About Security Operations Actions
Security Operations (SecOps) actions are the controls available in an endpoint security or EDR workflow that let administrators review detections and take follow-up steps such as updating status, investigating details, or performing response tasks within the security console. In Iru Endpoint Detection & Response, these actions are surfaced on the Threats page and include updating the detection’s Status to track progress through review and remediation.How It Works
Security Operations actions provide a structured approach to threat management through status tracking and tagging systems. The Status action on the Threats page of Endpoint Detection lets you track and update detection events as you work through them. As an admin, you can manually mark detections as Open or Closed, while Iru Endpoint automatically assigns other statuses based on timing, such as when the detection first occurred or how long it’s been resolved. This creates a consistent workflow that helps you see what’s new, what needs attention, and what’s been handled, making it easier to triage threats and track progress across your fleet. The Status column is available in both File Detection and Behavioral Detection tables..png?fit=max&auto=format&n=UzJ56q8TtGBboKzK&q=85&s=ddbc0fb77316e49b65330f0aa09ea791)
Understanding Detection Status Types
Detection events can have one of four statuses:- New: Occurred within the last 24 hours
- Open: Not yet marked as closed
- Closed: Resolved by manually marking as Closed
- Archived: Closed for more than 30 days
Filtering Detection Events by Status
You can filter detection events by status on the Threats page:- Event filter: By default, shows New, Open, and Closed events. Archived events are hidden unless selected
- Device filter: Located in the side panel, allows filtering devices by Open or Closed detections
Changing Detection Status
Updating statuses regularly helps keep detection lists accurate and improves filtering for active threats.
You can update detections individually or in bulk.
About Threat Organization Tags
Tags provide a flexible way to organize, filter, and manage threats based on your team’s specific operational needs. These admin-defined tags streamline threat management and enhance collaboration by allowing you to categorize detections with custom labels that align with your workflow. The threats page now includes a Tags column, giving you visibility into which tags are associated with each threat. If a threat has multiple tags, you can hover over the column to see the full list.Managing Tags
Creating and Removing Tags
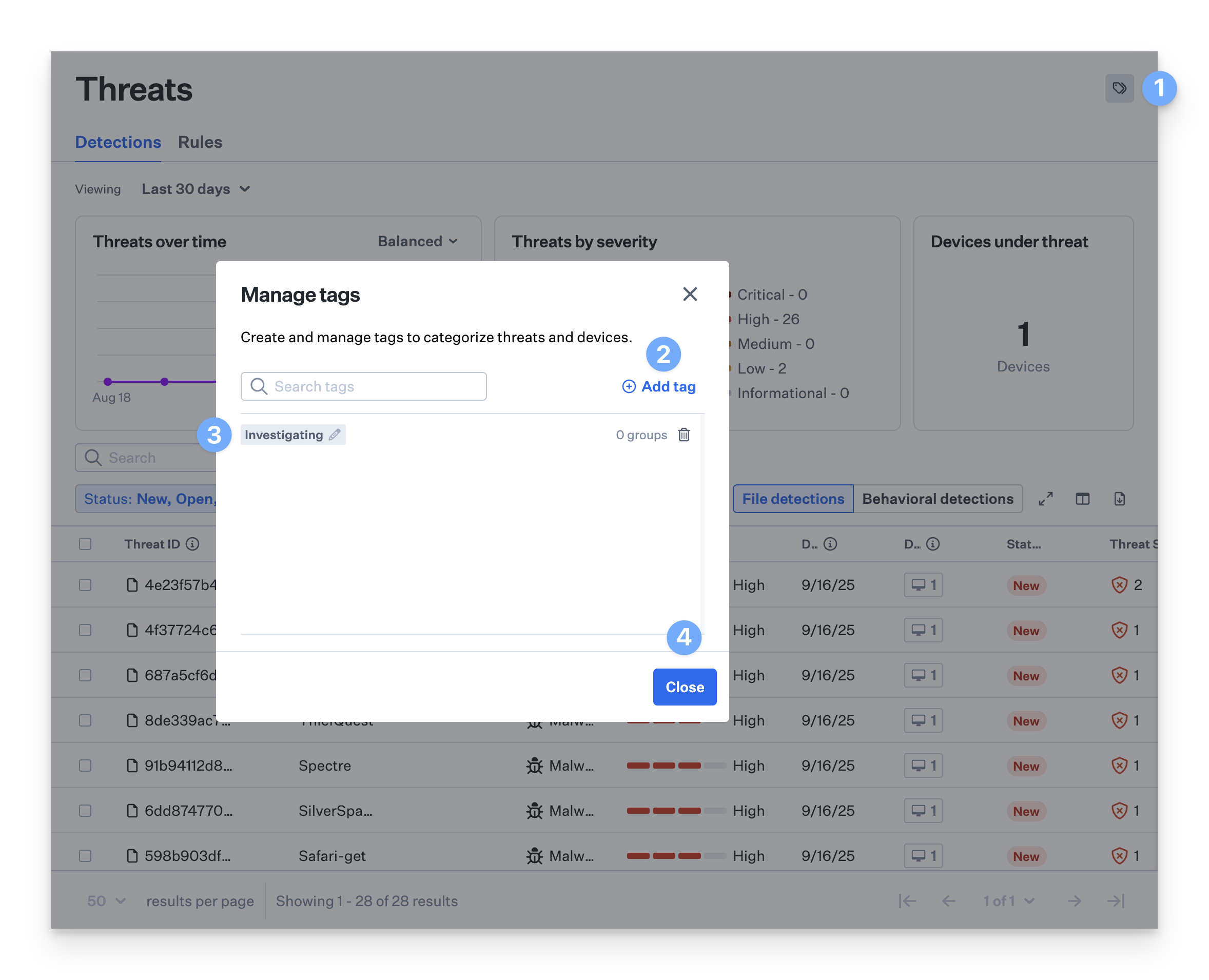
You have full control over your tags. To create, modify, or delete tags, click the Manage Tags button. This allows you to customize and maintain a tagging system that aligns with your team’s operational needs.Access Tag Management
Select the Manage Tags icon in the upper right-hand corner of the Threats page.
