This guide applies to iOS, iPadOS, and macOS devices
Product Name Update: Throughout this guide, you may notice references to both “Kandji” and “Iru Endpoint.” Our product is now called Iru Endpoint, but some integration interfaces may still display the previous name. This is a temporary situation that will be resolved as our integration partners update their systems.
About Configuring the Okta Verify Library Item
Configuring the Okta Verify Library Item in Iru Endpoint allows you to deploy Okta Device Trust (ODT) to your devices, ensuring required settings, configurations, and resources are applied automatically to devices in scope.How It Works
After configuring the Okta Device Trust (ODT) Integration in Iru Endpoint, the Okta Verify Library item (distributed from ABM or ASM) is used to deploy ODT to your Apple devices. After turning on ODT, required settings, configurations, and resources will be applied to this Library item and deployed automatically to devices in scope.For macOS, the downloadable package of Okta Verify is not compatible with the ODT integration. Okta recommends deploying Okta Verify via Apple Business Manager or Apple School Mananger.
Prerequisites
- The Okta Verify Apple App Store app must be assigned to Iru Endpoint via Apps and Books in Apple Business Manager or Apple School Manager.
Configuring Okta Verify for ODT
Find Okta Verify App
Find and click on the Okta Verify App Store app in the App Store Apps section. You can use the search option to narrow down the results if you have many apps in your Library.
Assign to Blueprints
Assign the Library item to one or more Blueprints. If this is the first time deploying ODT, it is a good idea to deploy to a test blueprint scoped to a limited number of devices so that you can see how it functions when deployed.
Configure Installation Type
For the installation type, choose Install and continuously enforce. If Okta Verify is already installed on some devices, this process will not reinstall the app, but Iru Endpoint will take over the management of the app.
Confirm ODT Activation
You will see a modal letting you know that Managed AppConfig for iPhone and iPad will be disabled in the library item and will be managed by the ODT integration. Click Yes, turn on Okta Device Trust to continue.
Review Configuration
Once turned on, you will see the device families that are configured for ODT and the configured Okta domain.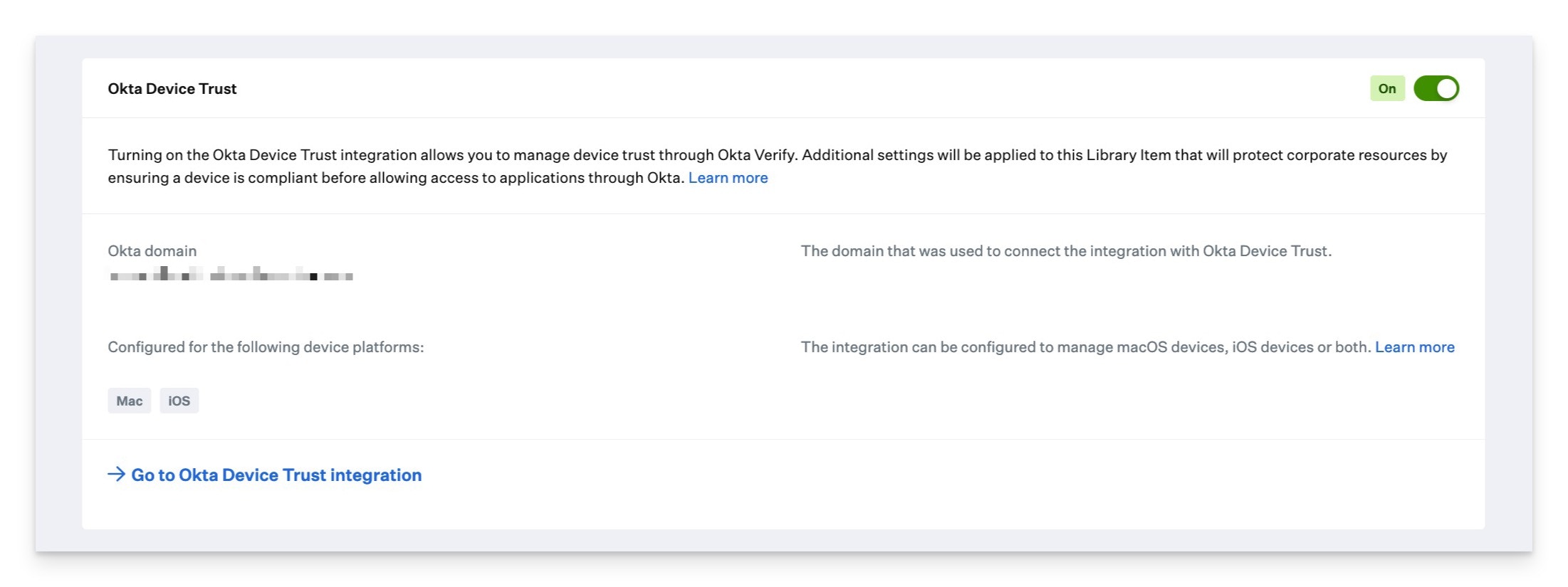

What settings are deployed to devices
Once ODT is set up, enabled, and scoped to your blueprints, the following settings payloads are automatically configured and delivered to Apple devices in the scope of Okta Device Trust in Iru Endpoint.| Payload setting | Platform | Description |
|---|---|---|
| Dynamic SCEP challenge certificate | macOS | This is a unique Okta SCEP certificate per device. The certificate is used in the device registration process and will automatically renew when it expires. |
| OktaVerify.EnrollmentOptions | macOS | Okta Verify SilentEnrollmentEnabled configuration is sent to macOS devices. This will launch Okta Verify automatically if an unregistered device attempts to access Okta resources and prefill the Organization URL for the user. |
| Okta Verify Login item | macOS | This payload adds Okta Verify as a login item on macOS and will start Okta Verify at user login. |
| Managed app config | iOS and iPadOS | This App Config contains the OktaVerify.OrgUrl and device managementHint used to register the device as managed in Okta. |
| SSO Extension payload | macOS, iOS, and iPadOS | The SSO extension forwards requests from the browser or app to Okta Verify, and users do not receive the Open Okta Verify browser prompt. Not supported on Chrome or Firefox. |






 to turn on ODT.
to turn on ODT.