About Behavioral Detection Testing
Behavioral detection testing validates that Iru Endpoint EDR can identify and respond to suspicious or malicious activities in real-time. This testing approach simulates actual attack behaviors to ensure your EDR system is properly configured and functioning as expected.How It Works
Behavioral detection testing uses controlled simulation techniques to trigger EDR responses without posing actual security risks. The testing process involves executing specific commands or scripts that mimic malicious behaviors, allowing you to verify that your EDR system correctly identifies and responds to these activities based on your configured posture modes.Prerequisites
- EDR Library Item Configuration: Ensure that the EDR Library Item has behavioral detections enabled and has been successfully applied to the device by confirming that a green dot is visible next to the EDR Library Item located within the Status tab of a Device Record
Single Detection Testing via Terminal
Expected Results in Detect Mode
When the Malicious behavior response posture in the EDR Library Item is set to Detect mode:-
Iru Endpoint EDR will identify the test as malicious behavioral activity. This will be reported with a status of Detected in both the Threats module (accessible via the left-hand navigation bar) and the Threats tab within a Device Record.
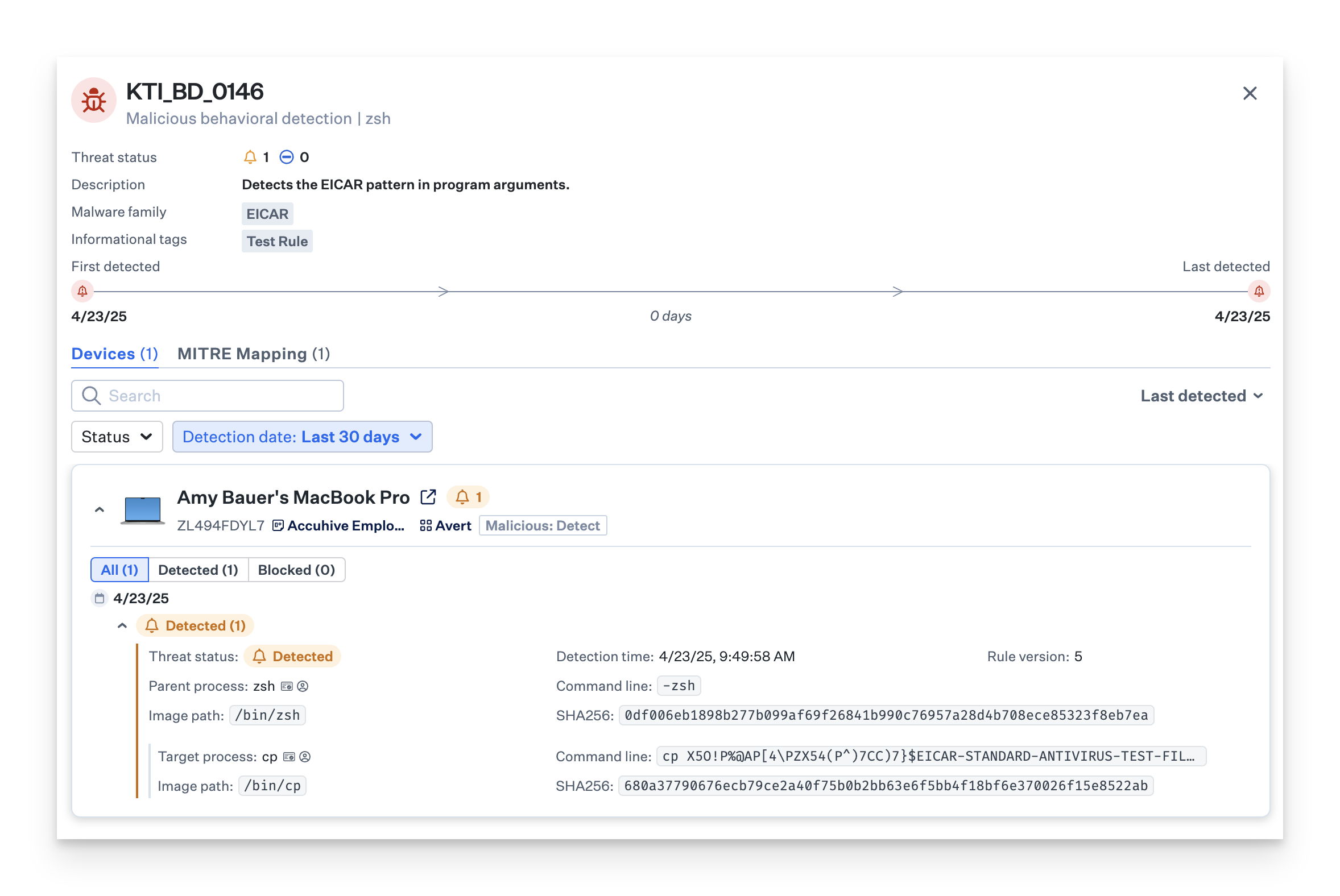
Expected Results in Protect Mode
When the Malicious behavior response posture in the EDR Library Item is set to Protect mode:-
Iru Endpoint EDR will recognize the test as malicious activity and block it. This will be reflected with a status of Blocked in both the Threats module (accessible via the left-hand navigation bar) and the Threats tab within a Device Record.
