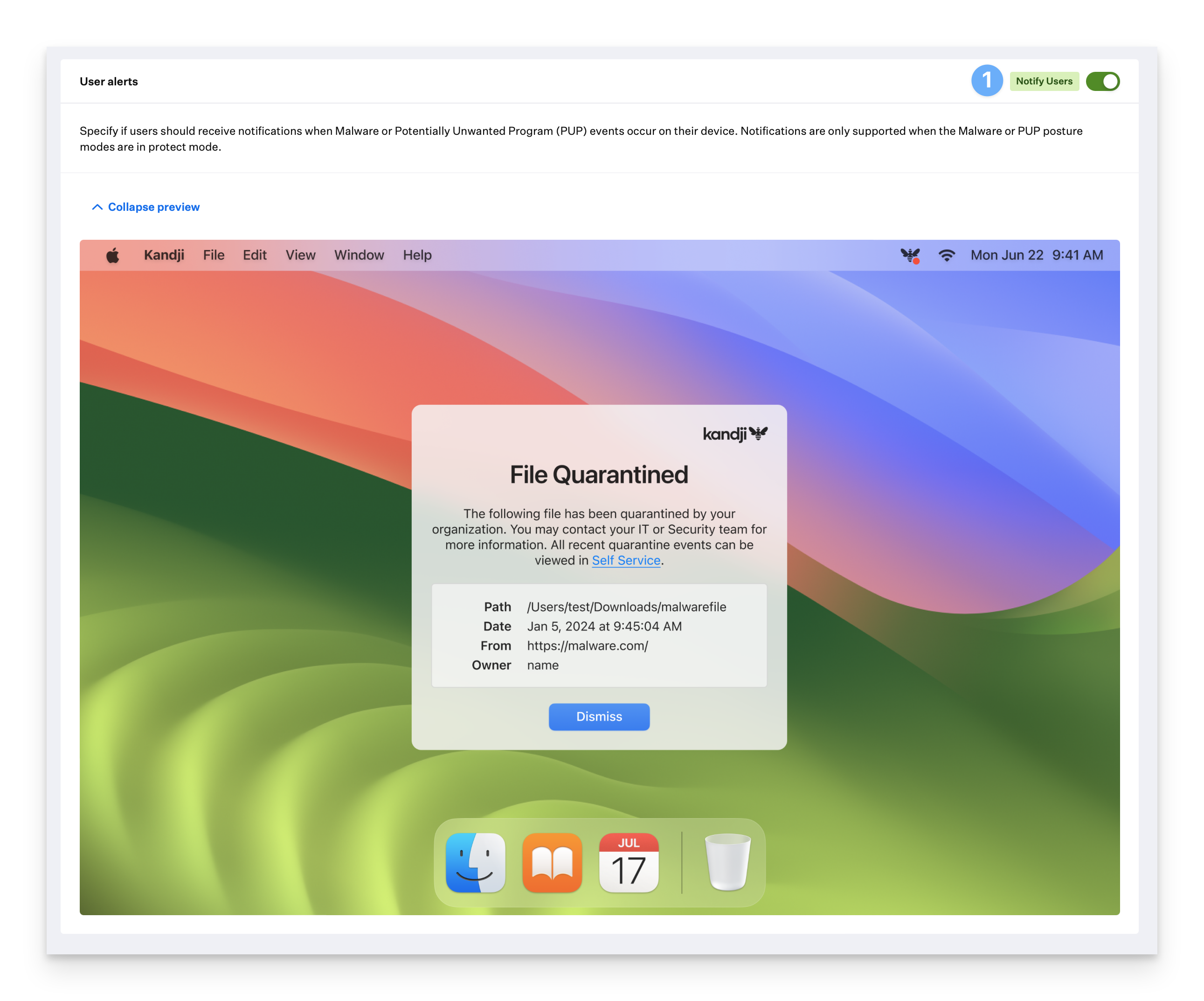
Configuring Allow and Block Lists
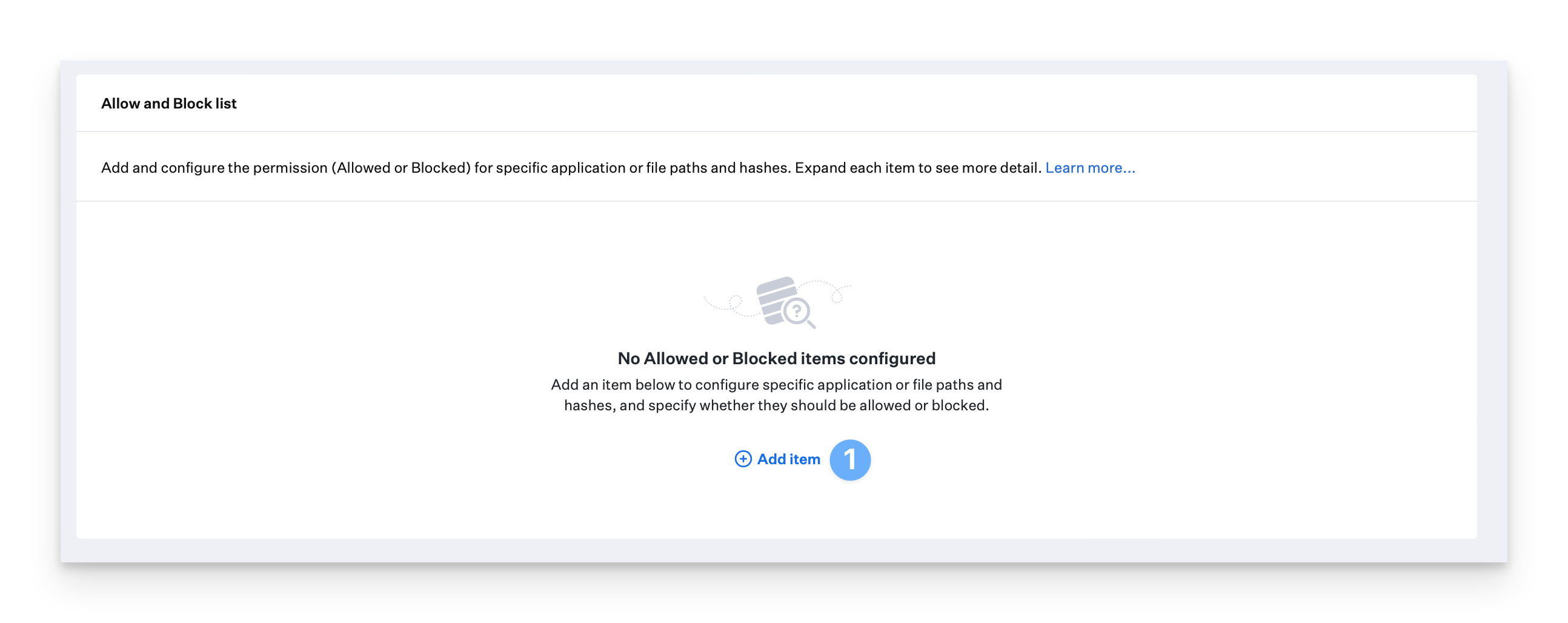
Allow and Block lists can be used to ensure that specific files or applications are always allowed or blocked in your environment regardless of whether or not a file or application is known to be malicious in Iru Endpoint EDR’s threat feeds.Enter Item Information
If Path was selected, enter the application or file path. If Hash was selected, enter the file hash.
Set Item Action
Select Allow to allow a file or application. Select Block to block the file or application.
Add Item to List
Click Add to add the item to the Allow and Block list. Optionally, select the “Add another item” checkbox in the lower-left corner prior to clicking the Add button to add additional items.