Enter Tag Text
Enter your desired tag text. Select the checkmark to save, and repeat as desired for the number of tags you want to add.
Access Tag Management
Select the Manage Tags icon in the upper right-hand corner of the Threats page.
Access Tag Management
Select the Manage Tags icon in the upper right-hand corner of the Threats page.
Assigning Tags to Threats
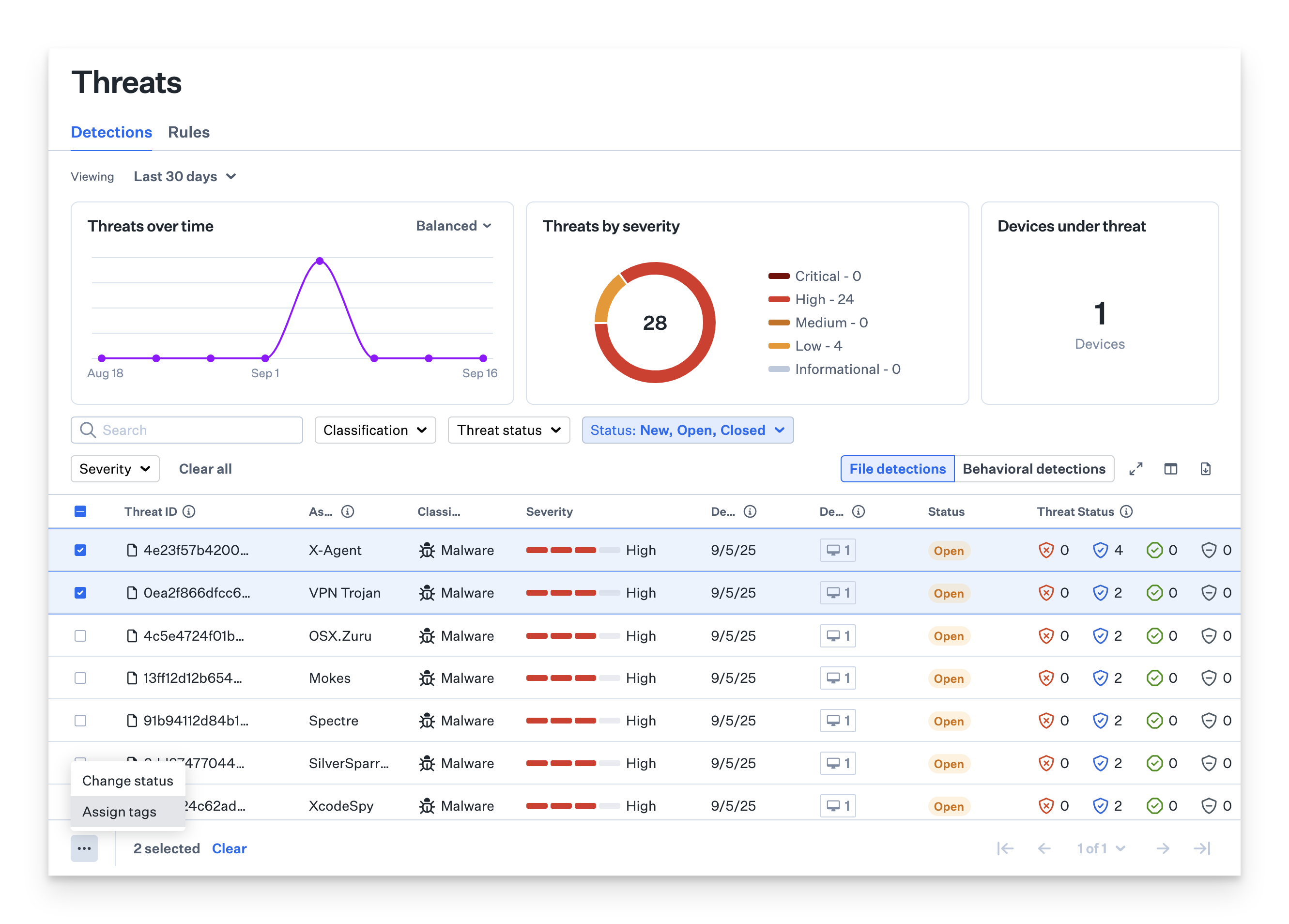
Filtering Threats by Tags
You can filter the threats table by selecting one or more tags from the top filter. This helps you focus on specific types of threats or tasks.Considerations
- Status Management: Regularly update detection statuses to maintain accurate threat tracking and improve filtering effectiveness
- Tag Strategy: Develop a consistent tagging strategy that aligns with your team’s operational workflows and threat classification needs
- Bulk Operations: Use bulk status changes and tag assignments to efficiently manage multiple detections simultaneously
- Filter Combinations: Combine status and tag filters to create focused views for specific threat types or operational priorities
- Team Collaboration: Establish clear guidelines for status updates and tag usage to ensure consistent threat management across your security team
- Automated Statuses: Understand that New and Archived statuses are automatically managed by Iru Endpoint based on timing, while Open and Closed require manual intervention
- Threat Prioritization: Use status and tag combinations to prioritize threats that require immediate attention versus those that can be addressed later