.png?fit=max&auto=format&n=pt004fUbT6GTF1kl&q=85&s=36c0bfe6f1355fa727fca79f28bb7be1)
Multiple Detection Testing via Attack Simulation Script
Prerequisites
Apple’s Xcode Developer Tools are required to run this script. When you run the script, it will prompt to install Xcode Developer Tools if missing.Download and Execute Script
The following method requires downloading and executing our EDR Test script from GitHub. The script will simulate suspicious behaviors on the device, and the resulting detections will approximate an attack scenario. While there is no danger to executing the script, the Malicious behavior response posture and the PUP response posture in the EDR Library Item should be set to Protect. This will block behaviors simulated by this script and ensures an optimal experience.Download Script
You can either run the following command to download the script, or you can download it from our GitHub repository:
Expected Results in Protect Mode
When the Malicious behavior response posture in the Library Item is set to Protect mode:- Iru Endpoint EDR will recognize the executing behaviors as malicious or suspicious, and either flag or block them
- This will be reflected as seven behavioral detections. These can be found in both the Threats section and the Threats tab within a Device Record in the Behavioral detections tab
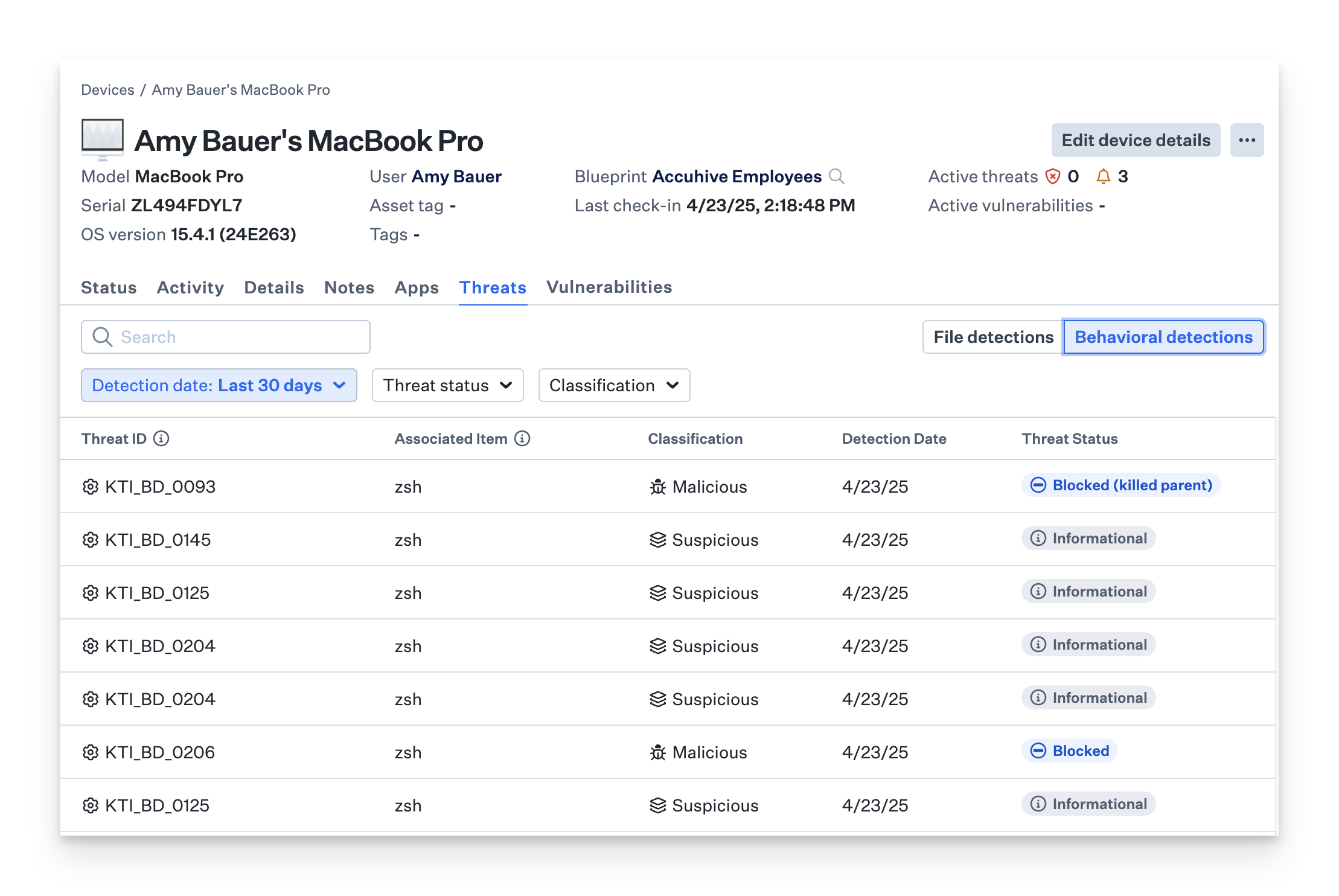
- One file detection will be listed in the File detections tab in the Threats section in the Device Record
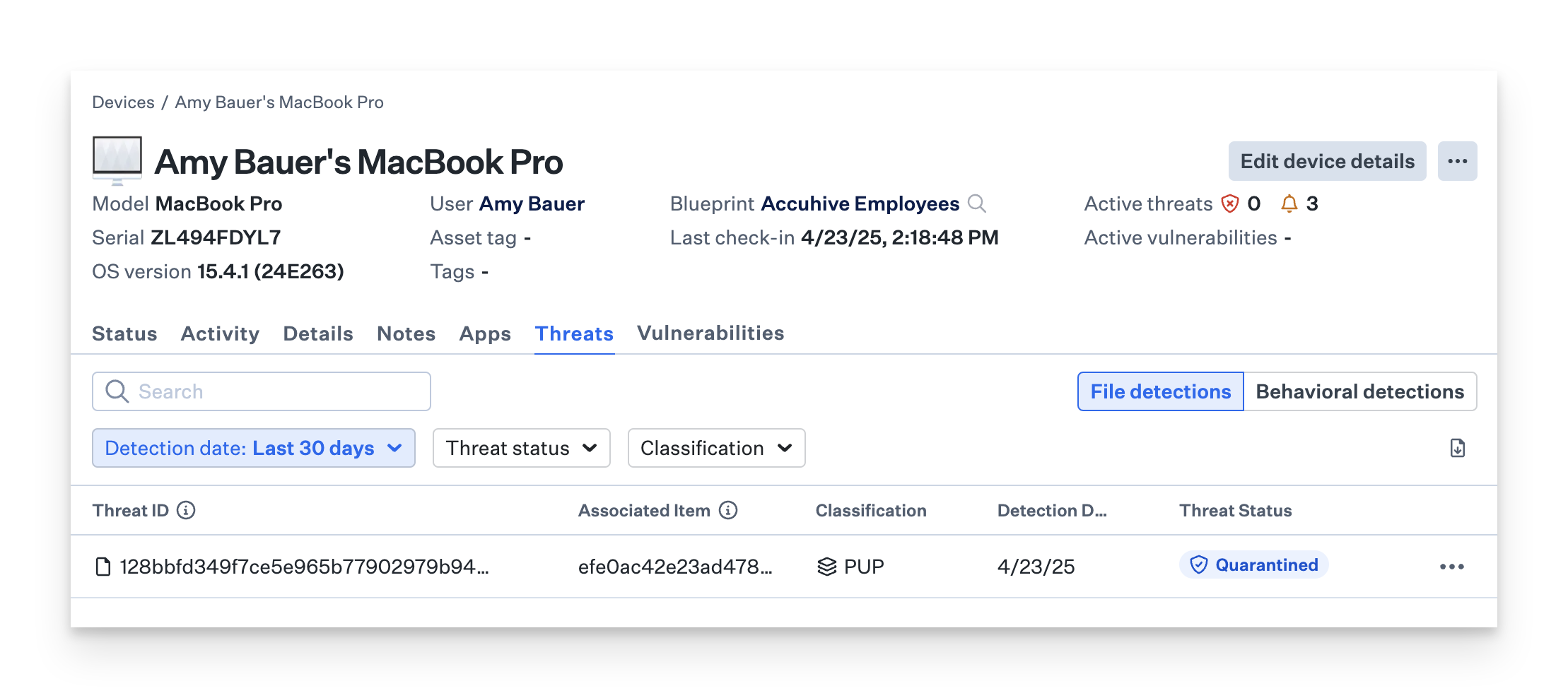
Considerations
- Safe Testing Environment: Both testing methods use controlled, non-malicious techniques that simulate attack behaviors without posing actual security risks
- Posture Mode Validation: Test both Detect and Protect modes to ensure proper behavioral detection configuration and response capabilities
- Real-time Response: Behavioral detections should trigger immediately when suspicious activities are detected, demonstrating real-time protection capabilities
- Comprehensive Testing: Use both single detection and attack simulation methods to validate different aspects of your EDR system’s behavioral detection capabilities
- Script Safety: The attack simulation script is designed to be safe and will not cause actual harm to your system, but always ensure you’re testing in a controlled environment
- Detection Verification: Always verify that behavioral detections appear in both the main Threats module and individual device records to confirm proper detection and reporting
- Regular Testing: Incorporate behavioral detection testing into your regular security validation procedures to ensure ongoing EDR functionality
- Team Training: Use behavioral detection testing as a training tool to help security teams understand threat detection and response workflows
- Performance Impact: Monitor system performance during testing to ensure EDR doesn’t significantly impact device performance during normal operations
- Documentation: Keep records of your behavioral detection testing results as part of your security compliance and audit documentation