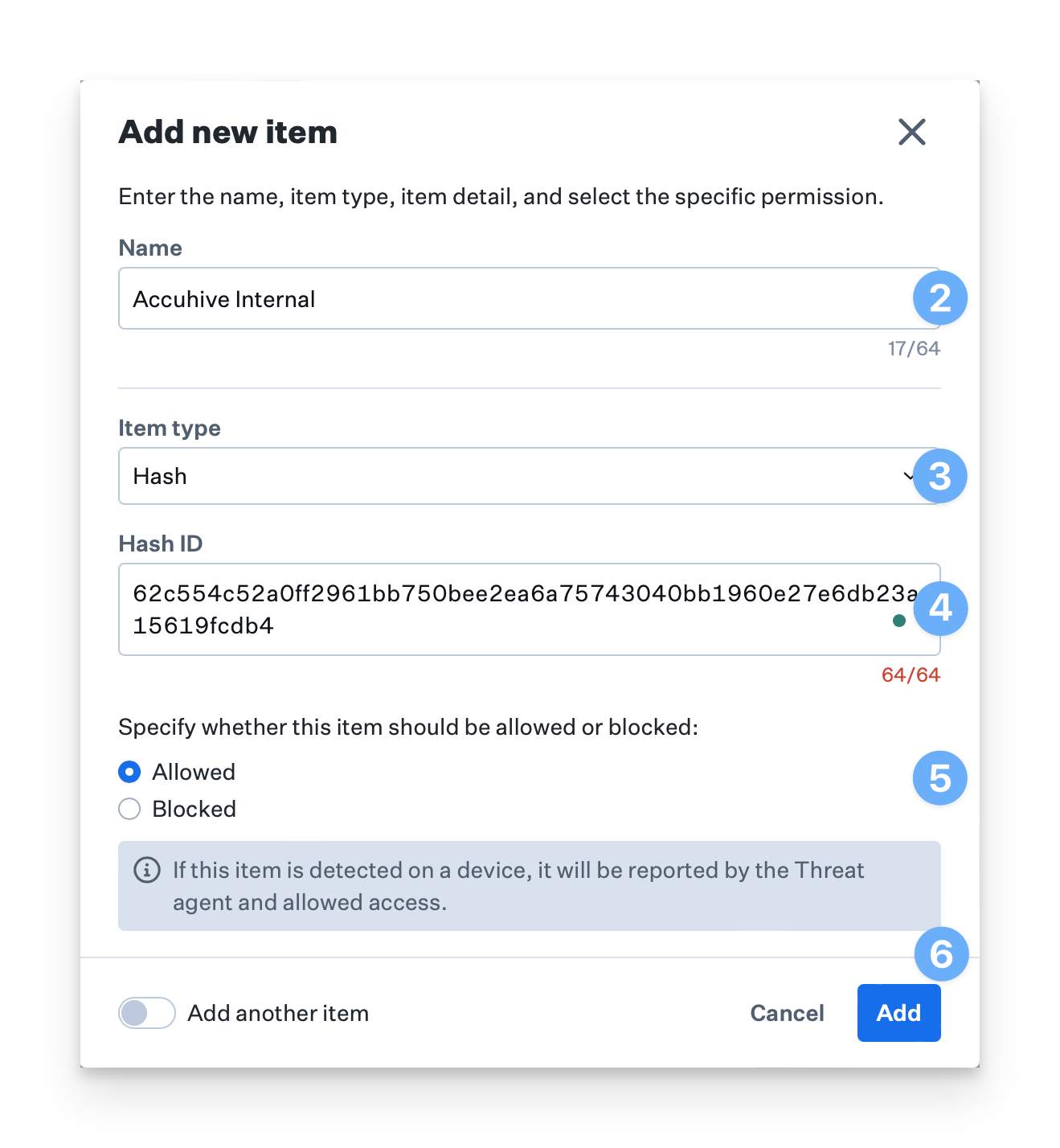
Determine Hash Value
The Hash item type is only supported for files. The Path item type is supported for both files and applications.
Viewing Edit Details in the EDR Library Item
You can audit changes to the EDR Library Item in the Activity tab of the Library Item or the Global Activity section of the Iru Endpoint Web App. This will show what configurations were changed, what the previous state was, and who made the change.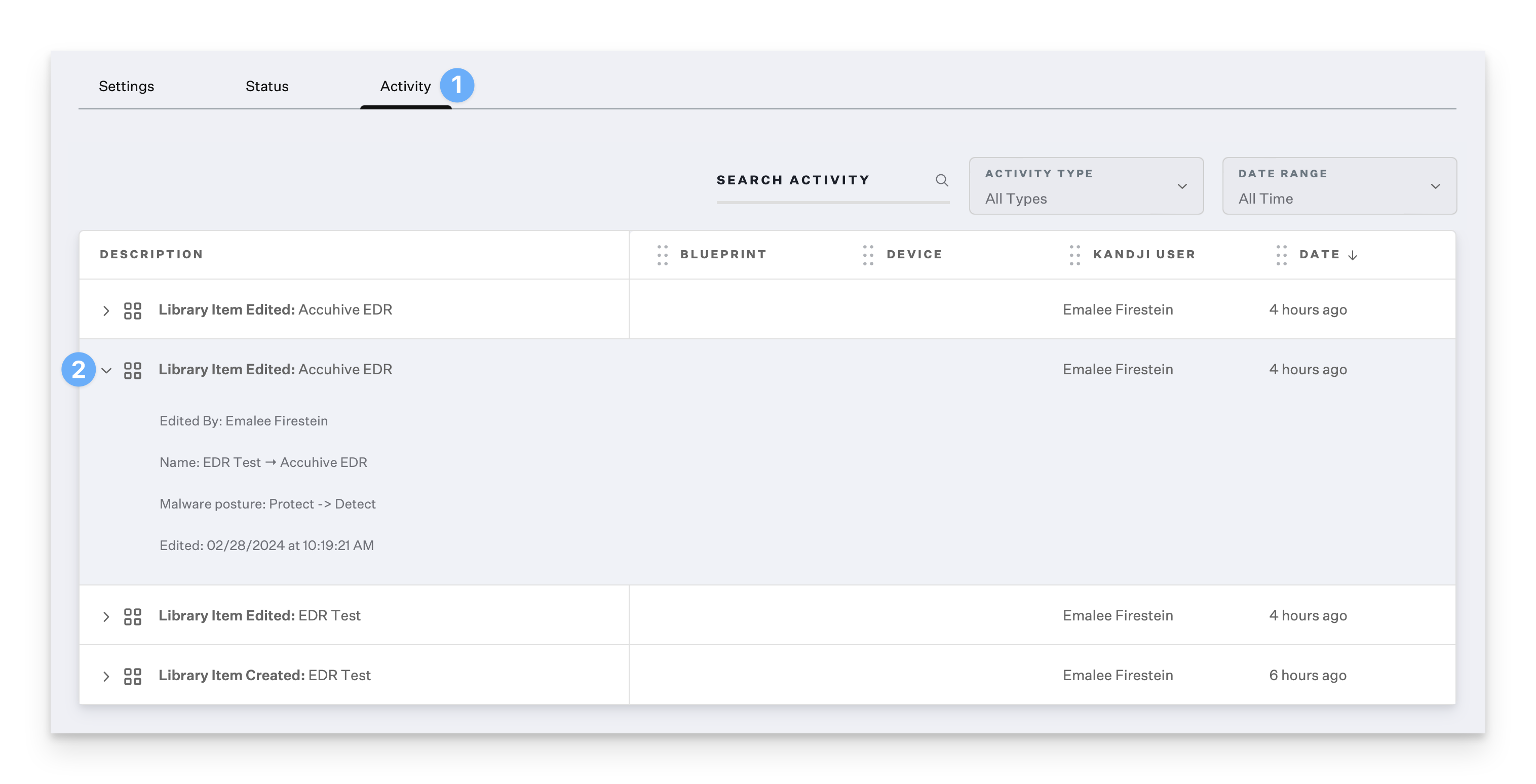
Considerations
- Posture Mode Selection: Choose between Detect and Protect modes based on your security requirements. Detect mode provides visibility without blocking, while Protect mode actively prevents threats
- Behavioral Detection Configuration: Enable behavioral detections for comprehensive threat monitoring, but consider the impact on system performance and false positive rates
- User Alert Management: Configure user alerts to balance security awareness with user experience, ensuring users understand when and why files are quarantined
- Allow and Block List Management: Maintain accurate allow/block lists to prevent legitimate applications from being blocked while ensuring malicious software is properly identified
- Hash vs. Path Configuration: Use hash-based entries for specific file versions and path-based entries for applications that may update frequently
- Regular Review: Periodically review and audit your EDR Library Item configuration to ensure it aligns with current security policies and threat landscape
- Testing and Validation: Test configuration changes in a controlled environment before deploying to production to avoid disrupting legitimate workflows
- Documentation: Keep detailed records of configuration changes and their rationale for compliance and troubleshooting purposes
- Performance Impact: Monitor system performance after configuration changes to ensure EDR doesn’t significantly impact device performance
- Integration Planning: Consider how EDR Library Item settings integrate with other security tools and workflows in your environment





